
The Clifford Stoll’s interesting story of stalking the wily hacker back in the 80s was probably the first time deception was used for catching a hacker. Since then, the technology has changed a lot, but the concept of honeypots and deception in general has remained the same. Despite the undeniable and important role that honeypots have in proactive defense strategies, they are still not widely accepted and deployed in production environments. So far, honeypots have been primarily used by security enthusiasts and researchers for discovering new attacks, collecting malware, and studying the attacker’s tools, tactics and motivations. In the last couple of years, however, once breach detection became a new must-have security tool and enterprises shifted their security focus from prevention to detection and response, more {mature} companies have started to adopt deception-based security technologies. As Gartner has predicted, by 2018 about 10 percent of enterprises will use deception tools and techniques against attackers. One of the most important use cases of deception is for breach/post-breach detection. Knowing the global median time of compromise to discovery of an attack, which was 146 days according to M-Trends 2016 report, you can better understand the need for such a tool. Now, let’s see how we can leverage deception as a free (or at least cheap) breach/post-breach detection tool. Your deception system should at least include the following components:
- Honeypots
- Honeytokens or breadcrumbs, and
- Centralized logging and alerting system
Apart from these obvious components, you need to create several believable and well-designed deception scenarios. For the honeypot component, you can start by deploying open-source low-interaction honeypots, such as Cowrie (SSH and Telnet honeypot), Glastopf or its successor SNARE/TANNER (Web application honeypot), and Dionaea (Multi-protocol, malware capturing honeypot). Ideally, you should deploy high-interaction honeypots, but it requires more knowledge and effort to setup and maintain. Even for setting up a high-interaction honeypot, you don’t need any commercial tools. Instead, you can use the OS auditing capabilities combined with open-source endpoint monitoring tools and virtualization technologies for automating the deployment and maintenance of honeypots. As most of the open-source honeypots and endpoint monitoring tools support JSON logging, you can easily use a log management system, such as Elastic Stack, to collect, analyze and visualize the logs in real-time. However, for n00bs (and even experienced users), I highly recommend using T-Pot multi-honeypot platform, which includes dockerized version of several honeypots, ELK stack and some other useful tools.
Honeytokens, Breadcrumbs or Honeybits
In my opinion, Honeytoken is an important component of a deception system, and its value has been overlooked for many years. Honeytokens can be any resources like a bogus file or a fake database record that – just like the honeypots – don’t have any authorized use. So, any interaction with it can be considered as a potential breach or malicious activity. Some honeytokens contain beacons that are triggered when they are opened or accessed. Although some of these honeytokens, such as Word or PDF documents, can be easily identified by the attacker and are not that effective, some other tokens, such as URL and DNS tokens, are more effective if they are put in the right place. If you are interested in these beacon traps, have a look at CanaryTokens. There is another type of honeytokens that are even simpler than the former one. You don’t even need to monitor the access to these kinds of honeytokens, which are usually referred to as "breadcrumbs" because their value lies in being used (not just accessed) and leading the attackers to your decoys or honeypots. I have written a really simple tool called Honeybits to show how easy and effective it is to create and place these honeytokens on production servers and workstations to lure the attackers.
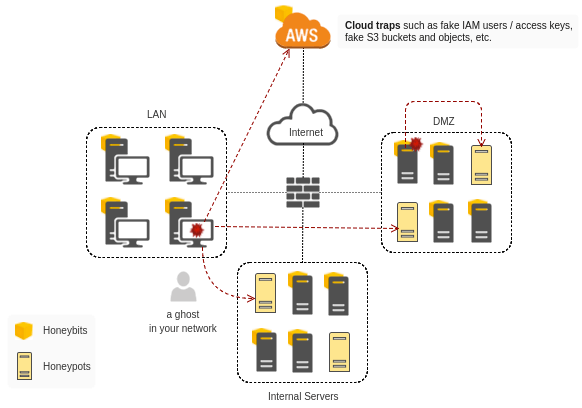
The problem with the traditional implementation of honeypots in a production environment is that the attackers can only discover the honeypots by network scanning, which is noisy! If you take a look at the Mitre ATT&CK Matrix, you will see that 'Network Service Scanning' is only one of the many different post-breach activities of attackers. The more you plant false or misleading information in response to the post-compromise techniques (especially the techniques under ‘credential access,’ ‘Discovery,’ and ‘Lateral movement’ tactics in ATT&CK matrix), the greater the chance of catching the attackers. So, deploying honeypots in your network is just not enough to deceive and catch an advanced attacker. For implementing an effective deception strategy, you need to design a comprehensive deception plan and point attackers to honeypots with different techniques. To learn more about deception-based security and honeypots, consider attending our two-hour workshop at BSides Canberra on March 17th and 18th. This workshop will be presented by Elliott Brink and myself. About the Author: Adel Karimi is a security engineer by day and honeypot researcher by night. He has been a member and chapter lead at the Honeynet Project since 2010, and he recently started Trapbits, an open community of honeypot enthusiasts in Australia. He has a passion for Deception, active defense and anything infosec! You can find him on Twitter at @0x4d31. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

