
Many of the breaches of the past ten years have taken advantage of weak or nonexistent security settings. Conversely, for example, companies that configured their Docker application to the CIS recommended security settings for container users and privileges were not as vulnerable to container escape exploits. Arguably, a configuration change prevented many breaches. Security configuration management can make a huge difference in reducing an organization’s vulnerability.
As stated in a previous post:
“As a multi-faceted topic, hardening may overwhelm organizations when designing or amending their security strategy. There are different types of hardening to be aware of, which can be broken down into five key categories.”
Configuration hardening is one of the five types of hardening that are vital to a secure environment.
Customization with SCM
What is SCM, exactly? Security Configuration Management (SCM) is the process of going through your systems’ settings and making sure they are arranged in the most effective way to protect the environment. Every operating system and software product has anywhere from several to thousands of options for how they can behave in different circumstances.
Tripwire Enterprise (TE) offers many benefits for organizations that seek to improve their security. One benefit is the policy reports feature. Policy reports in TE can be customized, enabling you to include just the hardening tests that you want to enforce easily. For example, the report shown in the following image will only show the sections and tests displayed. If those are the configurations that must be set for the environment, it will display the results of just these tests and not the entire NIST or CIS standard:
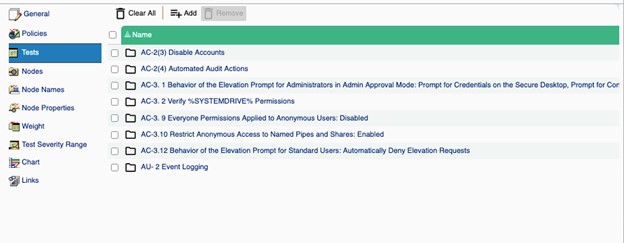
This level of compliance is achievable and absolutely necessary. The first thing I tell my customers is to consider following the CIS or NIST sections on audit configuration. Turning on the audit settings so that you’re logging all types of access activity and changes to security settings and other system activity gives you the best chance of being alerted to unusual activity. If you don’t turn on the audit settings (and many of them are turned off by default on Windows and Linux systems), you’re blind to what is actually happening on those systems.
NIST SP 800-53 includes a section named “Auditing and Accountability (AU)” and under that section, “AU-2 Event Logging”. There are configuration settings for system auditing that should be checked and configured as recommended. For the CIS Hardening Standards, section “17 Advanced Audit Policy Configuration” has similar advice, which is then broken into several sections for event types.
The settings for Auditing should all be followed. These are the simplest and most basic settings of configuration hardening because the changes don’t block anything from running and turn on the eyes of the system, so you can now see what’s happening. Yes, having all of the recommended audit settings turned on adds some system load, and years ago, this was a real concern because the logs were kept locally.
But today, you should be sending all logs off-system as soon as they are generated, which can keep the log size smaller so you’re not filling up your local disks. The ability for TE to review the configuration settings and the system’s ability to send events to an external logging system nullifies the old reasons for not logging events.
You can configure your Tripwire Policy Compliance reports to include just this section and ensure your systems show up as “Green” for audit settings.
More customization for your SCM reports
The next phase of customizing your SCM reports would be to apply the “Access Control” sections of NIST 800-53 or the “Account Policies” section of CIS. You can review which of these settings are mandatory for your environment and include those in your reporting.
There are basic settings to apply in this section of the specifications as well, such as renaming the system Guest account, renaming the default Administrator account, and inactive account checking. Others may require a decision based on how you administer your systems, such as “Behavior of the Elevation Prompt for Standard Users.” The secure action to take is to set that to deny all requests. Any users who can work as administrators should already be in an administrative group that allows them to do their job. But if you have an old process that relies on elevating itself, turning this on could break that process. So, you could need to exclude that check or if you do want to track and document the reason for the exception, create a waiver in TE for that test.
Beyond the basic settings, which will not affect system performance, the next step in customizing SCM is testing any changes that might adversely impact system behavior before engaging them in your production environment. Add configuration settings to the reports to enforce compliance after testing them in your Dev/Test environment. Adding more compliance tests over time is something you should strive for as well.
Sometimes, the effort to harden a system for security and compliance can seem so overwhelming that it seems impossible. However, hardening is such an important part of your security practice you don’t want to let the size of the task prevent you from getting started.
With Tripwire Enterprise and SCM, the ability to make your systems secure while also adhering to best practices and regulatory requirements becomes much easier.
Contact us to see how configuration management can make security easy.
Tripwire Enterprise: Security Configuration Management (SCM) Software
Enhance your organization's cybersecurity with Tripwire Enterprise! Explore our advanced security and compliance management solution now to protect your valuable assets and data.

