
The mammoth rise in cybercrime has made organizations revise their application security strategy and implement new techniques to safeguard their software. This is largely because traditional security methodologies, such as Manual Testing and Web Application Firewalls (WAF), have been rendered irrelevant due to evolving hacking techniques. Unlike old times, more and more organizations today are concentrating their efforts towards bolstering the foundation core of their software – the application code. The following 7 development AppSec tips should be adopted by all organizations striving to improve code integrity, and boost the robustness of their web/mobile applications.
1. Plan and create a Software Development Life Cycle (SDLC).
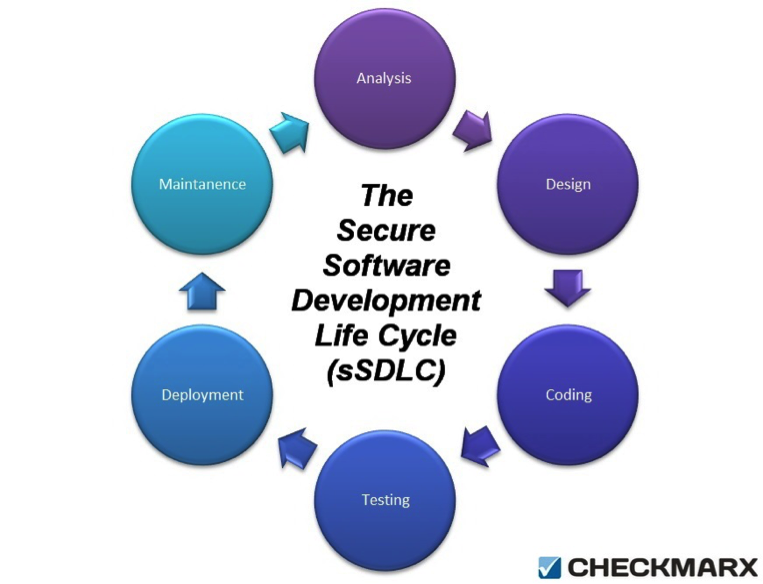
The most effective way to ensure secure development is to devise a Software Development Life Cycle (SDLC), which involves the breaking down of the development process into pre-defined stages with security testing built into each and every one of them. This automation of the testing process eventually leads to the early detection of vulnerabilities. The modern SDLC typically consists of six stages:
- Analysis – This stage involves the establishment of a high-level game plan for the development process, inclduing system analysis, adding of new features and also the tweaking of the development protocol. The data received from the security solution is also taken into consideration and benchmarks are revised accordingly.
- Design – Just as the name suggests, this is where the software design is prepared from the requirement specifications decided upon in the first stage of the process.
- Coding – Here, the developers step in and start writing the application code. The coding stage is typically the longest and most complicated part of the SDLC.
- Testing – The post-build stage is where most QA procedures are executed, along with security testing. However, it's highly recommended to not postpone security implementation and integrate the solution into all stages of the SDLC. This enables the creation of a secure SDLC, arguably the safest development method today.
- Deployment – At the end of the process, the application is basically ready for release. The customers start using the software and implement it in their systems.
- Maintenance – No application is perfect and flawless. Customers report their bug findings and performance issues after using the software. Developers then work on eliminating the problems and fine-tuning the different features of the application, ideally in thoroughly planned sprints (Agile/DevOps).
2. Automate the security process within the secure SDLC.
The most effective way of creating a secure SDLC is to automate the entire security process. When security is built into all six stages above, vulnerabilities are located early. The early detection of loopholes in the application code significantly shortens the remediation process while also saving the organization a significant amount of money and resources. Static Application Security Testing (SAST), most commonly Static Code Analysis (SCA), is usually implemented to achieve these goals. These code scanners can be integrated into all SDLC stages and also have light-weight plugins that seamlessly blend into the developer's IDEs. Other benefits of implementing automated application security testing include:
- Best-fix location functionality, where the most vulnerable junctions are pin-pointed.
- No need for scanning unchanged code, which is ideal for CICD, Agile and DevOps.
- Wide programming language coverage and multiple framework compatibility.
- Detection of coding errors (i.e – buffer overflow), dead code and other flaws.
- Automatic generation of security reports in PDF/XML format for offline scrutiny.
3. Halt the build when medium- or high-level threats are detected.
Regardless of what development environment you are in, you must make sure that you have security thresholds in place. For example, it should be made sure that medium- or high-severity vulnerability detection stops the build instantly until the issue is mitigated. This can be easily implemented by using the aforementioned automated security application testing. See part two here

About the Author: Sharon Solomon (@checkmarx) is a Content Manager at Checkmarx, a leading provider of Source Code Analysis (SCA) solutions to identify security vulnerabilities in web and mobile applications. It provides an easy and effective way for organizations to introduce security into their Software Development Lifecycle (SDLC) which systematically eliminates software risks and coding flaws. Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc. Title image courtesy of ShutterStock

