
This is a follow-up/continuation to Part One of the series, where I recommend reading to help provide some background into why we should all consider reviewing our OPSEC (Operational Security), not just those with something to hide. Have you actually thought about how much you are tracked on a daily basis? Think about everything you post on social media, what you search, the apps that are generating metadata (with or without your consent), what your phone knows about you. Not forgetting your “voice assistants,” there is a worrying amount of data we generate every day that builds an impressive digital footprint.
All this data is incredibly valuable to an adversary, whether this be an advertiser trying to sell you better, cheaper, faster services through abusing privacy and online tracking or an attacker who’s trying to steal your identity or gain unauthorised access to your systems. The objective of good OPSEC (Operational Security) is to deny the enemy information that can be used to their advantage, the process and methodology of which will be detailed in this article.
Oversharing is a risk, one an adversary will capitalize on.
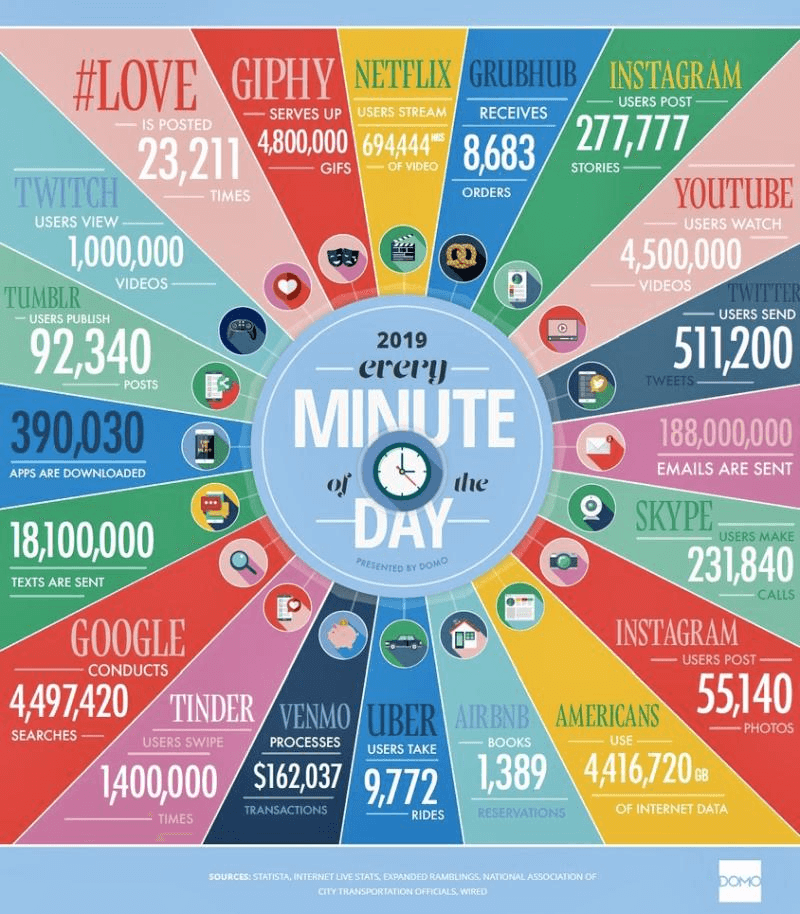
Even attackers make mistakes. Sometimes these are insignificant but provide a breadcrumb trail for investigators to dismantle criminal operations. In the case of Paige A. Thompson AKA “erratic,” they committed a significant OPSEC fail which led to their immediate arrest. In July 2019, Paige was arrested by the FBI on suspicion of illegally accessing and downloading data relating to over 100 million credit card applications from Capital One in the US. However, Paige AKA “erratic” made little to no effort to hide her identity boasting about the hack on Twitter. Information about the attack was posted on her Github account. This linked to her Gitlab, which contained her CV and all her personal information. It was also reported that details of the Capital One breach and other companies was also posted on a erratic’s Slack channel called Netcrave Communications. There was literally no effort to hide the breach or erratic’s real identity, leading to a swift arrest by the FBI.
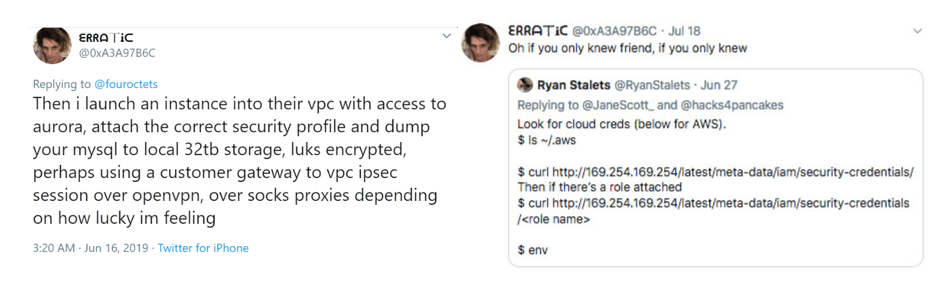
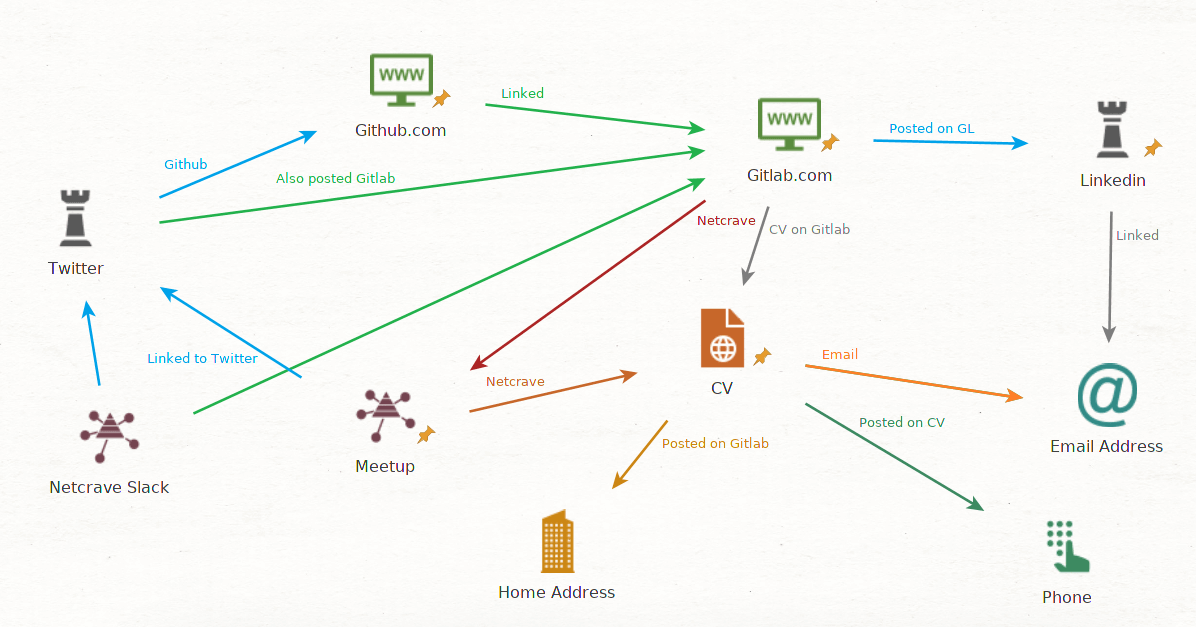
Figure 1: Twitter posts about erratic talking about the breach and a Maltego illustrating how their accounts were linked. Paige A. Thompson committed 3 OPSEC sins;
- Provided an adversary (law enforcement), evidence that could be used to their advantage
- Linked real identities to Pseudomys- massive OPSEC fail!
- Zero consideration for their Privacy (AND) Anonymity, including admitting on public channels to allegedly conducting the attack.
Identify, Analyse, Deny - The mindset and process of OPSEC
Protecting information from the adversary is not as simple as creating a Strong Passwords, MFA (although this is helpful), multiple identities (Pseudonyms) and using VPN/Tor etc. It's about understanding your exposure and what is not only valuable to you but also an attacker. There are three stages for protecting what you care about from the enemy. These are Identify, Analyze and Deny. In this article, we are going to cover Identify. The other stages will be covered in Part III.
Identify
“The important thing in strategy is to suppress the enemy's useful actions but allow his useless action” - Miyamoto Musashi, 1584-1645 Identifying information about yourself, what form it’s in and where it resides is the first step in performing OPSEC. You can’t protect what you don’t know about. The best way to remedy this is to perform open source Intelligence (OSINT) on yourself, with the emphasis on thinking like an adversary. Understanding and building a picture of your own digital footprint is both an enlightening and terrifying experience when you undertake this for the first time.
Search Engines
So where should you start? The obvious place is search engines. Start with Google and DuckDuckGo. For example, let's see what search engines can find just on your name try the following searches first:
- “Your Name"
- Intext:“your name”
- Inurl:”your name”
- Filetype:.doc intext:“your name”
Search engines are extremely powerful tools, and by using what we call search operators, you can uncover a lot of information. Here are the search operators for both Google and DuckDuckGo https://booleanstrings.com/2018/03/08/the-full-list-of-google-advanced-search-operators/ (Google stopped publishing search handlers, but this is a good list.) https://duckduckgo.com/bang (DuckDuckGo has bangs which are search shortcuts for each site. It's a nice feature.) https://help.duckduckgo.com/duckduckgo-help-pages/results/syntax/ (DuckDuckGo search handlers) In the below example, you can see there are over 3,660 results just from searching one of my usernames.
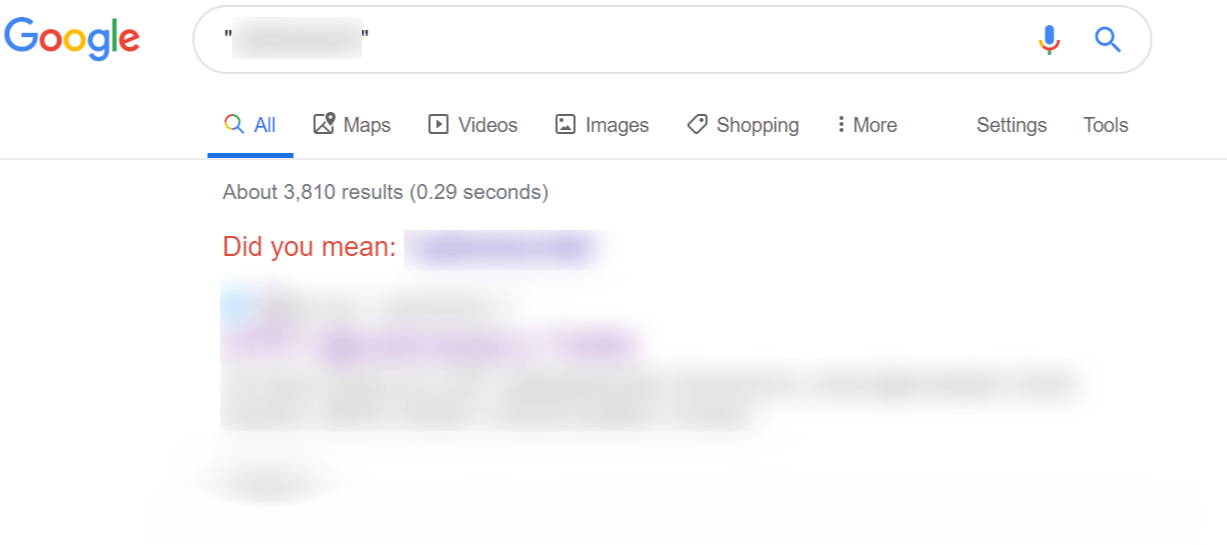
Figure 2: Google Search of Username However, if we use the inurl:username, we’ve now found a smaller number of sites where my handle appears in the URL, and actually has found some interesting results.
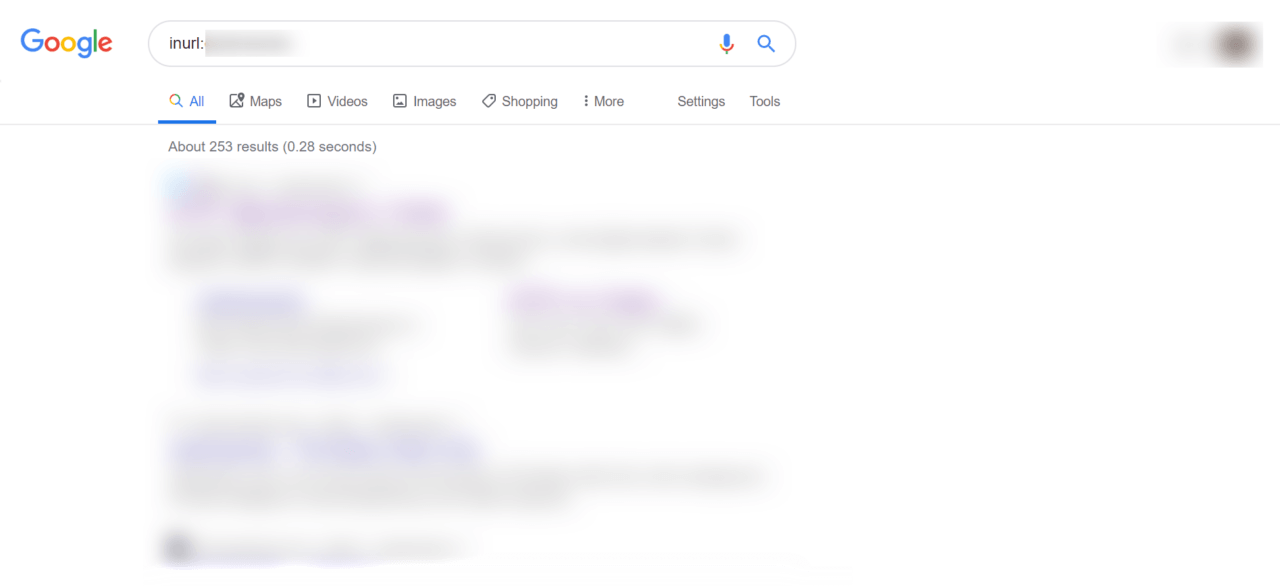
Figure 3: Google Search of Username In URL
Images
Next, we may want to look at where our images reside or where these are being used by an attacker. If you have a larger digital footprint, your profile may already be in use by dating scammers or fraudsters without you even knowing. There are a couple of really good reverse image tools you can use detailed below:
- https://www.tineye.com/ - great reverse image tool, fairly good results with this in the past.
- https://berify.com/ - another reverse image search tool
- https://images.google.com/ - Google’s image search is still very powerful
It's really important to be mindful of the content of your images. Really look at what is in the background that an attacker could use. For example, are there keys that could be 3D printed? Are there identifying landmarks that might give away your location? Remember that a motivated attacker has limitless time, and with this can be really creative, such as the recent Japanese stalker that found the location of a singer through the reflection of her eyes. Every image you post online is a clue. Aggregating this information can provide a clear picture not only to your pattern of life but also an insight into your location and home address and even clues to passwords.

Figure 4: Example of information in background useful to an attacker.

Figure 5: Post from CIA demonstrating how images can be used for intelligence gathering

Figure 6: Image from Twitter of work badge, which is extremely common, and great for social engineers!
Case Study
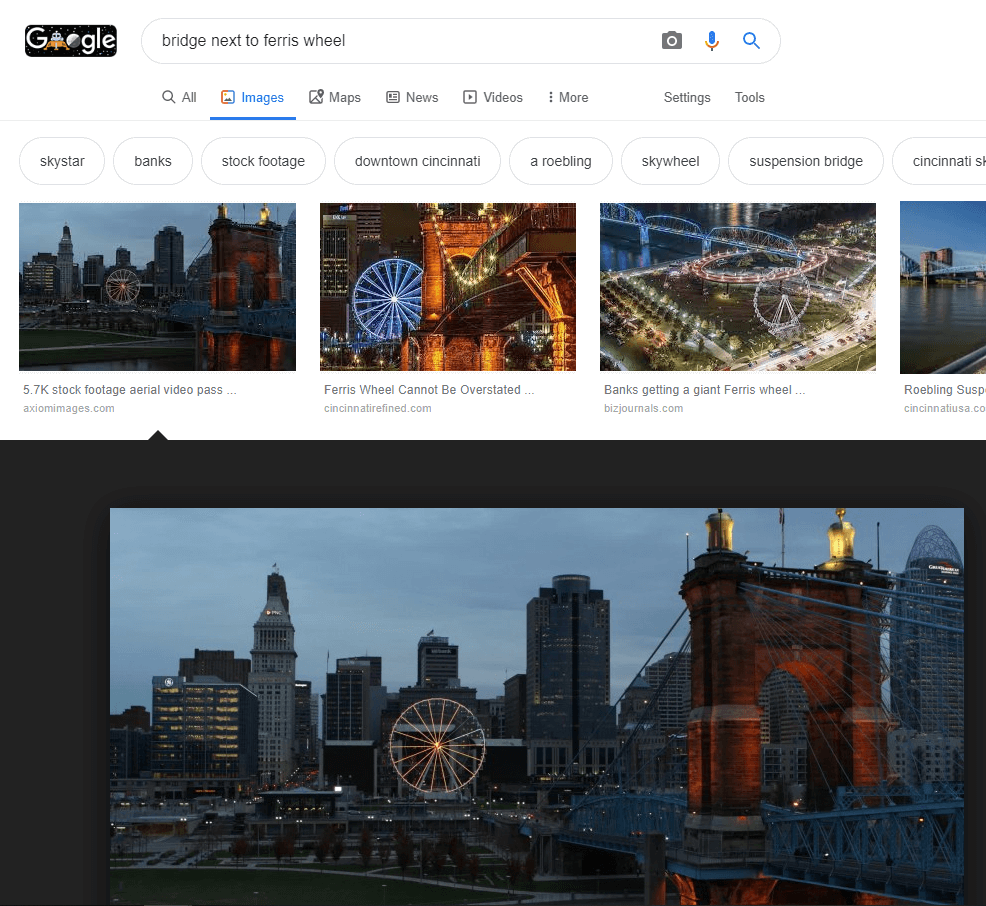
A good case study is from @thecyberviking, an expert on Open Source Intelligence. He was challenged by @rag_sec to find her location from a redacted image posted on Twitter.


CyberViking picked out some of the landmarks of the skyline and used Google Image search to try and work out the location.
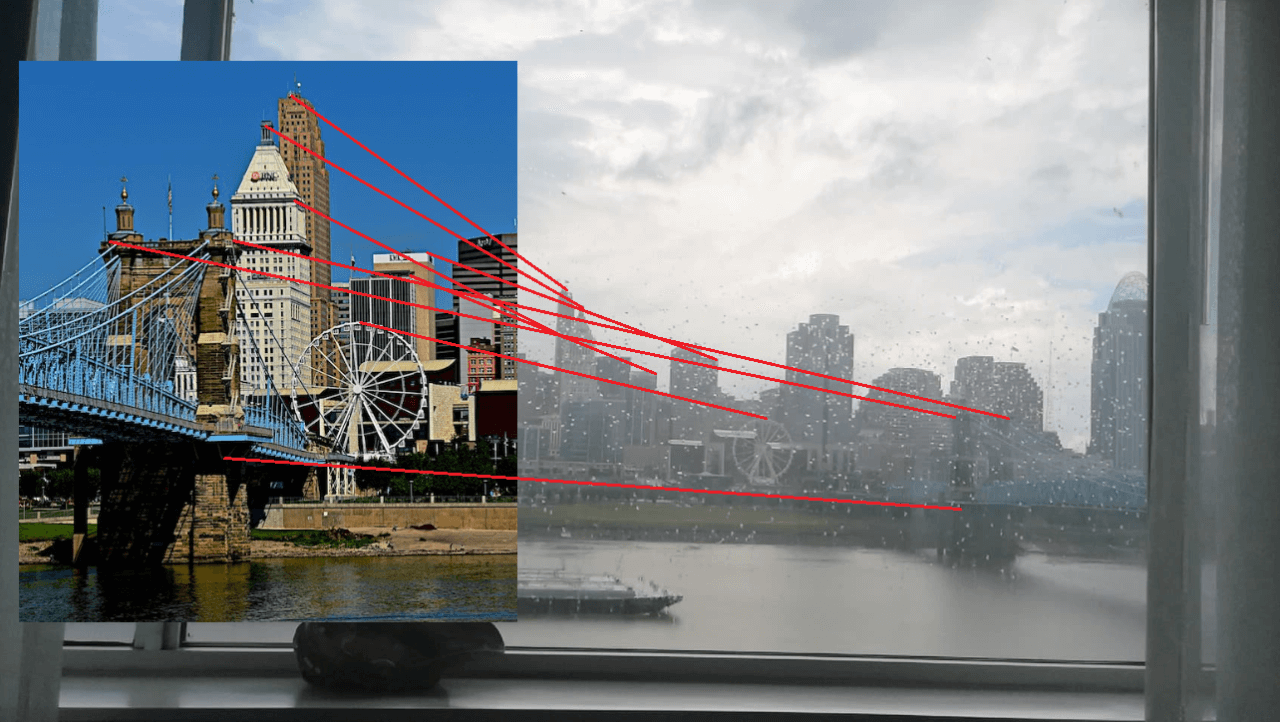
He then compared the images and to confirm the location, and using CCTV cameras then triangulated the position of the hotel. This whole process took less than 2 minutes

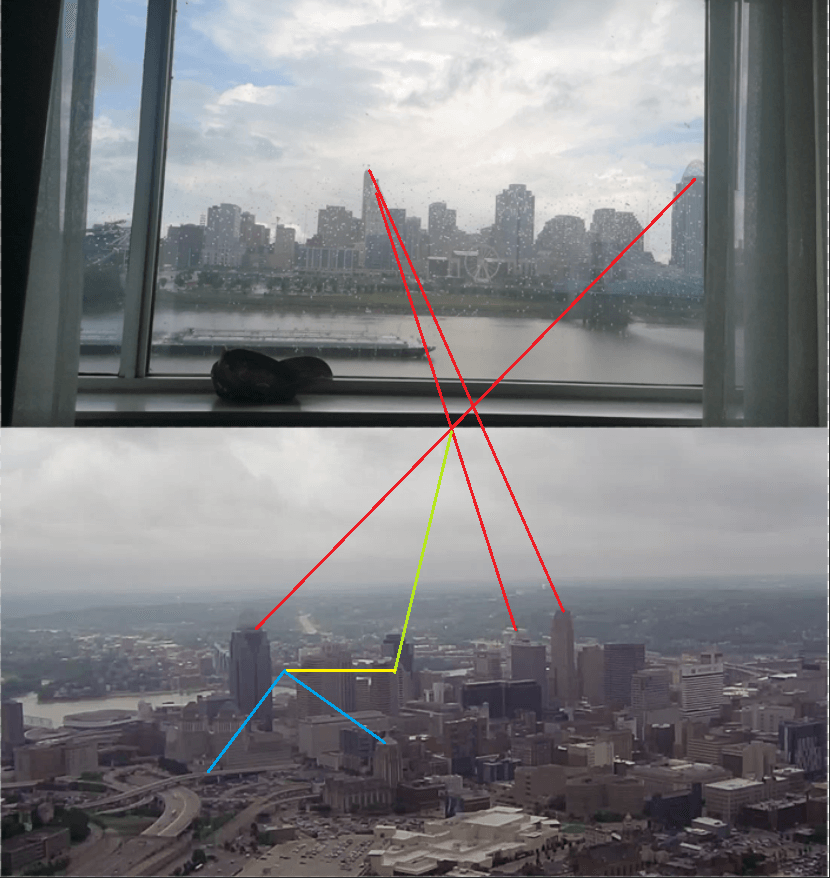
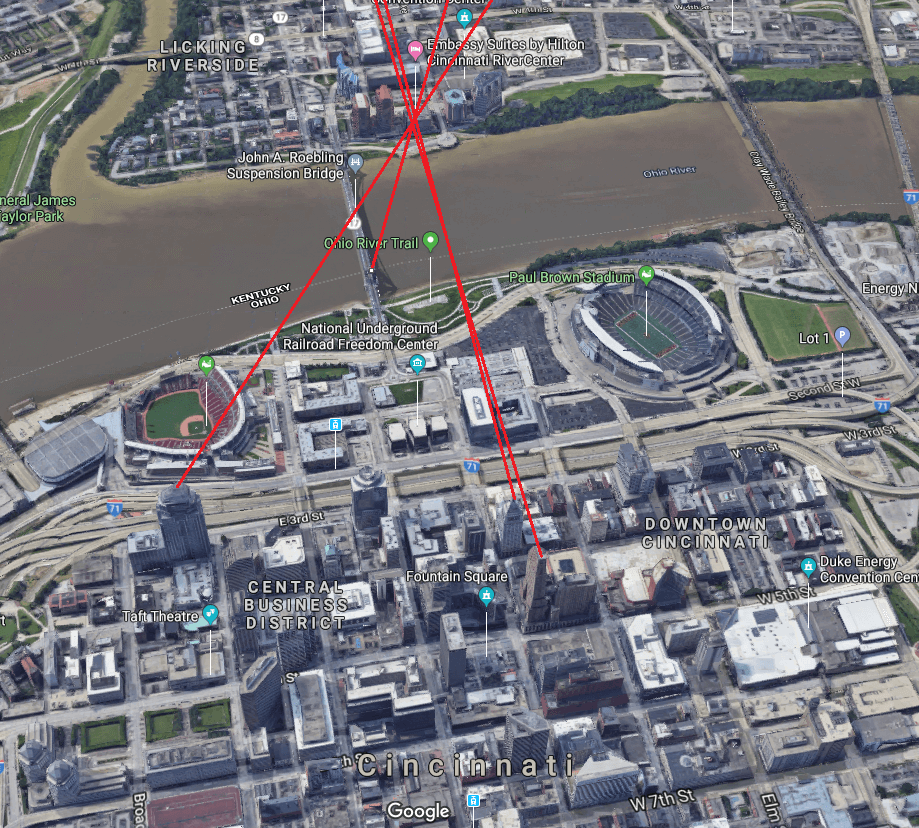
This process is extremely common, so be mindful about what images you post on social media, and if in doubt, don’t post or at least redact it.
Data Dumps and Username Searches
The next step is trying to establish where you are exposed in Data Dumps from any third party services and applications that have been breached. Attackers will use these to understand how you construct passwords and whether you reuse passwords. They will then use the information to perform account takeovers known as ATO’s. There are many useful resources to assist you. Here are a few well known ones:
- https://haveibeenpwned.com/ - will only show where your accounts have been involved in a breach. It's a free service and requires no sign up. However, it is recommended that you subscribe to receive alerts.
- https://hacked-emails.com/ - requires you to sign up, but will show where accounts and passwords have been breached.
- https://spycloud.com/ - requires you to sign up and will show where accounts have been breached. This is a paid service
- https://ghostproject.fr/ will show for free where your accounts are breached but requires you to sign up to see all the results. This is a free service and limited to the Collection Dumps only.
After reviewing your exposure in data breaches, the next logical step is to understand how an attacker might enumerate your usernames. There are a few really interesting tools that can provide visibility quickly. https://github.com/sherlock-project/sherlock (Sherlock Project) This tool is extremely useful for finding usernames extremely quickly, it does, however, require some technical knowledge of Linux and Python, but it is really easy to clone the repo and use.

Figure 7: Image from Sherlock, checking one of my usernames. For the non technical user, I recommend the following online service: https://usersearch.org/ UserSearch.org is an extremely quick and easy service that searches over 45 top websites. You can find online accounts by searching usernames, emails and even phone numbers.
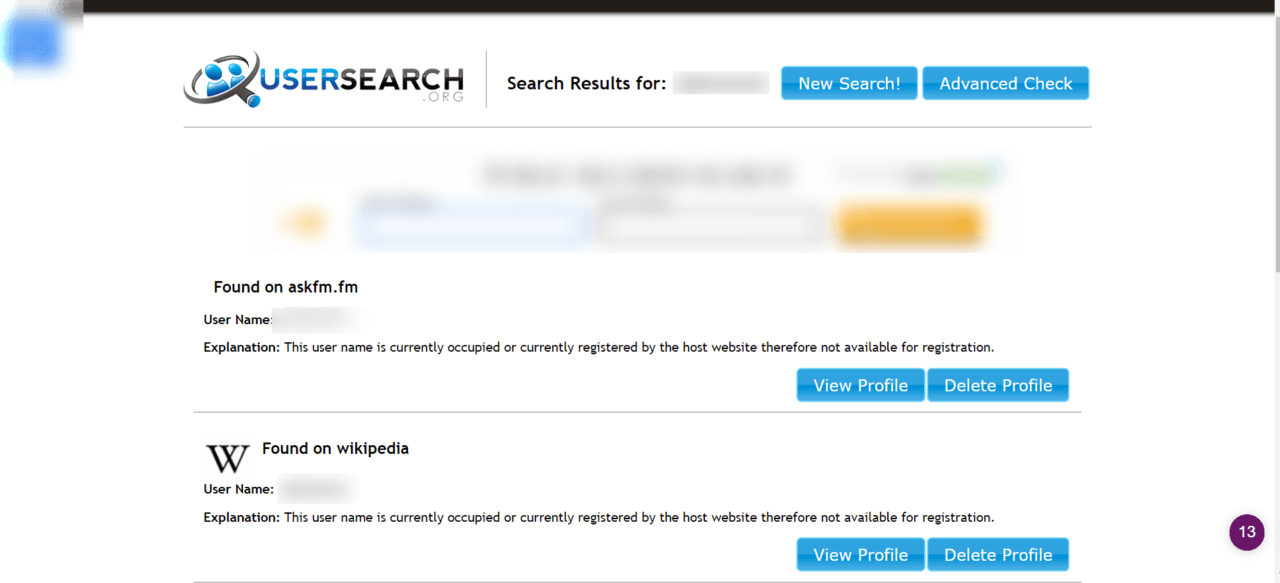
Figure 8: Image from UserSearch.org checking one of my usernames. As highlighted earlier, it’s the aggregation of information that can be gathered on a target that poses the greater threat. Performing OSINT helps quantify the actual exposure and provides an insight into how an adversary might target you. In the next article, we will discuss how you can start to analyse this and develop a strategy for denying and deterring an attacker. Other useful resources you should review:
- https://github.com/jivoi/awesome-osint
- https://github.com/twintproject/twint
- https://osintframework.com/
In Part III, I will cover how to develop an OPSEC strategy using the information harvested from OSINT. This will include:
- Privacy vs Anonymity
- Deleting yourself from the internet
- Covering your tracks (reducing your footprint and anti-tracking techniques)
- Tools and Services
- Creating Sock Puppets and Pseudonyms
- And much more.
***UPDATE - PART III is now live here: https://www.tripwire.com/state-of-security/security-awareness/opsec-everyone-people-something-hide-part-3/
About the Author:
From a background of threat intelligence, social engineering, and incident response, Stuart Peck is the Director of Cyber Security Strategy for ZeroDayLab. Stuart regularly delivers threat briefings to FTSE-level executives and directors throughout the UK and Europe. Passionate about educating organizations on the latest attacker trends facing business today and how to combat them, Stuart’s key areas of expertise include: the dark web, social engineering, malware and ransomware analysis & trends, threat hunting, OSINT, HUMINT and attacker recon techniques.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor and do not necessarily reflect those of Tripwire.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

