
Over US $43 billion has been lost through Business Email Compromise attacks since 2016, according to data released this week by the FBI.
The FBI's Internet Crime Complaint Center (IC3) issued a public service announcement on May 4 2022, sharing updated statistics on Business Email Compromise (BEC) attacks which use a variety of social engineering and phishing techniques to break into accounts and trick companies into transferring large amounts of money into the hands of criminals.
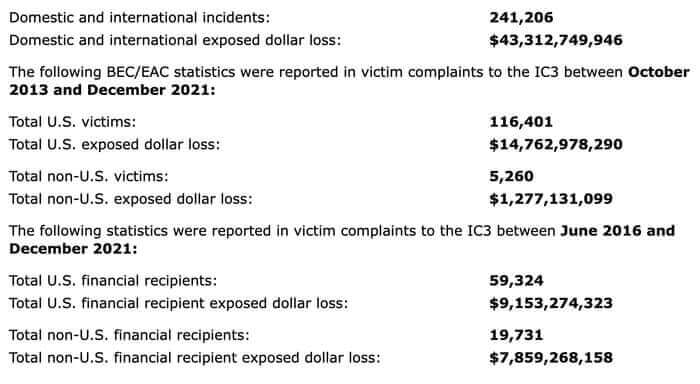
The report looked at 241,206 incidents reported to law enforcement and banking institutions between June 2016 and December 2021, and says that the combined domestic and international losses incurred amounted to US $43.31 billion.
Worryingly, there has been a 65% increase recorded in identified global losses between July 2019 and December 2021. The report suggests that this increase can be "partly attributed to the restrictions placed on normal business practices during the COVID-19 pandemic" with many workers forced to do their jobs remotely.
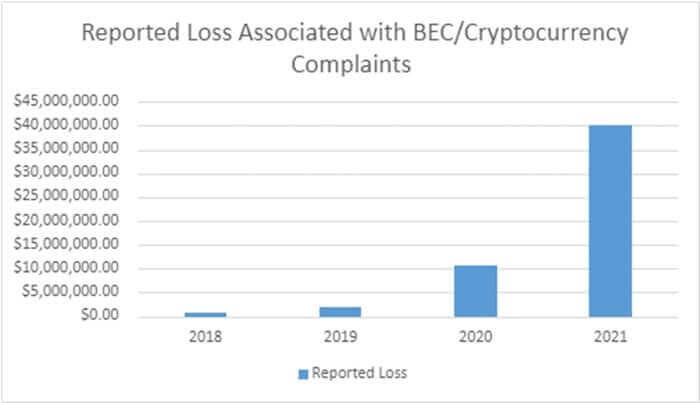
The rise of interest in cryptocurrency has also been seen in the stats, with an increased number of complaints recorded involving digital funds. For instance, the report notes how scammers have used direct transfer of funds to cryptocurrency exchanges (or a "second hop" transfer to a cryptocurrency exchange) in a seeming attempt to anonymise the movement and ownership of stolen funds.
The FBI offers a number of tips to companies wishing to better protect themselves from Business Email Compromise attacks:
- Use secondary channels or two-factor authentication to verify requests for changes in account information.
- Ensure the URL in emails is associated with the business/individual it claims to be from.
- Be alert to hyperlinks that may contain misspellings of the actual domain name.
- Refrain from supplying login credentials or PII of any sort via email. Be aware that many emails requesting your personal information may appear to be legitimate.
- Verify the email address used to send emails, especially when using a mobile or handheld device, by ensuring the sender's address appears to match who it is coming from.
- Ensure the settings in employees' computers are enabled to allow full email extensions to be viewed.
- Monitor your personal financial accounts on a regular basis for irregularities, such as missing deposits.
Organisations are also advised to immediately contact their financial institution should they believe that they have fallen victim to fraudsters, as it may be possible to request a recall of funds. Regardless of the amount stolen, victims of Business Email Compromise are urged to file their complaint at bec.ic3.gov as soon as possible.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

