Brute force attacks are mitigated by using 2-factor authentication, which comes in many forms, such as time-based tokens, SMS and push authentication using a cell phone. A new contender has emerged: Universal 2nd factor or U2F. U2F is an authentication standard sponsored by the FIDO Alliance, whose members include the technology industry’s top companies and vendors.
What is U2F?
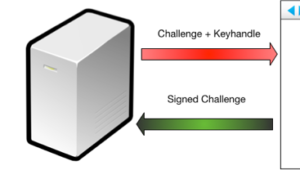
The U2F protocol has been implemented using a USB token device that features a button to activate the device. U2F combines challenge-response authentication and public-key cryptography. The server sends a challenge request to the client’s web browser, then the browser sends the request to the USB device. The USB device lights up, prompting the user to push the button to activate the device. Once activated, the device signs the challenge and returns the signed data back to the browser, which forwards it back to the server.
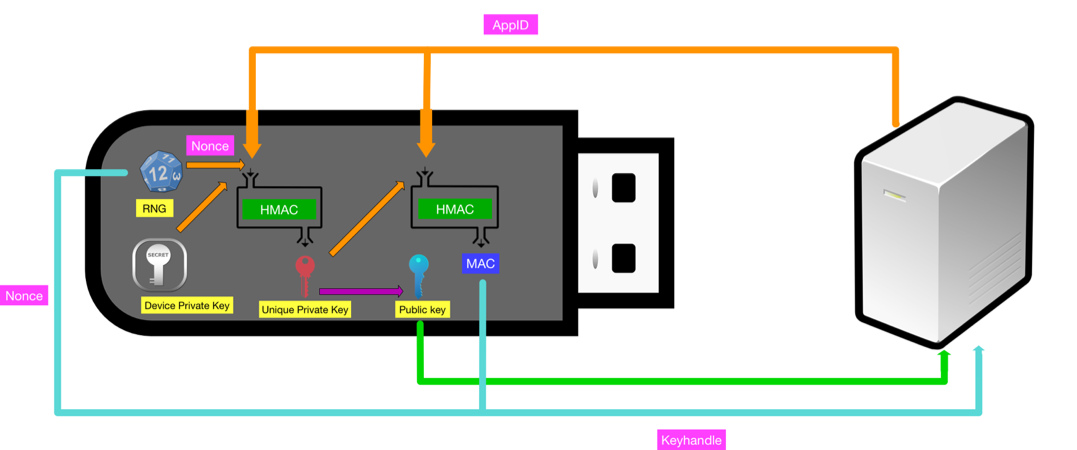
The U2F mechanism provides stronger security in a variety of ways. According to the top manufacturer, the device they produce features a hardware random number generator that is used during registration to create a nonce. In the registration process, the server provides an “AppId” that is passed to the device. Then, the nonce and AppId become input for a HMAC function using the private key stored on the device. The output of the HMAC is a unique private key for that individual service. This newly generated private key is then used to perform another HMAC function with the AppId and the resulting MAC is combined with the nonce to form the “Key Handle.” A public key is generated from the new private key and returned to the server along with the key handle. Upon authentication, the service sends the AppId, key handle and challenge to the device, which uses the provided data to generate the same private key to sign the challenge. The server then compares the signed challenge to the public key to ensure it was signed by the correct key. The token also has a counter that prevents replay attacks as long as the server validates the counter number is greater than the previous received number. This process is what makes U2F phishing resistant, as an attacker would have to know the AppId and the key handle to impersonate the service successfully. Additionally, if an attacker could hypothetically compromise multiple authentication databases of different services, he or she would not be able to correlate the users of the devices due to the unique keys created for each service. This also reduces the impact of data leak vulnerabilities such as Heartbleed, Cloudbleed and Rowhammer.
The manufacturers also write what is called an attestation certificate to the devices that can be used to validate the manufacturer of the token. These certificates are signed using a certificate authority and can contain vendor and model information. U2F keys provide several advantages to time-based tokens. They do not have a battery (excluding Bluetooth based devices). They never fall out of sync due to time drift. The private key stored on the device cannot be extracted, so cloning would not be feasible. U2F dongles can be bought for prices ranging from $10-$20. For the ultra-paranoid, it is possible to build your own for around 5 dollars. The DIY method gives the user control over private key and attestation certificate generation. The USB-only tokens are only useful for computers; this prevents their use on mobile devices. There are a few U2F devices on the market that use NFC or Bluetooth in addition to USB. A common concern with these tokens is losing them; therefore, it is recommended that you register more than one just in case. Currently, Google Chrome and Opera support U2F out of the box. Firefox can be used with an add-on. In testing, it was found that some server side implementations only support Chrome. Adoption of the U2F standard is accelerating with many web services using it, such as Facebook, the entire Google platform, Dropbox and GitHub. U2F can also be implemented as a Linux Pam module. U2F is not going to solve all cybersecurity problems, but it is certainly a step in the right direction.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

