
If you’ve read a newspaper or watched the news in the past few weeks, you’ll notice one common topic that all the major news outlets are discussing… COVID-19. Right now, many companies are trying to provide employee guidance during this worldwide pandemic, as governments ask those who can to work from home in an effort to slow the spread. Zoom, a popular remote conferencing solution, has taken the crown and become the go-to option for millions of professionals, students, and families due to its ease of use and simple setup. Zoom has exploded in the last couple months, going from 10 million meeting participants as of December to over 200 million as of today. With this increase in usage, Zoom’s security has been drawn into the light. Several friends and family have asked me if using Zoom was safe to use and the answer is that it depends on several things, but using a few security tips, they can keep their online conferences safe and protected.
1. Configure a Meeting ID and Password
Setting a meeting ID and password seems trivial but it’s far from it. Attackers and disrupters can guess or enumerate meeting ids using a process called “war dialing.” zWarDial is a tool used to identify the phone numbers that can successfully make a connection to a computer modem or in this case a Zoom meeting. The use of zWarDial, makes it important to set a password to help stop uninvited guests from performing a “Zoom Bombing”, in which uninvited guests introduce inappropriate content to your conference call.
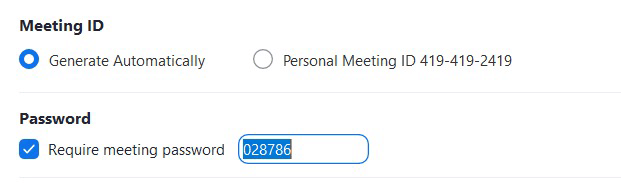
Screenshot of Meeting ID and Password Controls
2. Enable Waiting Room
Zoom has a feature called “Waiting Room” which allows the host to control when a participant joins the meeting. As the host, you can admit attendees one by one or hold all attendees in the waiting room and admit them all at once. This option allows hosts to be selective and allow entrance for attendees they’re expecting.
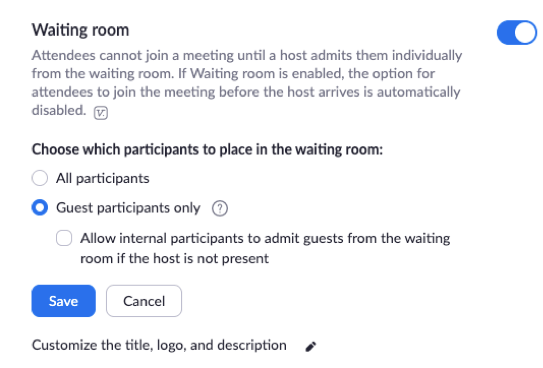
3. Disable “Join before host”
Disabling “join before host” will prevent attendees from entering a Zoom meeting before the host. This is important because with this setting enabled the first attendee who joins the meeting will automatically be made the host and have full control over the meeting.

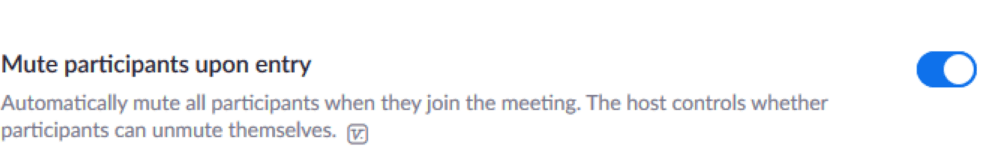
4. Enable “Mute participants on entry”
This function will allow the host to have all participants automatically muted upon entry. With the exception of webinars, participants will be able to unmute themselves in the meeting. Having meeting attendees muted as they join will reduce noise disruption.
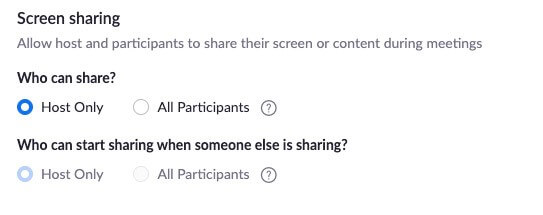
5. Enable Screen Share to “Host Only”
Preventing others from screen sharing unless given permission will keep the meeting orderly and prevent unexpected users from disrupting the meeting via screen sharing.
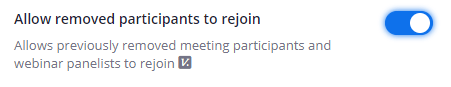
6. Disable “Allow Removed Participants to Join”
If there is a disruptive attendee or an uninvited guest that connects and the hosts removes them, disabling this feature will ensure that they cannot continuously rejoin the meeting.
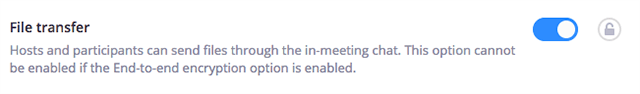
7. Disable “Allow File Transfer”
Malware can be shared via file transfers, so by disabling file transfer during a zoom meeting you will prevent any attendees from sharing potentially malicious files.
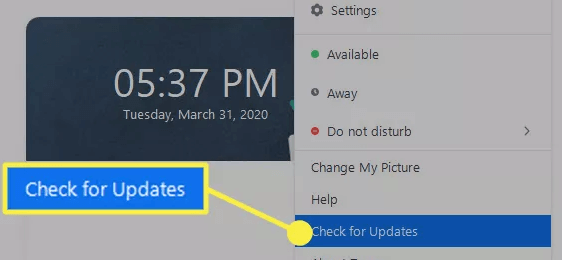
8. Keep your Zoom application up to date
Keeping your applications up to date ensures you have the newest features and security updates installed. This should apply to all your applications, not just Zoom.
Zoom excels at being easy to use and widely available in both free and paid versions, but don’t mistake increased usage for increased security. There are issues with most software and Zoom has been very transparent by acknowledging their issues and showing that they have a plan for mitigation. In fact, they’ve hired several security consultants who have worked with the likes of Microsoft, Facebook and Google, and tasked them with plugging up the recent bevy of security bugs. So, with these steps taken to ensure a secure conferencing environment, stay safe and Zoom on.

