
Google found that users who add a recovery phone number to their accounts effectively block 100 percent of automated bot attacks by doing so. The tech giant arrived at this finding after teaming up with New York University and the University of California, San Diego to investigate the efficacy of basic account hygiene in preventing account hijacking. It then presented the results of this year-long study on 22 May at The Web Conference. Google researchers Kurt Thomas and Angelika Moscicki explained that Google responds to a suspicious sign-in attempt such as from a new location or device by asking the user to provide additional proof of identity as a means of verifying themselves. They found that those who've signed into their phones or who use a recovery phone number in those instances can protect their accounts against all automated bot attacks. The same went for other verification measures such as last sign-in location and security keys, though a secondary email address was effective against just 73 percent of automated bots attempts. A recovery phone number has its limits, Thomas and Moscicki uncovered. They found that it wasn't as effective against phishing attacks or targeted campaigns in particular. However, they determined that users can compensate for these effects by activating SMS codes or on-device prompts. As quoted in their research:
If you’ve signed into your phone or set up a recovery phone number, we can provide a similar level of protection to 2-Step Verification via device-based challenges. We found that an SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks. On-device prompts, a more secure replacement for SMS, helped prevent 100% of automated bots, 99% of bulk phishing attacks and 90% of targeted attacks.
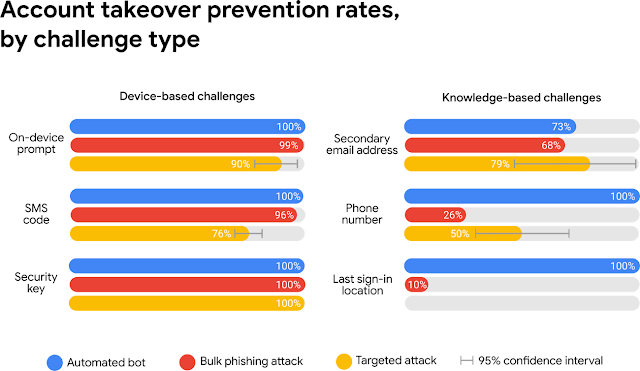
A summary graphic of Google's findings. As the above image shows, the only method that was effective against 100 percent of automated bots, bulk phishing attacks and targeted attacks was a security key. Users can consider adopting this level of security by reviewing Google's Advanced Protection Program. The findings presented above highlight the importance of users relying on something more than just a secure password to protect their accounts against hijackers. In the very least, they should seriously consider enabling 2-factor authentication or 2-step verification on common services that offer these measures. They should ideally enable these features via an authenticator app or a security key. (The 2018 Reddit data breach proved how weak SMS codes are as a means of multi-factor authentication.)
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

