
John Callahan’s October article “4 Reasons to Get Your Masters in Cyber Security” made me think about how to help students and cyber professionals strengthen a critical soft skill: written communication. Research synthesis and analysis papers are common in academic environments. These critical thinking assignments require students to conduct research on specific topics and use scholarly articles and other authoritative sources to defend a position. In an effort to help others overcome one of the struggles of writing graduate-level research and analysis papers, here are 5 tips to help structure your paper and get an A every time:
- Write a thesis statement for each paragraph. (What point are you arguing?)
- Example: Patching is a major issue due to the frequency with which security flaws are discovered and the potential impact they can have for browsers' functionality, but it is a challenge that can be resolved with technical capabilities.
- Find content from two or more scholarly articles/authoritative sources to validate your point.
- Example: Browser patching frequency is an issue because updates are required to address known flaws that leave companies at risk between patch cycles. For example, Microsoft released several critical patches to address almost 50 weaknesses in the first two weeks of September. Likewise, Adobe released patches to fix 29 vulnerabilities in Flash. Most companies patch on a schedule after testing and validation, leaving those vectors open to exploitation during those windows of opportunity. While patching is important, testing is imperative to avoid unintended change to functionality. Woody Leonhard, a senior editor at InfoWorld, discusses here how one Internet Explorer patch 3146449 lets users “start an upgrade to Windows 10.” This could be problematic if the company’s current standard is Windows 7.
- Write a closing statement that restates or reinforces why those examples prove your point.
- Example: These examples illustrate why patching is a major issue.
- Write a transitional sentence that ties into the previous paragraph while leading into the subject of the next section.
- Example: Although patches fix known issues with browsers, there are some browser problems with no readily available solutions. Browser problems will be discussed in the next section.
- Summarize your key findings.
- Example: This paper evaluated browser attacks, network IDS/IPS, and event analysis. The student used scholarly articles and other authoritative sources to explain how browser attacks work and the function of the identified security technologies. She analyzed issues, discussed problems, and evaluated solutions in each category. Browser attacks can be attributed to vulnerable code on websites. Network IDS/IPS inspects traffic for malicious behavior and responds based on rules in the platform. Event analysis correlates data from multiple sources to tell a story of what happened. Patching is a major browser issue while end users are major browser problems. Recurring problems emerged in the IDS/IPS research: the inability to inspect encrypted traffic, prevent/detect advanced persistent threats, and functionality degradation without proper signatures. Recurring problems emerged in the IDS/IPS research: the inability to inspect encrypted traffic, prevent/detect advanced persistent threats, and functionality degradation without proper signatures. Recurring issues were also observed in IDS, IPS, and event analytics: the ability to respond to voluminous alerts, false positives, and network resource constraints. Solutions to address security issues in all categories include patching, secure configurations, and asset management. After reviewing all of the literature, the biggest takeaway is that all technologies have weaknesses, so a defense-in-depth strategy must be used for maximum prevention and detection.
How This Translates Into Professional Success
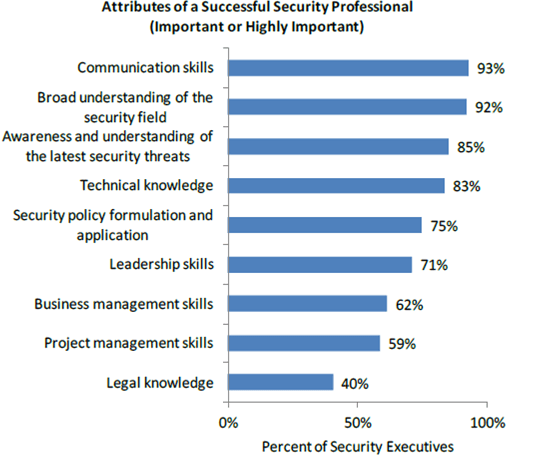
Whether you're a full-time student or student juggling a career, some people have exceptional hard skills (great with tools). However, infosec professionals often struggle with the soft skills that are necessary for success in this field (communication). It is important to note that these soft skills can have a positive (or negative) impact on your career. In fact, 93% of executives surveyed in a recent (ISC)2 Global Information Security Workforce Study cited communication skills as the most important requirement to be successful in security. Therefore, it is imperative that you cultivate that skill set for academic and professional success.
In the workplace, security professionals are required to research and synthesize data for many reasons, including but not limited to:
- Gaining buy-in from management
- Justifying investments in tools
- Providing metrics for different audiences
- Establishing thought leadership
- Creating/maintaining technical instructions
- Developing standards, policies, and procedures
- Producing documentation for auditors
- Negotiating a raise or promotion
- Writing incident summaries
- Delivering gap and risk analysis reports…just to name a few
Specific roles and responsibilities will govern whether you ever have to do any of the work listed above. However, the important thing to remember is that the ability to coherently present synthesized data to defend your position is a critical skill set in professional settings just as it is in school. Technical skills are important, but your communication skills will ultimately be the determining factor in how successful you are in your security career. To summarize: good written communication skills are valuable and can help you succeed in the academic setting and the workplace. Security is generally seen as cost that must be justified or “sold” to leadership. Hence, strong communication skills make you a better salesperson and subsequently will make your security program initiatives more successful. Further, strong communication skills in security can pave the way to other more brand building centric benefits, such as blogging, forum participation, research or other knowledge sharing opportunities. I am paying it forward and hope this article helps you in both environments.

