The next item to tackle is the overall security architecture – and this includes several things. But let me first state the disclaimer that of course it is imperative that the correct governance and policies are in place and that technology can’t replace those things.
But, it is also clear that however sophisticated, no paper document or process design will block an attack in the meantime until you have both the supporting policies and the enforcing technologies set up.
It is therefore – as a reality check if you want – necessary to take care of the very basic things, to have the long standing “perimeter” (this is the “outer wall” so to speak, the common (logical) border line around your company’s infrastructure and network, the “first line of defense”) in place, and a few other common necessities such as antivirus filters, intrusion prevention, secure browsers and a SIEM (Security Information and Event Management) system as well.
Here is why: No matter what kind of business you have, no matter how sophisticated your processes and products are – your company most certainly will have a network using TCP/IP (TCP/IP: Transmission Control Protocol / Internet Protocol, both together are used ubiquitous in today’s internet infrastructure), it will exchange files with 3rd parties (inside and outside the perimeter), and it most likely will use the security-prone MS Windows products (at least at the user client side).
So you don’t need to wait for any time-costing BIA or security audit (both are nevertheless indispensable though!), it is a matter of fact that you need “a” firewall (for the perimeter, I explain the “a” later), an AV solution, an IPS (prevention, not detection), and a secure browser as today’s most used interaction tool with the outside (and inside) world.
Finally, the SIEM solution will provide you with the needed visibility into your network, and it will (if configured and managed properly) help you to discover unwanted traffic (or behavior) and to develop the awareness and later the strategy of what needs to be addressed and why.
So what I am telling you here is that you should not do it strictly “by the books” and wait for the BIA and other great analysis work to be done, but instead insist on having “a :=” state of the art firewall solution in place, and should you not have one, get one now!
Talking about firewalls, I want to make it very clear once and for all: a network switch or router is a network switch or router and is NOT TO BE USED as a firewall, regardless of what the vendors will tell you. Keep this in mind, and make sure this is understood by any network administrator in your company. Make sure that the security tools are not in fact operated by network folks but instead by security folks reporting to you and not vice versa.
That doesn’t mean that you cannot, in addition, use a TCP/IP filter on your router or a “personal firewall” on your endpoint device – but those cannot be your single points of failures, as you will need the “in-depth” perimeter firewalls nevertheless.
An additional benefit of Next Generation Firewall solution is its integration of the IPS and a couple of other filters (even malcode:=”malicious code”, this is all kinds of code with a malicious purpose against you) as well, so you can simplify and consolidate some of the most necessary security functions in this choke point.
Make sure though that you have its logs reported into your SIEM solution to get the security cockpit / dashboard informed about their blockings and effectiveness.
In case your company uses outdated browsers on the client-side, make sure these also get upgraded as soon as time allows. This will ensure that the most used (and therefore most attacked) interface to the Internet (and intranet, but the first one is where most of the attacks are coming from) is secured as much as possible – this will “strengthen” (to some extent) your perimeter approach.
It can also have the nice side-effect to increase productivity in your company, depending on your browser usage and business type. With one of my previous employers I helped them to save ~$6.5 million per year just by upgrading the browser and increasing productivity / speed of their call center agents (see also see also chapter 21 “Building ROIs”). Not a bad thing to build your creditability at the C-level.
Once you have the most basic security technologies in place, and meanwhile hopefully your BIA and process analysis done, you should now have an idea what additional risks and areas of concern are out there in your realm. So you then need to develop a security architecture that addresses these findings per design.
A few suggestions are:
- A network separation (i.e. a separate administration network), a separate development (and test) network from production,
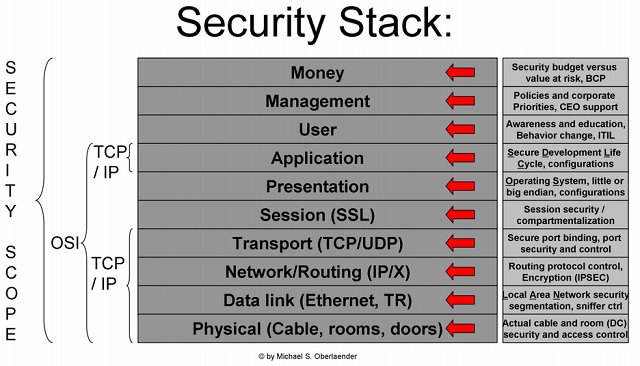
- A multi-tier security in-depth approach (each layer of the TCP/IP model needs to have at least one security mechanism in place – see also chapter 20 “Strategy Development” and Figure 2: Security Stack),
- A hardened operating system,
- A compartmentalized virtualization environment,
- Secured collaboration tools,
- And certain security tools at the client side readily available, such as providing usable encryption (confidentiality), hash controls (integrity) and backups (availability).
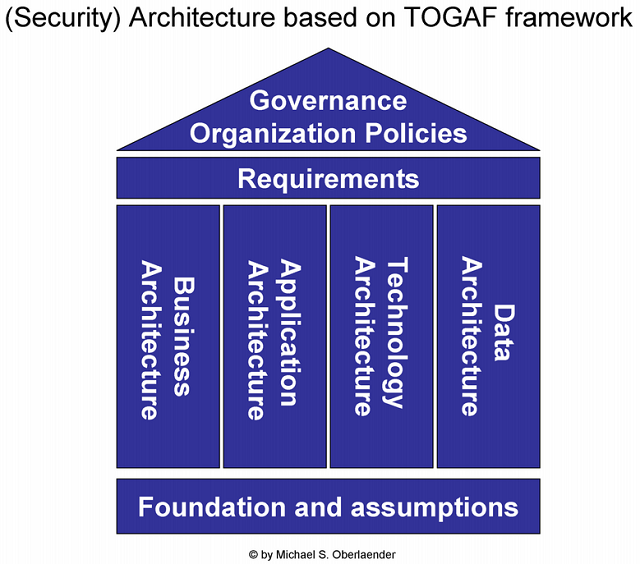
There is certainly more than this, but it really depends on your specific situation and environment, and the BIA should help you to develop your business case for that. A good idea is to use the TOGAF reference model to define your overall enterprise (security) architecture and build in security from the ground level
(Security) Architecture Based On TOGAF) and covered by adequate and accompanying policies:
About the Author:
Michael S. Oberlaender (@MSOberlaender) is a world-renowned security executive, thought leader, author and subject matter expert and has worked in executive level security roles (CSO/CISO) both in the US and EU (Germany) and in IT for over two decades. Most recently he has been serving as Chief Security Officer for the largest European cable network provider (Kabel Deutschland AG) in Munich, Germany and before served as Chief Information Security Officer for FMC Technologies Inc, a leading oil field services and engineering company in Houston, TX. Prior he was the Global IT Security Manager for Heidelberg Americas, Inc. in Atlanta, GA – the US subsidiary of Heidelberger Druckmaschinen AG -the world leader in printing press manufacturing. Before that he worked several years as Project Leader Security and Networks with Suedzucker AG in Mannheim, Germany, the world market leader in sugar and Europe’s largest food company where he has planned, built and run their complete Internet binding and DMZ solutions. He has more than two decades professional IT experience and is a member in good standing of (ISC)², ISACA, InfraGard, and several industry associations and is certified CISSP, CISM, CRISC, CISA, ACSE, and GSNA (all current and in good standing). He holds a Master of Science (Physics) from the University of Heidelberg, Germany. Michael is dual citizen (US and German) and speaks fluent English, German, fair French, and continually learns Spanish. When he is not at work, at conferences, chapter meetings, crises managing or otherwise busy, he enjoys time to relax with his family. Michael is also the author of C(I)SO – And Now What?: How to Successfully Build Security by Design, which is available at CreateSpace and Amazon, and from which the above article has been extracted from with his permission.
Building a Mature Vulnerability Management Program
This guide was written by CISSP-certified Tripwire system engineers with extensive experience in implementation of vulnerability management programs.

