
Cybersecurity has become a critical concern in every business sector nowadays due to organizations’ growing dependency on technologies. Research by Immersive Lab reported that in 2019 there were more than 20,000 new vulnerabilities. Not only that, TechRepublic reported that global companies experienced a 148% spike in ransomware attacks after COVID-19 hit the world. So, for most organizations, the question isn't who will be the target of a cyber attack. Instead, the question is, “When will it occur, and how do we deal with it?”
Organizations need an incident response plan to combat future incidents so that they can protect their business reputation and finances against malicious activity. But how can they know that the plan they have is efficient enough to alleviate future cyber incidents? By using a cyber crisis tabletop exercise (CCTE), organizations can test or rehearse the emergency preparedness plan before a crisis occurs.
What is a Cyber Crisis Tabletop Excercise?
A cyber crisis tabletop exercise, also known as cyber incident response test, helps organizations to identify different risk scenarios and prepare them for cyber threats. It’s an activity to evaluate whether your organization’s incident response plan works effectively in the case of a cyber attack. Towards that end, it considers several simulated scenarios that could profoundly impact your business if they happened in reality.
Internal and external stakeholders, C-level executives, and/or an internal security team from your organization could be participants of a CCTE. The whole exercise is guided by a skilled facilitator or top management personnel who analyzes the crisis management capabilities of an organization and ensures that response and recovery plans are well coordinated and communicated. They also keep participants focused on the exercise objective.
Benefits of Cyber Crisis Tabletop Experience
Cyber crisis business exercises help businesses to achieve the following:
- Develop a better understanding of breaches in a cost-effective way without any disruption to business systems and processes
- Maintain business reputation and customers’ trust through effective communication and better management
- Coordinate communication within teams and departments, thus improving response plans’ effectiveness
- Help top management personnel and other participants to understand their roles and responsibilities in case of a cyberattack
- Identify loopholes or defects in the response plan as well as evaluate teams’ ability and readiness in the face of an incident
Types of Cyber Crisis Scenarios to Practice with Tabletop Exercise
There are some cyber crisis scenarios organizations may face in the future that could affect their business continuity. To mitigate those threats, organizations should be aware and well-prepared to respond to the below-mentioned scenarios and threats.
Scenarios 1: Malware Attack
A malware attack is where criminals make their way into your system through malicious software so that they can destroy your system or access sensitive information. This could involve an employee from your company who accidentally inserts a malware-infected SD card into the company’s system.
In this scenario:
- Processes tested: Detection ability/User awareness
- Threat actor: Accidental insider
- Asset impacted: Network integrity
Scenario 2: Unauthorized Access
This is one of the most common examples of a data breach where attackers intend to access your organization’s data or network without the requisite permissions.
In this scenario:
- Processes tested: Incident response
- Threat actor: Hacktivist
- Asset impacted: Network/System
Scenario 3: Ransomware Attack
This is one of the challenging situations for organizations to deal with. According to Verizon Data Breach Report 2021, the range of losses in 95% of ransomware cases fell between $70 and $1.2 million; the median amount lost was $11,150. This threat has grabbed third place in breaches by doubling its frequency from last year.
In this scenario:
- Processes tested: Incident response
- Threat actor: External threat
- Asset impacted: Financial data
Scenario 4: Cloud Compromise
Almost every business nowadays stores their data on the cloud. Attackers know this, which is why they’re increasingly targeting these environments to expose sensitive information.
In this scenario:
- Processes tested: Incident response
- Threat actor: External threat
- Asset impacted: Cloud
Focus Areas to Cover for a Successful Tabletop Exercise Workshop
To ensure the success and efficiency of the exercise and desired result for business continuity, the following focus areas must be covered:
1. Scenarios & Threats
To make a tabletop exercise successful, the facilitation team intends to create scenarios and threats to emphasize questions like “Who is the threat actor?,” “What is their intent?,” and “How will the team handle and respond to the attack?” Focusing on threats and scenarios help businesses to understand the risks that they might suffer after a cyberattack as well as to confirm that the cyber incident response plan is efficient enough to eliminate those risks.
2. Threat Actors
Threat actors could be a group/individual with malicious intent or a key driver in malicious activity that seeks to undermine an organization’s IT security. It is vital to enlist the threat actors in organizations’ tabletop exercise and assess their impact on a business.
3. Critical Assets
Another crucial element to make the cyber crisis tabletop exercise successful is to simulate a compromise involving the critical assets of the business. Therefore, it is essential for participant teams to address the impact of an attack on their critical assets and reevaluate the plan to protect or mitigate the effects of cyber crises on those resources.
How to Perform a Cyber Crisis Tabletop Exercise?
As we explained earlier in the blog, participants in CCTE test their response capabilities. They can use the following steps to design and conduct a cyber crisis tabletop exercise:
Step 1: Identify Objective
The selection of objectives should be determined on core capabilities specific to the needs of an organization during a cyberattack.
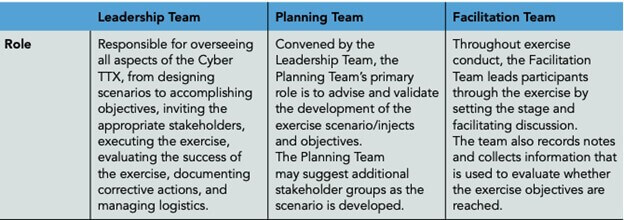
Step 2: Composition of Teams and Stakeholders
After identifying the objective, organizations are required to identify the exercise leadership team, stakeholders, planning team, and facilitation team to successfully plan, design, and conduct the exercise.
Step 3: Select Scenario Type
Once your organization has finalized the team and their objective for the exercise, the leadership team must identify the scenario type per the incident or cyberattack and create one for the purpose of practicing the exercise plan.
Step 4: Create a Meeting Schedule
The exercise leadership team must create meeting schedules for other participants to discuss exercise design topics and review response plans.
Step 5: Design the Exercise & Provide a Timeline
Designing the exercise is different for each organization. It depends on the type of scenario the exercise is hosting. For this, develop a script including surprising elements and formulate a series of probing questions to stimulate debate among team members. Furthermore, a timeline is provided for the exercise to play-out.
Step 6: Conduct the Exercise
After this, the exercise is performed, where many ideas and solutions are provided and evaluated.
Step 7: Prepare Improvement Plan
After performing and evaluating the exercise, a detailed after-action report is prepared along with potential improvements.
A TTCE is a flexible approach, and steps to perform the exercise can be customized based on the exercise objective. The rule of thumb for each tabletop experience is the same, though: after an exercise is considered complete, the findings and lessons learned are documented in the after-action report/improvement plan. And the plan is modified accordingly.
Best Practices to Make Cyber Crisis Tabletop Exercise a Hit
There are some best practices that every organization should follow to make the tabletop exercise successful and effective. Here are a few to keep in mind:
- Take time to prepare incident response plans for the exercise
- Involve multiple members from throughout the organization to build teams
- Make sure that all the participants know the basic rules of the exercise
- Leverage resources from outside agencies, the government, and within your industry
- Keep the scope of the exercise broader while structuring the tabletop exercise
- Invite subject matter experts to the planning team to make the scenario realistic
Summing Up
A tabletop exercise is a crucial approach in the cybersecurity realm. However, this exercise is not restricted to cybersecurity. Any organization with some disaster or crisis can benefit from running this exercise. CCTE is designed to discover organizations’ weaknesses and ensure that organizations implement best practices and protocols for cybersecurity.
However, it’s worth spending time on the exercise if you have a response plan ready for the scenario you’ll be running through as well as if the top management personnel agree on letting you change the plan and policies based on the exercise result.
Not only that, but make sure that the tabletop exercise your team is conducting is appropriate for your organization.
About the Author: Hardik Shah is a Tech Consultant at Simform, a firm which provides custom software development services. He leads large scale mobility programs that cover platforms, solutions, governance, standardization, and best practices.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

