
Digital fraudsters are using compromised servers and bogus links in an ongoing effort to target LinkedIn members with scams. The scam began when a Sophos employee received what it appeared to be an unexceptional email from someone they know in real life and with whom they keep in touch on LinkedIn. The body of the LinkedIn message informed the recipient that they had a document hosted through OneDrive awaiting them. The attack message didn't provide any information about the document's contents, but it did use the text "www.businessingith" at the start of the embedded link to try to create an air of professional legitimacy.
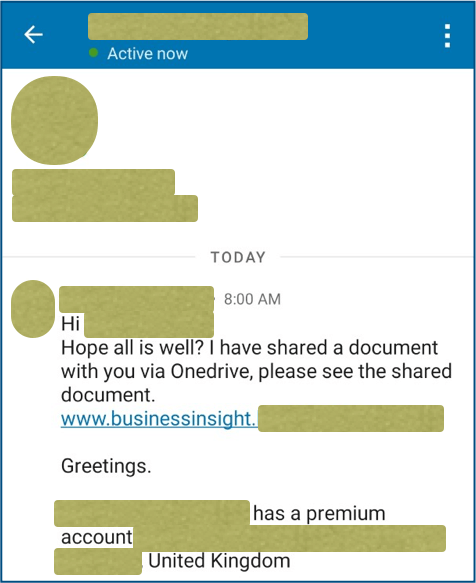
The suspicious LinkedIn message received by the Sophos team member. (Source: Sophos) Immediately, the team member was suspicious that their LinkedIn connection had used their full name and not the shortened name by which they regularly go by. This suspicion was well-founded, as it turned out. Indeed, the embedded URL might have began with "www.businessinsight," but its second half contained the name of someone else's website--specifically, a U.S. entertainer's website whose web server suffered a compromise. Clicking on the link spurred the campaign to use a redirection script, thus diverting the request to a second server in Mexico that maintained a valid HTTPS certificate. This action landed the user on a page whose URL ended with "/office365," which would suggest it was a phishing landing site page at one time. In this case, however, the page simply displayed a 404 error message in Spanish. Curious, the Sophos team decided to append related text to "www.businessinsight." They found a number of subdomains that all redirected to different "dating portals" using the same PHP redirection script as the one they uncovered on the U.S. entertainer's website. The purpose of many of these pages was to trick users into handing over their payment card credentials, but some were after users' online passwords. Paul Ducklin expanded upon the impact of this discovery in an article for Naked Security:
By redirecting only URLs that the entertainer himself didn’t intend to serve up, and thus wouldn’t know to look for, the crooks made sure that that the original web pages continued working just fine, so neither he nor his customers would see anything unusual. Nevertheless, the redirection script provided the crooks with a general-purpose mechanism for running a range of different spamming, phishing and scamming campaigns at the same time, with the target site determined by the URL that the crooks used each time.
This latest scam highlights the importance of LinkedIn users taking steps to protect themselves against ruses sent through the social networking site. This resource can help them defend against some of the most common scam variants.

