
The Cyber Security Body of Knowledge project or CyBOK is a collaborative initiative mobilised in 2017 with an aspiration to “codify the foundational and generally recognized knowledge on Cyber Security.” Version 1.0 of the published output of this consultative exercise was quietly released last year and then more publicly launched in January 2020. Yet, this free and information-packed publication does not appear to have captured the attention it perhaps deserves across the wider industry. Hence the reason for blogging and discussing a very quick overview of it here on State of Security. So, what does it look like?
Composition and Domain Categories
Across its 800+ pages, the CyBOK is effectively organized into nineteen top-level Knowledge Areas (KAs) and then grouped into five overarching categories, as shown in this diagram.
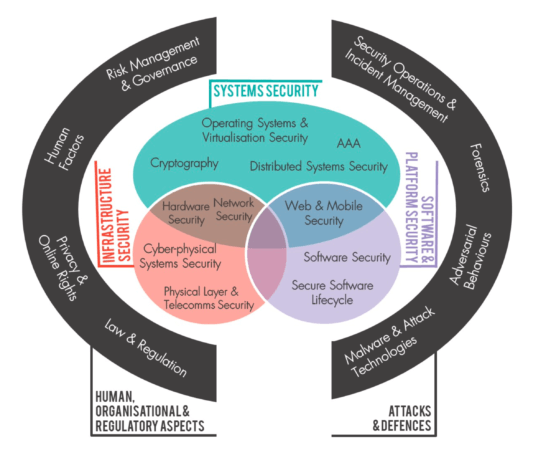
CyBOK Knowledge Areas Much of this will be familiar territory for many security professionals, some of whom have actually questioned if it is not simply “reinventing the wheel?’” (ISC)² has after all, already established a widely recognized ‘Common Body of Knowledge’ or CBK for its Certified Information Systems Security Professional (CISSP) accreditation. For those unfamiliar, the overarching CISSP CBK domain categories, are:
- Security and Risk Management (including Legal & Regulatory, Personnel Security, Threat Modelling)
- Asset Security (including Data Management, Privacy)
- Security Architecture and Engineering (including Security Models, Cryptography, Physical Site)
- Communication and Network Security
- Identity and Access Management (including IAM, IDaaS)
- Security Assessment and Testing
- Security Operations (including Incident Response)
- Software Development Security (including Malware)
Origins and Definitions
Originating in the early 1990s before the term ‘Cyber’ was common parlance for IT related security matters, the (ISC)² CBK has more traditionally been known by many as a ‘Common Body of Knowledge for Information Security’ of course. Whereas the CyBOK begins by offering distinct definitions for both ‘Information Security’ and ‘Cyber Security’, presenting the former as a contributor to the latter. Yet, there is an inevitable overlap of knowledge and topics across both taxonomies, just as there is within their actual practices in the real world of course. Given also, that this is the definition which the CyBOK uses in its introduction:
“Cyber security refers to the protection of information systems (hardware, software and associated infrastructure), the data on them, and the services they provide, from unauthorised access, harm or misuse. This includes harm caused intentionally by the operator of the system, or accidentally, as a result of failing to follow security procedures.”
Such a definition could apply just as relevantly to much of the CISSP CBK, however. Blurring these arguably subjective lines further, (ISC)² have more recently taken to promoting CISSP as being ‘the world's premier cybersecurity certification.’ A less semantic and perhaps more useful differentiator to consider instead, is that the CISSP CBK is also a curriculum for the certification itself. Although sometimes disingenuously described as being ‘an inch deep and a mile wide’, it is, in reality, more ‘a mile wide and a foot, or even yard deep in certain places.’ The CyBOK instead seeks to ‘map to’ established knowledge sets via a structured framework. This mapping may then be used to “inform and underpin education and professional training for the cyber security sector.” The opening narrative of the ‘Law & Regulation’ category someway acknowledges this by disclaiming itself to be “a mere starting rather than ending point” and the same could be said to apply throughout the CyBOK. But that is not to say it is just some dry reference manual of other works. The clear expository narratives which accompany each of the knowledge areas are all original, insightful and very readable. Likewise, the quality of expertise drawn upon to create the diverse ‘Knowledge Areas’ in their own right and then collate all of this into one cohesive publication should not be underestimated. Moreover, it positions itself as vendor agnostic, academically independent and, whilst sponsored by the UK’s National Cyber Security Programme, a cross-border effort of trans-global rather than marginalized national focus.
Knowledge Areas
The CyBOK also seeks to gather a balance of input from both academia and industry. With its prolific use of functional equations and theoretical models throughout the text, it does come across as being more at home within the classroom or laboratory environment than the operational, business driven frontline at times.
Cryptography
But as with the CISSP CBK once again, such an approach is for some areas both appropriate and somewhat inevitable. Cryptography for example, is an essentially mathematically rooted subject area. The KA for cryptography therefore warrants a suitably scholarly approach to both its curation and to the prefatory descriptions of some of the core concepts as they relate to cyber.
Malware
Likewise, the ‘Malware’ KA with its ‘lab eye view’ of its subject matter, descriptively ‘dissects’ characteristics and tactics of different malware families whilst discussing some of the analysis techniques used to understand them. It goes on to include clear, succinct explanations of some common ‘anti-analysis’ and detection evasion techniques such as ‘packing’ (compressing or encrypting part of the code.). These are base concepts for sure, but they are often glossed over in more overtly sales focused, industry publications on malware. Such key technical considerations are then complemented and contextually framed by a brief introduction of the ‘Underground Eco-System’ driving the ever-evolving malware lifecycle itself. Underground economics, monetization and black-market operating models all being cross-cutting themes discussed elsewhere, such as in the subsequent KA for ‘Adversarial Behaviours.’
Forensics
The ‘Forensics’ KA similarly offers a high-quality potted summary of key concepts, tools and methods as they are used to establish evidence in legal proceedings. It introduces some relevant cognitive, conceptual models such as the ‘sense-making’ and ‘foraging’ loops and then moves into describing specific analytical techniques and methods. Bringing its subject matter firmly up to date, it concludes by acknowledging the transition and challenges that cloud computing & IoT brings to the science of digital forensics.
Security Operations & Incident Management
The ‘Security Operations & Incident Management’ (SOIM) KA provides a solid representation of many of the key principles and components one would expect to be included for SOC type considerations. From base architectural principles to logs, network flows, anomaly detection, IDS/IPS, SIEM, SOAR. Leading into an overview of Incident Management planning and process groundwork. In places some of it is very well-trodden ground which could probably benefit from wider and more diverse contemporary industry input. Accepting of course that only so much consultation is feasible and affordable for a single project and such an undertaking is easier said than done. However, what is covered here is covered very well. It’s precise and authoritative narrative describing what good practice can look like whilst acknowledging the inherent fallibility of many tools, techniques and processes in detecting and stopping ‘all’ threats or achieving the nirvana of ‘total’ security. A state that is of course impossible, as it acknowledges from the outset in the referencing of a report from 1981 by James Anderson.
Final Thoughts
All in all, the sheer breadth of information condensed into this one collective work is as impressive as it is vast. Whilst I’ve cherry picked just a few of the KAs to highlight here, it would be futile to try and discuss every single one in a short blog such as this, let alone do any reasonable justice to any of them. But don’t just take my word or views about it, take a look for yourself. The CyBOK is freely available and accessible under the open government license, so there’s really no excuse not to. Admittedly, for many people it’s probably not a ‘cover to cover’ read (unless you are perhaps landed with a lot of time on your hands as a result of the pandemic lockdowns.) For professionals or anyone curious to understand more about the diverse range of knowledge areas which collectively define and support what we have come to call ‘Cyber Security.’ it is at the very least a useful reference to dip into as necessary. Given the comprehensive mapping it also gives you to a wealth of established knowledge sets, papers and other references (all helpfully linked to directly in its bibliography) who knows where it may lead you next?

About the Author: Angus Macrae is a Certified Information Systems Security Professional (CISSP) in good standing. He has more recently been awarded the CESG Certified Professional – IT Security Officer (ITSO ) role at Senior Practitioner level. He is currently lucky enough to live in and publicly serve the beautiful county of Cornwall in the UK. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

