In the modern digital landscape, cybersecurity is paramount, making the differentiation between vulnerability scanning and penetration testing essential for safeguarding organizational assets. Vulnerability scanning offers a broad sweep for potential security weaknesses, serving as an early warning system. Penetration testing takes a more targeted approach, exploiting vulnerabilities to understand the real-world effectiveness of existing security measures.
Both practices are cornerstone elements of a comprehensive security framework, ensuring that defenses exist and are effective against sophisticated cyber threats. This guide delves into how these critical security methodologies complement each other in bolstering an organization's cyber resilience.
The Crucial Roles of Vulnerability Scanning and Penetration Testing
Vulnerability scanning and penetration testing are two sides of the same coin in cybersecurity defense strategies. Vulnerability scanning is an automated process designed to identify and report potential exposures in a network's security before they can be exploited. It acts as a preventive measure, scanning systems for known vulnerabilities and helping prioritize them for remediation based on their severity.
On the flip side, penetration testing is a more hands-on, simulated attack that seeks to exploit vulnerabilities, mimicking the actions of potential hackers. This approach tests the effectiveness of an organization's security measures in a controlled environment, providing a deeper insight into potential weaknesses. Both methods are essential for thoroughly understanding and managing cybersecurity risks, each serving a unique purpose in protecting digital assets.
Penetration Testing
Penetration testing can reach far into an organization’s environment, both technically and physically. One of the most important pre-engagement steps for a penetration test is to consider and agree on the scope of the test carefully. The various tests can extend far beyond the IT or the information security teams.
Physical security testing is perhaps the most dangerous exercise, and it is vital to have fully documented C-Level support. Whether the physical perimeter is being tested or the goal is to prove that a person gained full access to office space, the stakes can become highly hazardous if not carefully scoped. This can prevent any unintended consequences.
Technical penetration testing is equally fraught with risks to the tester. An innocently misdirected port scan can result in the tester running afoul of both State and Federal laws, such as the Computer Fraud and Abuse Act (CFAA, 18 USC 1030), which makes it a crime to access or attempt to access a computer or computer network without authorization or over authorization. Penetration testing can also involve varying levels of notification to those impacted.
Testing can involve the entire infrastructure or be conducted at an application or a particular network segment. While time and cost are usually strong determinants of an organization's choice, it is always best to use a risk-based approach. This ensures that the correct assets are being tested for the correct reasons.
Vulnerability Scanning
Vulnerability scanning identifies potential susceptibilities in network devices such as firewalls, routers, switches, servers, and applications. Vulnerability scans can be automated, making the task easier to scope and safer for the tester. Acting as a detective control, it seeks to identify, without exploiting, any of the discovered vulnerabilities. However, just because a scan can be automated does not make it peril-free.
A poorly planned scan can be as disruptive as an outright attack. Sometimes, scoping a vulnerability scan project can often be a time of discovery. Many processes and other tasks, such as bank transfers, backup jobs, and production rollouts, occur outside normal business hours. These mission-critical functions cannot be interrupted. Vulnerability scans can be run more frequently on any number of assets to verify that levels are consistent with the organization’s risk appetite.
Integrating Vulnerability Scanning and Penetration Testing into Your Cybersecurity Strategy
Strategic integration of vulnerability scanning and penetration testing forms the backbone of a resilient cybersecurity defense. By routinely conducting vulnerability scans, organizations can maintain a vigilant stance against emerging threats, systematically identifying and addressing potential security gaps. Complementing this, penetration testing offers deep insights through simulated cyber-attacks, testing the real-world efficacy of security measures.
These methodologies enable a dynamic, responsive security posture that adapts to new vulnerabilities and evolving attack vectors. Implementing a cyclical process of scanning, testing, and remediation ensures that cybersecurity defenses meet current standards and are primed to respond to future challenges, safeguarding critical assets in an ever-changing threat landscape.
Review, Remediate, and Mitigate – Then Begin Again
Once all the testing and scanning are complete, the most important task is to review the results with the test subjects and the organization's senior management. No matter how plain the report's language may seem, restating it in language for a non-technical audience is important. The report should be converted into a grid that shows the finding, severity, remediation steps, mitigation steps, task owner, and deadline. This is where collaboration with the project management team becomes important to success. Without a formal project manager, a spreadsheet can fulfill this purpose.
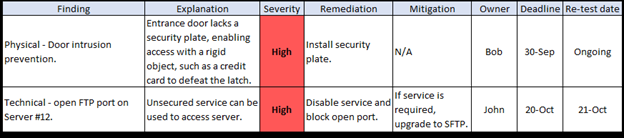
One of the most important columns to include in the grid is one that indicates a testing date after the initial correction of the problem and a periodic retesting schedule. This serves two purposes. First, it decreases the likelihood of the problem recurring and acts as evidence of a repeatable and managed security approach.
Most industry guidance and regulations either suggest or prescribe security scanning and testing. Whether your organization follows the Center for Internet Security (CIS) Controls, NIST guidance, or must adhere to any of the enacted cybersecurity and privacy regulations, the need to continually evaluate security is ever-present. Ensure that penetration testing and vulnerability scanning are a regular part of your organization’s security practice.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

