
In this blog series, I will be putting the spotlight on useful Ghidra features you may have missed. Each post will look at a different feature and show how it helps you save time and be more effective in your reverse engineering workflows. Ghidra is an incredibly powerful tool, but much of this power comes from knowing how to use it effectively.
In this post, I will again be going over how to use Ghidra to download symbols from a PDB Symbol Server and apply them to a loaded program. As noted in the previous post on this feature, PDB support is a rapidly evolving feature. Ghidra 10.x has made some considerable improvements including a new workflow with support for multiple local or remote symbol servers. This post contains updated steps for using Ghidra to download and apply symbols for a Windows OS binary. Please refer to the previous post for more information on the background of this feature.
Without further introduction, here are the steps for identifying, downloading, and applying Windows PDB files from Microsoft’s public symbol server. The steps were tested on macOS running Ghidra 10.0.1 via Amazon Corretto for JDK 11:
Step 1: Import a Windows executable or library into a Ghidra project.
Step 2: Open the program in CodeBrowser and select ‘No’ when asked to analyze the program.
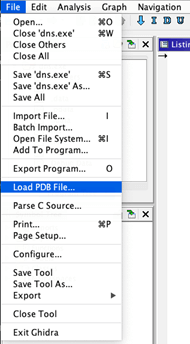
Step 3: Select ‘Load PDB File…’ from the File menu.
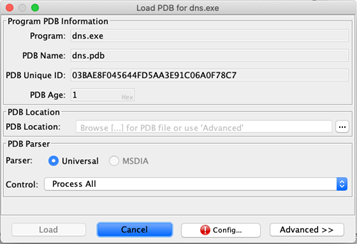
Step 4: Click “Config…” to load the Symbol Server Search Config window.
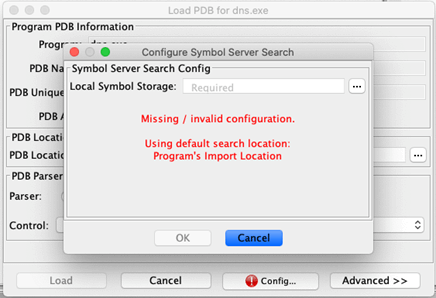
Step 5: Click the ‘…’ button, select a local path to store symbols, and click OK.
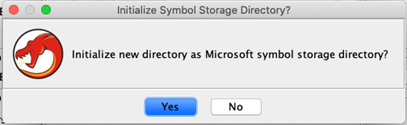
Step 6: Click ‘Yes’ to initialize the new directory.
Step 7: Click the ‘+’ icon to add a new symbol server location.
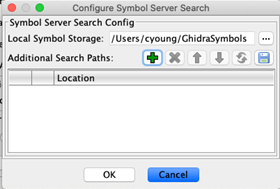
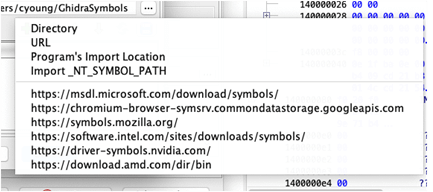
Multiple servers can be added to the search path. Click OK when all desired servers are added to the config. The pre-defined options in 10.0.1 are:
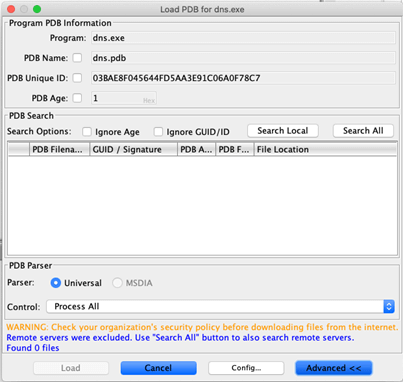
Step 8: The ‘Load PDB’ window is shown again. Click ‘Advanced >>’ to reveal the ‘PDB Search’ section and click ‘Search All’ to query remote servers for the program’s PDB file.
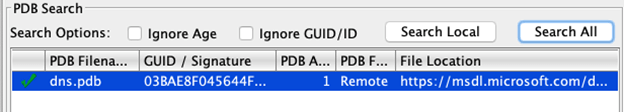
Results are displayed in a table. Select an appropriate PDB and click ‘Load’ to apply it to your session.
Step 9: Be patient while Ghidra applies the PDB.

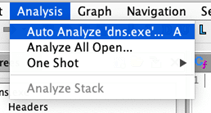
Step 10: Kick off an Auto Analysis by using the shortcut key ‘A’ or the menu ‘Analysis->Auto Analyze <Program>….’
All available Ghidra views and plugins should now be integrated with the debugging information from the PDB.
Read More about Ghidra
Ghidra 101: Cursor Text Highlighting
Ghidra 101: Slice Highlighting
Ghidra 101: Decoding Stack Strings
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

