
Technology has become the lens through which we perceive and experience day-to-day life. Take the smartphone as an example. What used to be a technological rarity and business-oriented tool has become the nexus of our personal and recreational lives. Pew Research Center has found that more than three-quarters (77 percent) of Americans currently own and use Android, iOS, or Windows mobile smartphones. And they found that the percentage is even higher among younger generations. An astounding 92 percent of 18- to 29-year-olds own smartphones. Of course, smartphones and other portable devices help us access the Internet, which facilitates communication and seamless, simultaneous, and instantaneous sending and receiving of information. We also use it to make purchases.
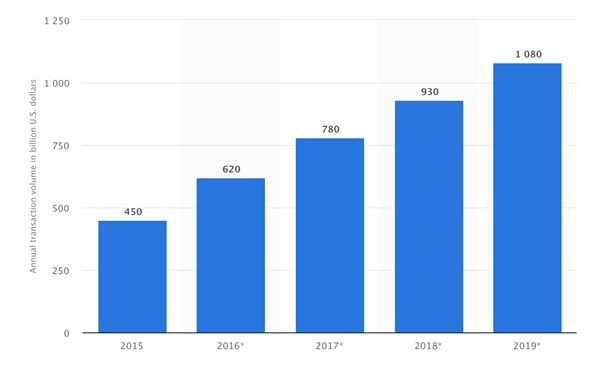
Source: Statista In 2017 alone, U.S. citizens spent approximately $780 billion in mobile payments on smartphones, tablets, and other portable devices. And due to the increased frequency with which we’re using mobile shopping apps like Amazon and eBay, peer-to-peer payment services (i.e., PayPal), and even in-app purchases, this figure is expected to surpass $1 trillion in 2019. For all the benefits (and convenient shopping) the Digital Age has afforded us, the Internet is also a major cause for concern regarding privacy and security. Although a lot of the information that we send and receive over the World Wide Web is innocuous and of nominal importance, we exchange a ton of sensitive data, too. For instance, data from 2016 showed that 62 percent of Americans managed their finances primarily online rather than in-person. This means lots of credit card and loan applications sent, accounts logged into, balances checked, credit reports requested, and so on over the Internet every day. Even if we only consider banking and finance, that’s a lot of sensitive information – current and past addresses, birth dates, and Social Security Numbers – sent across the web. We often assume our sensitive data makes it from point A to point B without interference. But in reality, the Internet can be easily misused. If recent news reports are any indication, the safe transmission of our sensitive digital data is not guaranteed. The very real possibility of getting hacked, having sensitive information captured, or even having one’s identity stolen is something that we should all be prepared for. But relatively few people have taken steps to protect their digital livelihoods. In fact, individuals usually only take steps to deter the ever-present threats to their digital privacy after they have been the victims of a hacking or another cyber attack. Why are people so reactionary when it comes to their privacy? Should we be taking our privacy more seriously in this inherently-digital age?
Hacks, snaps, and selfies: Welcome to the Digital Age
Before we discuss issues about privacy, let’s take a second to really digest what it means to be part of “the Digital Age.” Also commonly referred to as the “Information Age,” “New Media Age,” and “Computer Age,” the Digital Age is a place in time that accurately reflects the time that we currently find ourselves in. It’s characterized by the shift to “an economy based on information technology.”
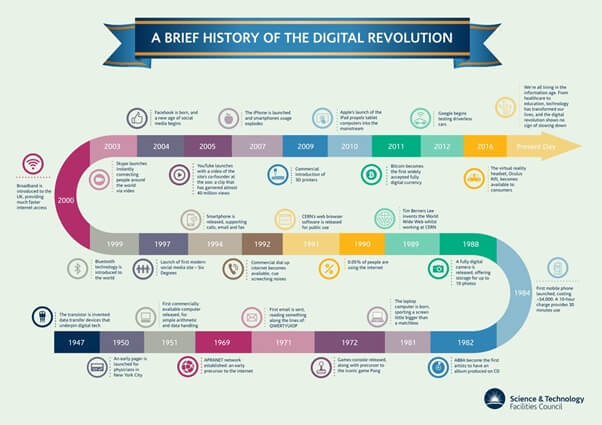
Source: Science and Technology Facilities Council The birth of the Digital Age was the so-called “Digital Revolution.” Whereas the Industrial Revolution saw the extensive use of machinery for the mass-production of goods and availability of services, the Digital Revolution marked a shift from mechanical machinery to digital technologies. More specifically, the Digital Revolution saw us beginning to mass-produce countless consumer products on a global scale. The use of circuit boards, computers, and eventually the Internet also became commonplace. The digital landscape has evolved quite a bit since the Digital Revolution. The vast majority of our personal devices are extremely portable. And they’re continuously connected to the Internet, allowing us to transmit personal data around the globe on an almost continuous basis. Similarly, social media has greatly increased the amount of personal data we share. But even before Facebook and Snapchat existed, there were plenty of digital avenues that users could share data on. What happens to that data once it leaves our devices? As it turns out, the data we share is stored in databases that are scattered across the globe. For the most part, we don’t worry about the security of our data, But it’s important to note that each of these databases is a point of vulnerability when it comes to data security and personal privacy. That’s because data is not only vulnerable where it's stored. For every bit of data two people share, both the sender and the receiver have online accounts (i.e., email, social media, cloud storage, or some other digital channel) that can be compromised or hacked. In case you underestimate how much data we share, the following figures will give you some perspective:
- About 269 billion emails were sent and received every day in 2017.
- Seven in ten American adults – and 89 percent of Americans from 18 to 29 years old – are using at least one of the major social networks.
- There are approximately 6,000 tweets posted to Twitter every second. This equates to about 350,000 tweets per minute.
- Snapchat users post nearly 9,000 photos to the platform every second.
- There are currently almost 230 million Facebook users in the U.S. and 2.13 billion Facebook users around the world.
- Facebook users post over half a million comments, nearly 300,000 status updates, and 136,000 photos to the platform every minute.
It’s not the status updates, comments, and selfies you post to your social media accounts that make you vulnerable. Or not exactly. But every time someone accesses his or her online account, there’s a possibility that someone will hack them. Worse yet, we've seen password databases breaches that prove that a person doesn’t even need to be actively accessing an online account via an Internet-connected device (ICD) to have his or her security compromised. In fact, a billion users had their Yahoo! email accounts hacked just recently. Email addresses are a popular target of hacking, and it makes a lot of sense for a hacker to want access to your email account. After all, we use our emails to create and manage all our other online accounts. Therefore, if someone hacks into your email, then there’s a pretty good chance they can also access your social media accounts, school and work accounts, Google and Apple accounts, banking and financial accounts, and so on. To make matters worse, most people use a single password for all their online logins, meaning that getting the password to just one online account often means gaining access to most or even all of them. Granted, many of us don’t keep much sensitive data out in the digital open. But there have been a lot of people brought down by damning information uncovered through account hacking like the Ashley Madison scandal of 2015. We’ve also seen that it’s a bad idea to assume that one’s cloud storage account will keep private photos safe from prying eyes indefinitely. This has backfired on numerous celebrities, including A-listers Jennifer Lawrence and Scarlett Johansson.
Why isn’t security a priority?
The most logical solution to the issue of privacy would be to increase your security. Adopt a complex password that isn’t simply a word in the dictionary. Take advantage of two-factor authentication or biometric security protocols when possible. Implement firewalls that make ICDs more secure as we use them. However, research shows that we aren’t actually taking the initiative to protect our online privacy until it’s too late. But why? Most of the hacks we see happening today weren’t as big an issue – or, in some cases, an issue at all – in the earlier days of the Digital Age. In 1995, a hacker couldn’t commandeer someone’s Google account by stealing his or her password because nobody had Google accounts, Twitter accounts, Facebook accounts, or numerous ICDs lying around their homes at that time. As our Internet usage became more intensive and gave rise to additional security vulnerabilities, there was a collective failure to accommodate the increased risk by commensurately escalating our security practices. Another inherent problem is that most people prioritize convenience over security. While fingerprint sensors and facial recognition have made more robust security protocols accessible and mainstream, the most effective deterrents for hacking require that we add more steps to the login process. In other words, it requires us to sacrifice some convenience. Two-factor authentication, for instance, requires a user to provide his or her password to trigger an email or SMS message with a temporary code. In turn, the user must provide this code as a follow-up to the password, serving as additional proof of identity before gaining access to the account.
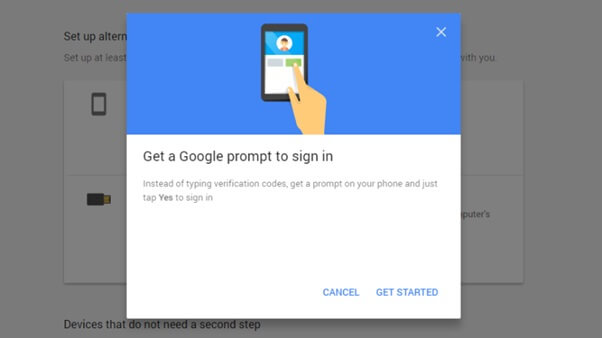
Source: Google The entire process takes only a moment longer than using just a password, and it offers a much greater level of security. Unfortunately, most users don’t use two-factor authentication because they see it as being more complicated (and taking much longer) than simply entering a password. The tendency for many people to prioritize convenience over security isn’t a new phenomenon. Before the Internet became the best thing since sliced bread, our forebears showed this tendency by choosing postcards over letters. And we continue to show it anytime we’re willing to pay a premium for convenience and ease of access.

Source: Frank on Fraud When it comes to security breaches, there’s a popular misconception. People think, “That would never happen to me. Why would hackers target a random, inconsequential person when they can focus their energies on politicians, celebrities, and other persons of interest?” For one thing, the people many of us would assume to be obvious targets for cyber attacks are actually the ones who are best prepared for them. Although hacking a public figure is far from impossible – just ask former presidential candidate Hillary Clinton – it’s more likely that such individuals have taken steps to minimize the likelihood that their privacy would be compromised. They’ve probably implemented more robust security than the average John Smith or Jane Doe would. By comparison, the average person probably doesn’t know much about cybersecurity or the countermeasures they can take to prevent breaches of privacy, which makes the seemingly inconsequential people the easiest targets. Let’s not forget that as security methods become more robust, hacking methods become more advanced, too. Today’s hackers are more experienced, organized, and have more funding than ever before, making them increasingly efficient when it comes to finding chinks in the digital armor. In 2018, many security experts have begun turning their focus to cloud storage, which is a logical target for hackers who are after your data. However, technology is ever-changing, so the threats we see today are likely to be quite different from the threats we might see ten years from now. Finally, it’s worth noting that hackers usually play the long game. For this reason, many of us will downplay the threat of a security breach since the consequences of getting hacked — if there are any notable consequences at all — may not become apparent until many years later (if ever). But is this a gamble anyone really wants to take?

About the Author: John Mason is a Cyber Security/Privacy enthusiast working as an analyst for TheBestVPN.com. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

