The most successful phishing attacks are those that combine technical expertise, e.g., the ability to spoof an email so it appears credible, with a little bit of online research such as identifying employees and their roles in the company. So, how can companies protect themselves against this type of attack?
The first thing is to understand that scammers can be extremely sophisticated and that any company may be vulnerable to this type of attack. Sometimes, it is hard to tell if an email is genuine. Second, appreciate that human factors are frequently exploited when it comes to phishing emails.
Let’s examine a couple of real-life case studies to show how scammers may target businesses using phishing emails.
-
Image
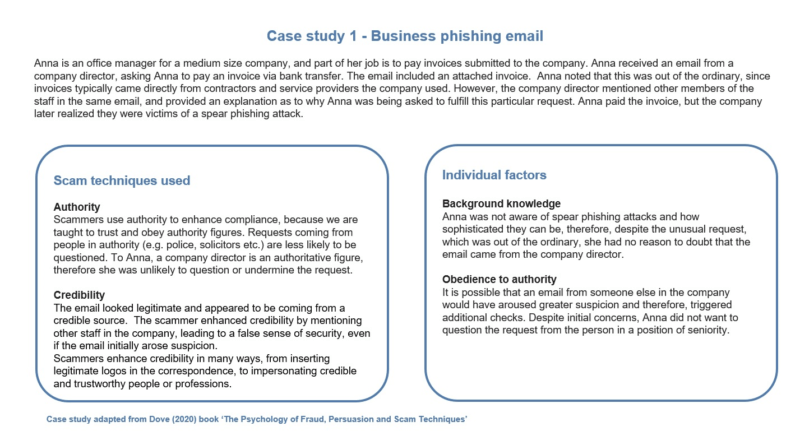
In this example, scammers used the technique known as evoking authority by pretending to be the company director, who has authority over Anna. This is a very common technique used in many scams and frequently in phishing scams sent to businesses. It is effective because many people shy away from openly questioning the motives or actions of those who are in a position of authority. At work, this may include managers, company directors, or leaders. In other contexts, this may include police, legal professionals, or doctors. People who tend to obey authority figures will be especially vulnerable.
However, not all fraud attempts of this kind result in victimization. Below is another real-world yet contrasting example. The techniques used are slightly different but no less effective.
-
Image
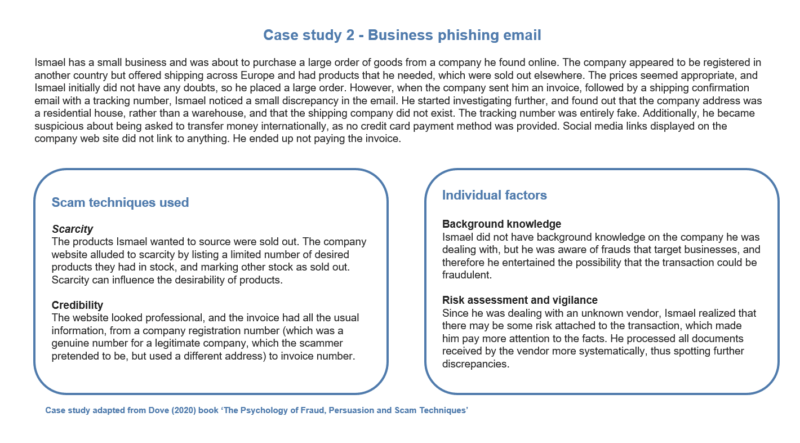
Unlike Anna, who was not fully aware of how realistic phishing emails can be, thus resulting in a low level of vigilance, Ismael was cognizant of impersonation scams and was more suspicious. This increased his level of vigilance and assessment of the risk, prompting him to look a bit more closely at all the documents sent by the company he was buying from. Looking carefully through this, he spotted inconsistencies, which he investigated and which resulted in more suspicion and eventual avoidance.
These examples show that fraud awareness can be complex. Sometimes, one factor can influence another factor, and this can result in greater susceptibility or avoidance. To avoid these types of scams, it is important to appreciate that we often act based on previous experience as well as our human characteristics (personality, beliefs, and heuristics). Understanding how scams manipulate these factors can influence certain fraud outcomes.
More articles that may interest you:
Protecting a New Vulnerable Population on the Internet
Protecting the New Most Vulnerable Population – The Grandparent Scam
Protecting the New Most Vulnerable Population – Subscription Scams
more from Martina Dove
Top 5 Scam Techniques: What You Need to Know
How Social Norms Can Be Exploited by Scammers on Social Media
Data Breaches: A Chance for Opportunistic Scammers & What You Should Watch for
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

