
Ransomware attacks continue to plague organizations globally regardless of their size. In a press release by the NCC group that preceded the Annual Threat Monitor Report 2021 published for the year 2021, there were an estimated 2,690 ransomware attacks, a 92.7% increase from 2020s figures of 1,389. The increase of ransomware attacks builds upon the general gradual rise in cyber-attacks in the wake of the COVID-19 pandemic. Ransomware accounted for roughly 65.4% of global cyber incidents in 2021. North America and Europe accounted for the most attacked regions with 53% and 30% of all the attacks respectively.
Ransomware Threat Trends
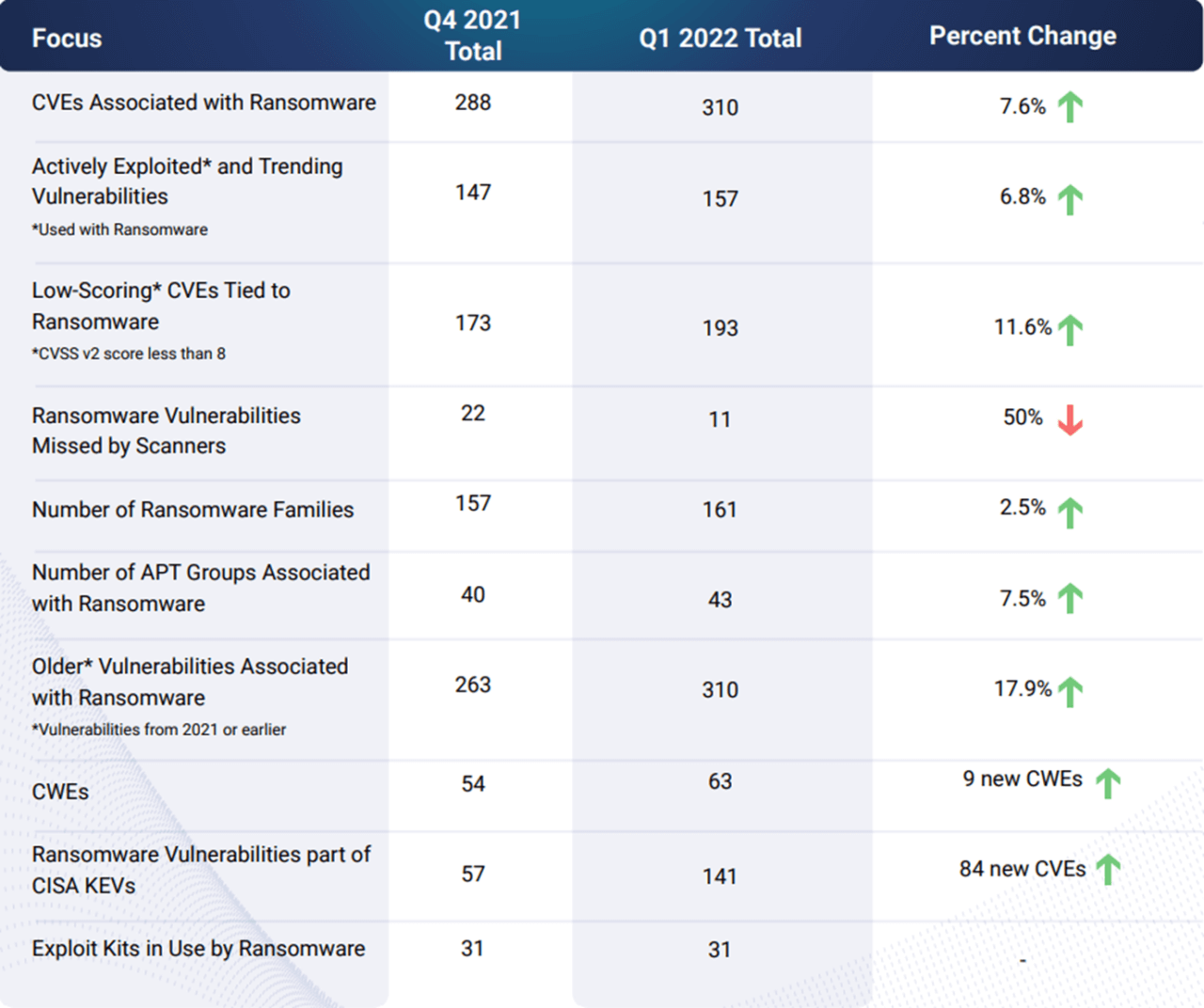
In a Ransomware report published by Cyber Security Works for Q1 of 2022, there has been an increase in eight of the ten ransomware foci. One positive revelation is that ransomware vulnerability detection capabilities appear to be improving. However, it is uncertain if this accounts for copycat variants, or if these are truly unique signature detections. Regardless of that curiosity, the figures in comparison to 2021 show the unrelenting nature of the current ransomware ecosystem.
Accordingly, in the PhishLabs Ransomware Playbook for Q1 2022, enterprises are specifically being targeted by ransomware operators to disable their critical systems and publish their stolen data. This has led to a 144% increase in ransom demands with victims being convinced more to pay ransoms in the hope their stolen data is not sold to third parties or published in criminal marketplaces.
Understandably, most organizations that suffer ransomware attacks are left with the options of either not paying and risking their data being exposed, or paying the ransom in the hope that the threat actor does not release their data afterwards. Either way, it is a difficult position to be in, one often influenced by other decisions such as reputational damage, a halt in operations, and a complete loss of data.
Why the Rise?
Despite the sophisticated security systems employed by most organizations to combat cyberattacks, there still has been a steady increase in these criminal activities, notably ransomware. This can be accredited to a number of factors:
Initial Access Brokers (IABs): Initial access brokers are cybercriminals who specialize in breaching companies and then selling the access to ransomware attackers or basically anyone willing to buy. IABs can gain unauthorized access to victims' networks using a variety of methods. Some frequent techniques include exploiting remote management software that they have accessed through brute-force methods, weak remote desktop protocols, and unpatched vulnerabilities. Brokers can sell, and resell their successful access information to other criminals. The benefit of purchasing ready access to a corporate network for criminals is clear. Buyers need not do any of the reconnaissance work, and can choose from a menu of options, picking victims based on their revenue, country of origin, and industry, as well as the type of remote access being offered.
Double and Triple Extortion: The Double extortion tactic was first used in 2019 by the Maze Ransomware group. Since then, the tactic has become more widely used by a number of threat actors, and subsequently advanced further to Triple Extortion. In a double extortion attack, the attacker exfiltrates the data they want to use as leverage, launches a ransomware attack, and then threatens to sell the data's exposure – which could entail selling customer personal information or the victim company's intellectual property – in exchange for money. Triple Extortion involves either additional attacks launched against the original target if they refuse to pay the ransom, or attacks against the victim’s clients that was gathered through the original data theft.
Ransomware-as-a-Service(RaaS): This is a Software-as-a-Service model that leverages enables threat actors to launch ransomware attacks without knowing how to code their own ransomware. This is simply “ransomware for sale”. This type of service provides a low barrier point of entry for inexperienced threat actor groups to participate in enterprise-level exploits using enhanced and proven ransomware variants. RaaS models often allow affiliates access to instructional videos, 24/7 support, and dedicated dashboards. The ransomware itself is built using ransomware builders, which is instruction-based do-it-yourself software.
What can be done?
It is general practice for most organizations to conduct a more passive approach to securing their digital assets. While this is effective in guarding against a number of cyber threats, it has proven to be ineffective against ransomware attacks. As such, a more active approach should be undertaken. An active approach offers a more layered approach to security. This layered approach is often termed “defense-in-depth”, enabling organizations to:
- Analyse their existing security posture for gaps and vulnerabilities, and remediate them to prevent future attacks.
- In the case of a data leak, assess which of their data has been leaked online, the sensitivity of the data and the best approach to mitigation.
- Be proactive to prevent data breaches.
Defense-in-depth, a layered approach to cyber security
Using defense-in-depth as a layered approach to guarding against ransomware involves a holistic approach to security. This holistic approach is sub-divided into three steps: collection, curation, and mitigation.
Collection
Collection involves organizations having enhanced visibility in data collection. This can be done by organizations spooling data from as many targeted sources as possible including social media, new and existing domains as well as email addresses. Open, deep, and dark web monitoring should also be incorporated.
Email monitoring is primarily important. Email remains the primary attack vector for ransomware. Ransomware is often delivered via impersonations of legitimate businesses using business email compromise (BEC) emails and phishing lures.
Open, deep, and especially dark web monitoring is crucial because it allows organizations to have an insight into marketplaces where leaked data are sold, as well as offering a good understanding of threat actors.
Curation
Curation of the collected data involves sifting through potentially thousands of data so organizations can determine which are relevant and pose an immediate or potential risk to their organizations, and which are irrelevant. Proper curation of data is a multi-layered approach that involves the very best of automated logic and analysed results which are then further examined by specialists. Simply put, curation can only be properly done by a combination of skilled human and automated technical assessment, and if possible, by hiring specialists to examine at specific subsets of search results. All of this would lead to the development of ransomware Indicators of Compromise (IoC) and Proof of concepts (PoC).
Mitigation
After data is collected and curated, mitigations must be put in place. For ransomware, this is done either through technical blockers or takedowns.
Technical blockers involve employing IoCs to block suspicious emails, either automatically, or reported by employees, to stop threats from being exploited inside the company. Additionally, user traffic to and from suspicious domains must be blocked.
Takedown refers to the complete removal of any data or websites created to spread stolen data or ransomware. This, of course, is more involved, and is not something that an organization may undertake without the assistance of law enforcement authorities. It is, in fact, illegal to “hack back”.
In the case of dark web, removal of data isn’t as straightforward. The best remediation is to continuously and closely monitor the activity associated with the data so as to come up with the best mitigation possible.
Organizations have traditionally employed a number of passive approaches in their defense against ransomware attacks. While these methods are often regarded as industry-standard and have in the past helped, they are somewhat outdated and do not offer a holistic approach to security against more modern ransomware strains.
As ransomware variants evolve, and new ransomware strains are seen and exploited in the wild, a more active approach to security is needed. This is done using defense-in-depth, which utilises a multi-layered approach to security, often termed “offensive” security.
A layered approach to security helps reduce the impact of a ransomware attack before it happens. In a case where a ransomware attack has already occurred, a defensive approach gives organizations a wider scope of action towards remediation since they will possess an awareness of the collated data, giving them the ability to devise the best mitigation strategies possible.
About the Author: Musa is a Cyber Security Analyst and Technical Writer and has been writing professionally since 2017. Till date he worked with several organizations in the fields of women lifestyle, ecommerce and Cyber Security as a Technical Writer. He currently works as a Cyber Threat Intelligence Analyst and vulnerability analyst for an MSSP in Nigeria and is looking to further expand his Cyber Security Career, potentially incorporating DevSecOps in future.
Twitter: @nadeer_sani
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

