
The importance of a mature vulnerability management program can’t be overstated. File integrity monitoring (FIM) and security configuration management (SCM) might be the bedrock of a strong cybersecurity program, but they can only go so far. Scanning for vulnerabilities needs to be a foundational part of your program, too. The Center for Internet Security (CIS) already knows this; that's why it ranks continuous vulnerability management (VM) as number three in its top six basic security controls.
"Organizations that do not scan for vulnerabilities and proactively address discovered flaws face a significant likelihood of having their computer systems compromised."
— Center for Internet Security (CIS)
Threat Detection and the Growing Cybersecurity Skills Gap
But as crucial as VM is, security teams are having a harder and harder time filling the roles and securing the budget necessary to establish a mature VM program. Security professionals are put in a difficult position when they know what they should be doing, but they just don’t have the resources to do it.
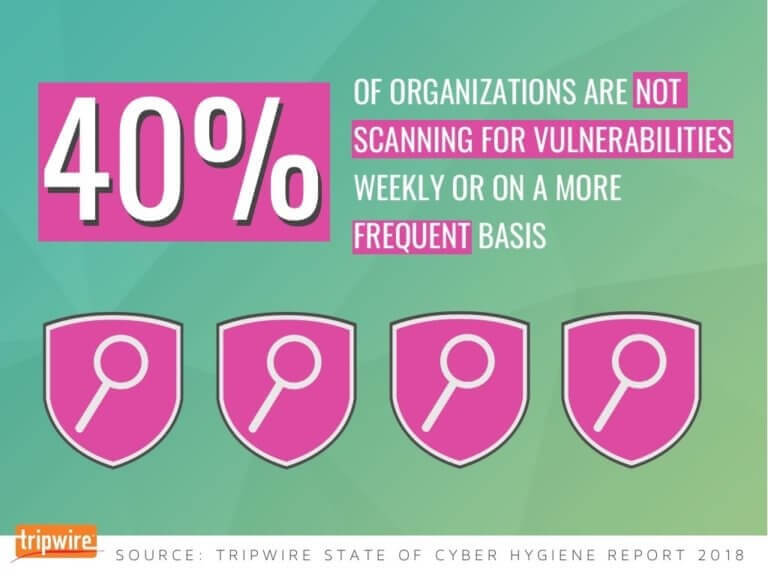
There simply aren’t enough cybersecurity professionals to meet industry demand. And due to the shortage of cybersecurity talent, many organizations may skimp when it comes to VM. According to CSO, 53 percent of organizations claim a “problematic shortage of cybersecurity skills.” While some VM effort is better than none, any lapse in continuous monitoring is an opportunity for cybercriminals to impact your network. A Tripwire study found 93 percent of security professionals are concerned about the cybersecurity skills gap, and 72 percent believe it’s more difficult to hire skilled security staff to defend against today’s complex cyber attacks compared to two years ago. In addition, 81 percent believe that the skills required to be a great security professional have changed in the past few years.
“The skills gap doesn’t have to be an operational gap. Security teams shouldn’t overburden themselves by trying to do everything on their own. They can partner with trusted vendors for managed services or subscribe to service plans where outside experts can act as an extension of the team.”
— Tim Erlin, Tripwire VP of Product Management and Strategy
Vulnerability Management Goes Beyond Compliance
Another common issue arises when organizations view their VM program as little more than a means of achieving regulatory compliance. VM programs that aren’t far along in their maturity will often frame VM as a compliance hurdle rather than an essential security practice. This is just one of many rampant misconceptions about VM. This perspective can hinder VM programs from developing and maturing from a security-centric mindset. Complex attack surfaces call for VM programs that are expertly handled—to go beyond ticking an auditor’s checkbox.
More Organizations Are Turning to an MSSP
Managed security service providers (MSSPs) are one-way organizations can protect their data without needing to hire additional hard-to-find cybersecurity professionals. When you choose the path of cybersecurity as a managed service, pay attention to the credentials of the team that will be running your vulnerability management processes for you. At Tripwire, managed services are executed by experts relying on the Tripwire Vulnerability and Exposure Research Team (VERT). VERT works to continuously keep organizations armed with the most accurate, relevant, and up-to-date threat defense intelligence. Tripwire has a range of managed cybersecurity services for organizations to choose from, the newest being Tripwire® ExpertOpsSM VM. It uses advanced analytics and a unique quantitative scoring algorithm based on several factors—including the ease and impact of exploit—to prioritize vulnerabilities for remediation.
Vulnerability Management as a Cloud-Hosted Service
Tripwire ExpertOps VM combines managed services with the industry’s best vulnerability management solution so you can focus your remediation efforts on the highest risks and the most critical assets. The solution provides both personalized consulting and cloud-based infrastructure and is easy to deploy and use, with simple subscription pricing and low total cost of ownership. Managed by experienced Tripwire engineers, Tripwire ExpertOps VM gives your organization highly-accurate and granular vulnerability assessment results to help you focus your remediation efforts on the highest risks on your most critical assets. Customers regularly receive expert guidance to ensure that their environment is secure and that critical vulnerabilities are remediated. Tripwire’s vulnerability management solution has the industry’s most granular risk scoring available in addition to the lowest false positive rate: 0.02 percent.
Key Benefits of Tripwire ExpertOps VM
- Simple subscription for best-in-class VM
- Comprehensive discovery and profiling of all network assets
- Protect the increasing numbers of hosts and vulnerabilities on your network
- Identify top risks using advanced vulnerability scoring algorithm and prioritization
- Tailored advice, incident assistance and audit support related to Tripwire findings
- Avoid delays, missed threats and vulnerabilities
- Maximize limited human resources while improving security operations
- Cloud-hosted infrastructure combined with consulting services
Ready to learn more? Download the Tripwire ExpertOps VM Services Brief.
Tripwire ExpertOps
Elevate your organization's cybersecurity with Tripwire ExpertOps! Explore our managed security service now to ensure round-the-clock protection and expert guidance in safeguarding your digital assets.

