
Building the Case for IoT Security Framework
The Internet of Things (IoT) is growing in technical, social, and economic significance. ENISA defines the increasingly complex IoT systems as “cyber-physical ecosystem[s] of interconnected sensors and actuators, which enables intelligent decision making.” These technologies collect, exchange and process data in order to dynamically adapt to a specific context, transforming businesses and the way we live. Nevertheless, IoT poses some very important safety and security challenges that need to be addressed for IoT to reach its full potential. As we become increasingly reliant on intelligent, interconnected devices in every aspect of our lives, the billions of “things” can be the target of intrusions and interferences that could dramatically jeopardize personal privacy and threaten public safety. Therefore, the main areas of concern regarding IoT that require to be addressed are security and the paramount need for safety since both issues are tightly related to the physical world. The protection of IoT deployments depends on protection for all of the systems involved: the devices themselves, cloud backend and services, applications, maintenance and diagnostic tools, etc. The scale and the heterogeneity of IoT implementations present threats and risks that are manifold and are evolving rapidly. The IoT threat landscape is extremely wide, especially if we consider the impact that attacks may have on citizens’ health and safety. More specifically, IoT devices can be used as an attack vector against critical infrastructures, causing disruptions or, even worse, causing damage that could endanger a country’s social tissue. IoT also presents a great risk to privacy as it is heavily based on the gathering, exchange and processing of large amounts of data from a variety of sources. This sometimes includes sensitive data, which is collected and processed using methods that may be unclear to the users. Due to the characteristics of IoT deployments, new security challenges are emerging. Applying horizontal security controls to such a diverse ecosystem can be a complex and daunting task. For each IoT environment (e.g. Smart Homes, Smart Cities, Smart Cars or ICS/SCADA), it is necessary to carry out a risk assessment to determine the threats that can affect the different assets, define the plausible attack scenarios, and put them in the context of the IoT service to figure out which hazards are critical or not and which ones can be mitigated. Beyond technical security measures, the adoption of IoT has raised many new legal, policy and regulatory challenges which amplify the technical challenges. The rapid change in IoT technology has forced legislators to adapt to the ever-changing environment. For example, during the last years, the European Commission has been working to facilitate the implementation of IoT in Europe by adopting a set of supporting policy actions and launching a series of relevant initiatives. The goal is to build greater EU resilience to cyber-attacks, improve detection mechanisms and strengthen international cooperation. For instance, the EU Cybersecurity Strategy encourages the adoption of “security by design” through the whole lifecycle of IoT devices. On the other side of the Atlantic, the “Internet of Things (IoT) Cybersecurity Improvement Act of 2019” seeks “[t]o leverage Federal Government procurement power to encourage increased cybersecurity for Internet of Things devices.” Furthermore, since IoT solutions are developed with specific technologies and focus on specific applications, they lack standardization, which results in fragmented and heterogeneous architectures. When developing the Baseline Security Requirements for IoT, ENISA identified and studies manifold IoT architectures from agencies such as the European Commission Alliance for IoT Innovation to NIST, ITU, ISO, ISACA, IEEE and others. These challenges need to be addressed to ensure user trust and confidence in the Internet, connected devices, and related services. It is apparent that organizations need clear guidance to identify appropriate security controls and allocate them to specific components within their system. Under this scope, NIST has developed NISTIR 8228, Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks, while ENISA published the Baseline Security Recommendations for IoT. In tandem with these agencies, the Cloud Security Alliance (CSA) published in 2019 its IoT Security Controls Framework and its accompanying Guide.
The CSA IoT Security Controls Framework
The CSA IoT Security Controls Framework introduces the base-level security controls required to mitigate many of the risks associated with an IoT system operating in a range of threat environments. Created by the CSA IoT Working Group, the framework together with its companion piece, the Guide to the CSA IoT Security Controls Framework, provide organizations with the context in which to evaluate and implement an enterprise IoT system that incorporates multiple types of connected devices, cloud services, and networking technologies. While the framework helps users identify appropriate security controls and allocate them to specific components within their IoT system, the Guide to the IoT Security Controls Framework provides instructions for using the companion CSA IoT Security Controls Framework spreadsheet. This guide explains how to use the framework to evaluate and implement an IoT system for your organization by providing a column by column description and explanation. Utilizing the framework, user owners will assign system classification based on the value of the data being stored and processed and the potential impact of various types of physical security threats. Regardless of the value assigned, the framework has utility across numerous IoT domains from systems processing only “low-value” data with limited impact potential to highly sensitive systems that support critical services. The figure below details the flow that users of the CSA IoT Security Controls Framework should follow as they assess and then implement security controls for their unique environment. The circled letters in this illustration correspond to columns in the framework.
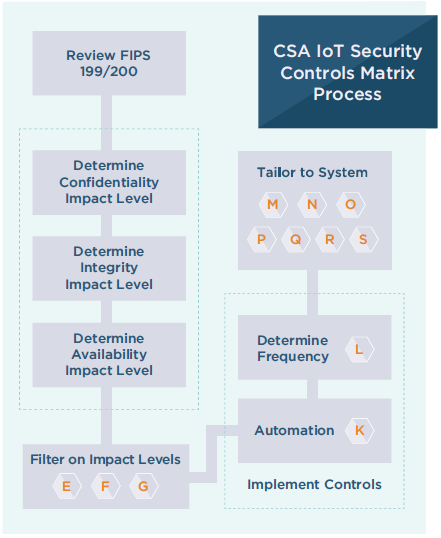
Figure 1 - CSA IoT Security Controls Framework flow According to the Guide, the first step before using the CSA Framework is to review two U.S. Department of Commerce publications: “Standards for Security Categorization of Federal Information and Information Systems” (FIPS 199) and “Minimum Security Requirements for Federal Information and Information Systems” (FIPS 200). FIPS 199 and 200 categorize risk impact levels as Low, Moderate, or High in three areas: Confidentiality, Integrity and Availability, the golden CIA triad. These publications will assist in determining the CIA impact level pertinent to an organization’s environment. When these risk impact levels have been determined, the IoT Security Controls Framework can be used to tailor security controls to the organization’s systemic environment. The IoT Security Controls Framework is a great resource for designers and developers who are tasked with creating secure IoT systems and other evaluators of IoT systems. Designers and developers can use this tool to continually evaluate the security of their implementation as they progress through the development life cycle. The tool offers a holistic evaluation of an IoT system to ensure it meets industry-specified best practices. Tripwire supports manufacturers of connected IoT devices and organizations that utilize them by providing rigorous security assessments. Tripwire’s device testing approach includes identifying security risks and vulnerabilities that may exist in the physical construction of the device and its network interfaces. You can learn more by downloading this solution brief.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

