
Companies are facing increased and complex cybersecurity challenges in today’s interconnected digital economy. The cyber threats have become more sophisticated and may harm a company via innovative new forms of malware, through the compromise of global supply chains or by criminal and hostile state actors. The hard truth is that it is difficult to counter the ever-expanding cyber-criminal economy. Corporations realize that they cannot escape reality nor find a panacea to remove the threats. Becoming a cyber-resilient organization is the only answer to the cybersecurity challenges, whether this involves developing a new culture and mindset or adopting different processes and technology. Those responsible for running the business of cybersecurity in companies and organizations are confronted by new demands driven by the digital transformation of businesses. The facts are indicative of the graveness of the situation. According to the World Economic Forum Global Risks Report 2019, cyberattacks are one of the top 10 global risks of highest concern for the next decade, with data fraud and theft ranked fourth and cyberattacks fifth. Globally, the potential cost of these risks could scale up to $90 trillion in net economic impact by 2030 if cybersecurity efforts fail to keep pace with growing interconnectedness, according to the Zurich Insurance Group. Although there is an abundance of guidance in the cybersecurity community from government and industry standards, including ISO, NIST and many others, the application of this guidance falls short of what is required to ensure effective defense against cyberattacks. As a result, the annual number of cyberattacks globally hit all-time highs every year.
What are the barriers to the adoption of cybersecurity best practices?
It is apparent that current approaches, policies and strategies make it difficult to implement comprehensive best practices across the digital and operating environments in organizations. Security tools and processes are often set up once and then forgotten, becoming outdated and even obsolete in a continuously evolving threat landscape. Systems must be updated continuously to keep pace with the flow of business activities if they are to protect effectively against newly discovered vulnerabilities. Although organizations have a plethora of tools available to automate security tasks, these tools often aren’t integrated in a fully automated fashion. This results in a complex environment of tools, gaps and vulnerabilities which together increase the attack surface rather than mitigating threats due to the inability to deploy a holistic automated approach. Another major challenge is the sheer volume of work involved in following up on security alerts and incidents that cannot be automated. The reliance on humans to carry out security functions, to assess the more strategic implications of alerts and incidents, is mission critical. However, the well-known problem of cybersecurity talent shortage means this capability is often under-resourced. All too often, to face these demanding challenges, organizations need to consider outsourcing some of the more advanced, complex and onerous services to service providers depending on their risk profile to improve their coverage and service level agreements.
10 Tenets for Cyber Resilience in a Digital World
The role of an organization’s cyber resilience leaders is to support the mission of their organization by ensuring that cyber risks are managed at an acceptable level. It is unrealistic for any organization to achieve faultless security. Since no enterprise is immune to cyber threats, organizations need to be prepared for the inevitable, namely, that a breach will happen. Therefore, the end goal of every organization should be resilience, the ability to quickly and efficiently identify and minimize the impact of an incident to allow business continuity as effectively as possible. Having the aforementioned in mind, the World Economic Forum published the “Cybersecurity Guide for Leaders in a Digital World.” The guide bridges the gap between leaders with and without technical backgrounds, and it is intended for senior executives who are responsible for setting and implementing the strategy and governance of cybersecurity and resilience in their organization. Since cybersecurity is everyone’s responsibility in an organization, it is essential that key stakeholders in the C-Suite and other company executive officers understand their responsibilities regarding cybersecurity. The purpose of this guide is to present the key tenets of how cyber resilience in the digital age can be achieved through effective leadership and design. Essentially, the guide offers an excellent cybersecurity playbook for leaders in a digital world. The guide presents and elaborates on 10 tenets based on existing guidance and standards, which are “the fundamentals that an organization must implement in order to embed cybersecurity in the corporate DNA and as part of a comprehensive cybersecurity program in the exercise of due diligence for cyber resilience.” The 10 tenets are the following:
- Think Like a Business Leader to transform cybersecurity from a support function into a business-enabling function, considering that cybersecurity has a direct influence on business reputation, stock value, revenue, brand equity, customer relations and a product’s time to market, among other parameters.
- Foster Internal and External Partnerships. Internal partnerships are required to ensure that business timelines are met while delivering a highly secure and usable product to customers in line with the risk tolerance defined by the organization. On the other hand, external partnerships are important to share information on security-related issues such as threats and best practices to manage the risks associated with cyber threats in a most effective manner. This kind of relationship is built on trust; the more trusted the relationship, the more sensitive the nature of the information that can be shared.
- Build and Practice Strong Cyber Hygiene, because the effective and consistent implementation of strong cyber hygiene could have potentially mitigated the majority of the cyberattacks of the last decade.
- Protect Access to Mission Critical Assets based on the principle of “least privileged access” while building a strong identity and access management system.
- Protect Your Email Domain Against Phishing since email is one of the most valuable and broadly used means of communication and since most organizations strongly depend on it. According to Verizon’s DBIR 2019 report, email is the most common point of entry, with the median company receiving over 90% of their detected malware via this channel.
- Apply a Zero-Trust Approach to Securing Your Supply Chain that does not assume that a company can be made safe and sound within the confines of its own “secure” corporate network. As nearly 50% of companies fail to assess their hardware and software suppliers’ level of cyber risk, a perimeter-agnostic zero-trust approach places control around the data assets themselves and increases the visibility into how they are used across a digital business ecosystem. Cybersecurity is only as strong as its weakest link.
- Prevent, Monitor and Respond to Cyber Threats by developing a robust risk-based approach to measuring risks and responding to cyberattacks that is tailored to the organization’s business context. The security services implemented must be fit for purpose and tailored to the needs of the organization across the dimensions of people, processes and technology.
- Develop and Practice Comprehensive Crisis Management Plan. Crisis management is a critical component of any security program in today’s world. Communicating a security incident in a timely manner is as important as transparency and simplicity to form a solid trusted relationship with customers, shareholders, regulators and other stakeholders.
- Build a Robust Disaster-Recovery Plan for Cyberattacks tailored to security incident scenarios to protect an organization from potential cyberattacks and to instruct how to react in case of a data breach while reducing the amount of time it takes to identify breaches and restore critical services for the business.
- Create a Culture of Cybersecurity which puts users in the first line of defense and recognizes the critical role all employees play in the organization’s security. Keeping an organization secure is every employee’s job.
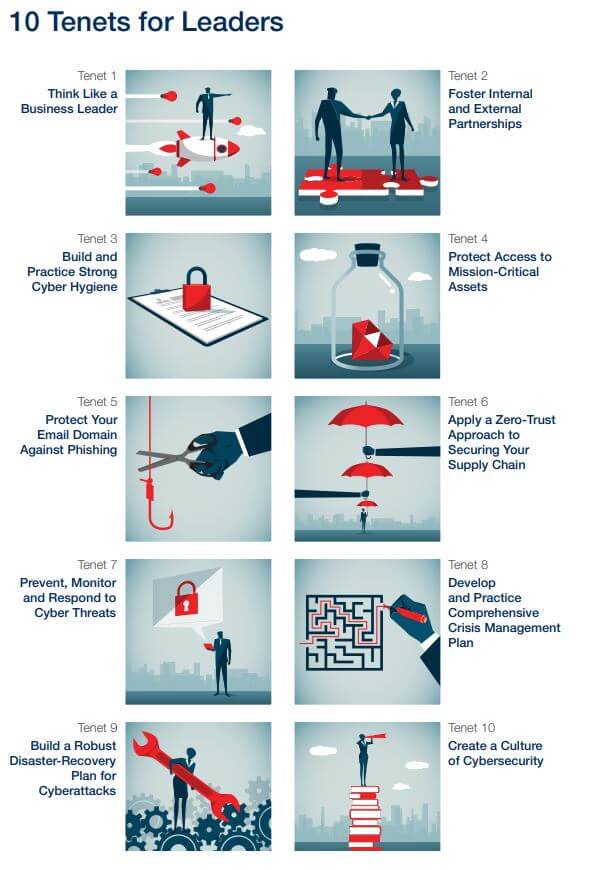
Figure 1: WEF The Cybersecurity Guide for Leaders in Today’s Digital World
What is the most important tenet?
Commenting in the foreword of the guide, Sir Rob Wainwright, Partner, Risk Advisory at Deloitte, Netherlands and ex Europol Director, says that “The recommendation to foster internal and external partnerships is one of the most important.” He explains that “the dynamic nature of the threat calls on us to build a better global architecture of cyber cooperation. Such cooperation should include more effective platforms for information sharing within and across industries.” If you asked my opinion, I would say that the two most important tenets are Leadership and Cybersecurity Culture. The pillars of every successful, effective and efficient organization is leadership and organizational culture. A transformative leader can inspire by his vision and lead, by example. However, a successful cybersecurity strategy and its implementation are dependent on the culture of the organization. Cybersecurity, privacy and digital trust are all based on how well the organization manages to integrate security as an inherent part of its DNA. “The importance of fostering an environment of security and risk awareness, shared ownership of cyber risk and cyber risk resilience is only going to grow. Cybersecurity leaders who are able to step beyond a tactical, technical level are more likely to gain credibility and support among leaders across the enterprise, including the board, C-suite, and business unit leaders,” comments Troels Oerting, Chairman of the Advisory Board of World Economic Forum’s Centre for Cybersecurity. At Tripwire, we strongly believe that cybersecurity is everyone’s job. Cybersecurity responsibilities can’t fall on security teams alone. Contrary to the common misunderstanding, cyber threats aren’t a technology problem looking for a technology solution. The solution is found at the intersection of an organization’s employees, the processes, strategies and best practices promoting a healthy cybersecurity culture and hygiene and the use of proper, orchestrated and updated technology.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

