
In this final part of the series, I discuss why everyone should consider reviewing their OPSEC (Operations Security), not just those with something to hide. If you haven’t read the previous articles then please check them out first (Part I & Part II), as they provide key background information about the techniques discussed in this post. The processes described are designed for both technical and non-technical people, especially those who are concerned about their digital footprint and how it might be abused. As this is the last article in the series I asked the wider infosec community for their views on OPSEC, and their quotes are highlighted throughout this article. In the last article, we covered how to “Discover” information about yourself, in this one we will detail how to “Analyse” your information to uncover any potential risks and then provide actions for “Denying” and disrupting “the attacker”. The ultimate objective of OPSEC is to prevent sensitive (referred to in this article as confidential), information from falling into the hands of an adversary, primarily by denying them from uncovering and gaining unauthorised access to your data. But there are other use cases, such as:
- Preventing an adversary from identifying you, or attributing your actions
- Preventing an adversary knowing your movements or location
- Preventing an adversary from uncovering information about a “secret” project/operation
- Preventing an adversary learning about the systems and controls we have in place, especially how robust (or not), they are.
So once you have discovered (identified), your information the next step of the process is to Analyse this for any risks.
Analyse
“From one thing, know ten thousand things” - Miyamoto Musashi 1584-1645 So you’ve done an initial scrape of your digital footprint, maybe done some digging into a project you are working on, but now what? One of the most important steps in conducting OPSEC is the analysis of the potential risks to the data you are trying to prevent the adversary from obtaining/seeing. Understanding how an attacker may gain an insight into your movements or access to data they can later use against you is vital in ensuring that the correct countermeasures are deployed. There are various methods for doing this, some of these are going to be covered in this post, but be mindful that not everything detailed will work for every scenario. Just as organisations regularly perform risk assessments or business impact assessments to understand exposure to certain threat scenarios, it is equally important to perform a personal risk assessment on oneself on a fairly regular basis.
“As a security researcher once your work starts to get a lot of media attention, people and journalists want to know who is behind the work. If you want to keep a good separation between your work life and your private life OPSEC is essential” - @fs0c131y (Elliot Alderson)
The first step is to quantify the potential risks of the data discovered on your digital footprint, you should ask the following questions to threat model your exposure:
- Should this information be public or private?
- What is useful to an attacker? What information could compromise me?
- When was this data posted? When does this become a problem?
- How would an attacker compromise me? How would I know?
- Why would an attacker want to compromise me?
What and When? And Considerations for Public/Private info.
The next step is categorising the information that is sensitive, identifies you, could be used to compromise your accounts, or allow an adversary to build a profile on you. Some examples include:
- Email(s)
- Phone number (mobile/cell, number could be at risk from SIM swapping)
- Address
- Social media profiles
- Passwords
- Financial information
- Usernames/ handles / gamer tags
- IP addresses
- Mac addresses
- Images (especially those of your house, family, or selfies. Also be wary of metadata in images EXIF covered later).
- Personal interests/hobbies (especially for profiling you)
- Date of birth (partial data of birth is even a risk)
- Devices and OS versions these are captured by social media sites and are discoverable by adversaries
- Posts of movements (such as planning to attend X event in future)
- Location data shared with third parties, especially fitness apps
- Information friends/family/colleagues have shared about you on their social media profiles
- Work information such as badges/passes/company equipment
- Public records (electoral / voter register), birth certificates
- DNA information held by third parties
- Police/government records
- Data dumps/ pastes /breaches
“When you’ve been a victim of cybercrime, be it cyberstalking or NCP, you learn how valuable privacy is. You learn to use good OPSEC out of necessity, but sadly- the damage has often already been done. I wish more people would think of OPSEC more when online, because prevention is worth its weight in gold.” - @BadassBowden (Katelyn Bowden)
You may want to start building a brief personal classification table to help you define the information that is contained within your digital footprint; there is nothing that focuses the mind more than realising the amount of sensitive information you have shared with third parties! This is a small investment in time that will have a massive payoff downstream, not to mention help with developing preventive measures for the future.
| Confidential (should be private but currently public) | Confidential- Public (can’t be made private) | Confidential- Private (currently private) | Non-Confidential (currently public) |
| This category is for newly identified information classed as confidential- where this is useful for an adversary. Every effort should be made to make private and restrict access to this information. | This category is for information classed as confidential which is public but cannot be made private. Some examples include data dumps, pastes etc. Countermeasures should be applied to this data. | This category is for information classed as confidential where you have been able to remove the information, modify, or make private. | This category is for data that is public and that poses a limited risk. |
Figure 1: Classifying our information is vital to developing our personal risk appetite. As part of the classification process, try to establish when this information was posted. The newer the information the more relevance it has and therefore the more risk it can expose you too. However, do not disregard older information as the past has a way of coming back to haunt us, eventually! As part of this process, you will be able to identify what information you are comfortable being public. Categorising your information naturally reduces your risk appetite and helps adjust attitudes to information sharing. I’ve produced a simple process below to help visualise the thought process.
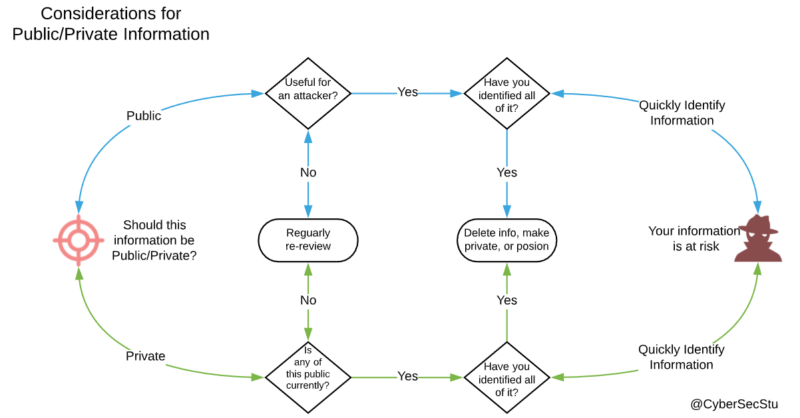
Figure 2: Public or Private? You decide! Even if you don’t have a social media profile you can be exposed by your friends and family posting images and information about you, or if you are lucky enough to present at meetups and cons, this information may also be posted. Time for a case study, on how not to perform OPSEC.
Mini case study:
So a few years ago I had spent a long time identifying and deleting images of me from the internet, got rid of my real Facebook account, and had managed to get my digital footprint down to 2-3 images. I was pretty happy, it took over 5-6 months of work, but I had got my OPSEC under a semblance of control. Then I gave a talk on OPSEC lessons from WWII propaganda at a meetup in London. I forgot to mention at the beginning of the talk not to take any photos, within minutes there were 50+ photos on Twitter, Discord, LinkedIn, even Facebook. At the end of the talk, I counted over 100+ photos, one talk and the hard work I had put in was over! It had become a game for some, especially in the community I run, to scrape photos of me or post them and create memes at every talk I did after this one. The irony: talks about OPSEC; commits OPSEC fail! I quickly decided at this point those images were public info, so unless I decide not to give another conference talk. I was happy for these to be public, as the information I was looking to deny the adversary were the links to my operational “sock puppet” accounts, not my public persona. I was focusing on the wrong information at this point, so decided to rework my strategy, and this is what led me to develop the process discussed in these articles.

Figure 3: Protecting everyone else's opsec, apart from mine! Even months down the line, someone made a mosaic of me using the small number of images of me online. Because they could I guess!
Figure 4: Stu-Art!
How and Why?
All this information is incredibly valuable to an adversary, whether it is an advertiser trying to sell you better, cheaper, faster services through abusing privacy and online tracking, or an attacker who’s trying to steal your identity or gain unauthorised access to your systems. Now you’ve classified the risky information, what should you do next? The next step is to try and get inside your adversary’s head, to understand how they might use this information to their advantage and most importantly, why? You can do this by asking the following questions;
- How would an adversary likely target me?
- How is my information exposed?
- How can I further restrict access to my data?
- How do I disrupt an adversary obtaining my confidential information?
- How would I know if I’ve been compromised? How quickly could I react if I was?
- Why is this information useful to an adversary?
- Why would they want to target me specifically? (This one is very difficult to answer in most cases)
The key to this stage of the analysis is to understand the threats that your confidential information faces. Try to define how your information may be used to uncover more details about you or pattern of life. It is important to analyse all of your information, look at what might be useful for an attacker in each photo, social media post, blog post, YouTube video, podcast, etc. I recently competed in and was part of the winning team for the TraceLabs Global Missing Person’s CTF (Team TheManyHatsClub), where the objective was to help find information on real cases of missing people, usually ones that law enforcement is struggling to solve. Our key to winning the competition was when we found a social media profile, we reviewed every post, every image and pivoted off this information to find other social media accounts, family members, previous locations, habits, specific identifiers (tattoos, marks/scars) etc. We were even able to find family members of people with no social media profiles, and use them to find information about our target. Unless you do this on yourself, you don’t know how exposed you are. In 6 hours we found significant information on some of our targets that will be useful for the families and the cases, but this information would also be extremely valuable if we were attackers! You have to view your information through the eyes of an attacker by asking yourself: “If I were trying to target me, how would this information be useful?” Maybe in isolation not very, but when you aggregate everything, a picture begins to form, and this is the key to unlocking the puzzle.

You need to view your information as a whole and not just as individual items. Visualising it on a virtual corkboard, using tools like LucidChart, Maltego, Draw.io helps you to understand how an attacker might exploit your digital footprint.
The Process of Analysis
The example below represents some of an online digital footprint and provides a good visualisation of the areas an attacker could target you and build a picture. I’m pretty sure I qualify for a tinfoil hat after producing this! When conducting the analysis, think about where passwords, profile pictures, accounts, emails etc. might be linked to other accounts. As soon as you start down this path you’ll draw links that you consciously didn’t realise existed. This process is both enlightening and mildly terrifying at the same time, but extremely valuable!
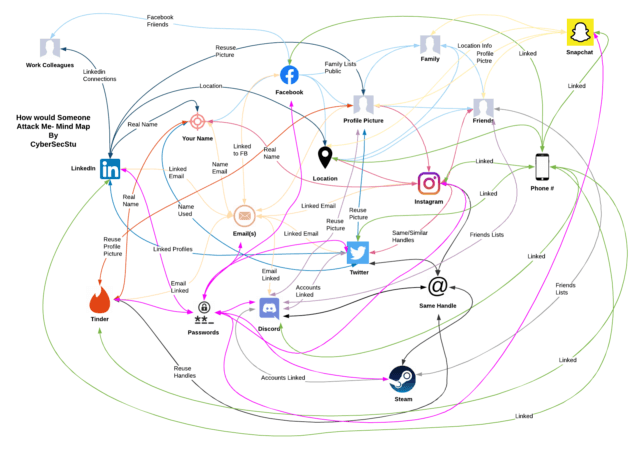
Figure 5: Rough mindmap of data. A bit messy but you get the idea! To expand this further you could include ISP’s, third-party sites, email providers, other sites like YouTube/Twitch, podcast apps, Spotify, online records such as government records, ”shoe size”, the list is literally endless! Once you have mapped how an attacker could obtain information about you, then you want to start working out how do you deny the attacker.
"I liked having my OPSEC because it kept my work separate from my personal opinions and Twitter, specifically. An irate jackass ex-reporter decided to have a temper tantrum and now I can't ever speak as openly as I did before." --Anonymous.
Deny
The final, and arguably the most important step of performing OPSEC is to deny the adversary. There are two states of performing OPSEC, preventative measures, such as actions you should perform when setting up a new online identity, like not mixing legends for example, and what I call Active OPSEC for historical and live data - usually relating to a real identity or project that you’re trying to protect and prevent an adversary obtaining. The process for preventative and active OPSEC are almost identical but the context and application differs. Preventative is easier to perform as you are working with a blank canvas, whereas active is a little more difficult and comes with a tonne of caveats!
Active OPSEC
“OPSEC is like sex.. everyone thinks they are really good at it but they can’t possibly all be right… and practice won’t make you perfect at it, but it’s worth making the effort”- @RayRedacted
There are many stages (we’re discussing four), to denying attackers access to the information you have discovered and analysed to be confidential. Some of the advice detailed in this section will not be applicable to your situation, and may require to use these as guidelines to build your own specific process. The full OPSEC process discussed is detailed in figure 6 below:
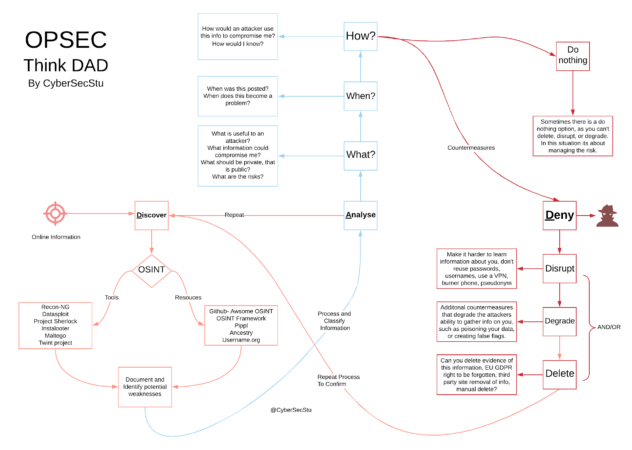
Figure 6: OPSEC process (Discover, Analyse, Deny)
Disrupt
The first set of tools you have is to deny your attacker and disrupt their information gathering and recon on you. There are many methods for doing this, but by analysing your data and the relationships between accounts, you can work to prevent the attacker from making those connections. Some options, starting with the more obvious, include:
- Ensuring all passwords are completely unique, using a password manager
- Using multiple password managers, offline for critical accounts, online with 2FA for accounts you use on a daily basis, one for pseudonyms using random addresses again
- Ensuring that you have multiple email addresses for accounts, maybe use a password manager to generate random character emails such as [email protected]
- Ensuring that email addresses don’t contain any identifiable information about you, such as year of birth, important dates etc.
- Use an app for 2FA authentication rather than SMS which can be used to identify you, not to mention SIM swapping risks. If the only option is SMS, this is better than no 2FA, but do consider the risks. Consider having a second phone for this though.
- Have Pin or passphrase added to all of your phone banking, ISP, Mobile accounts etc to prevent Social Engineering attempts
- Look at https://2fanotifier.org/ for understanding what accounts have 2FA and how to set up ones that don’t, a really useful app.
- Check where emails, usernames etc. have been found in breaches, sites like haveibeenpwned and dehashed are pretty good for this. Ensure passwords are unique across these sites, consider which accounts should be deleted.
- Use Brave Browser and DuckDuckGo over Google Search/Chrome
- Use a VPN to mask your real IP address, especially when signing up to sites, also you can create profiles in some providers to create false flags, for example sign into Twitter using XYZ profile and always from Sweden.
- Check whether your current VPN leak metadata or logs. This is an interesting tool https://www.comparitech.com/privacy-security-tools/dns-leak-test/ not sure about the VPN recommendations though!
- Good VPN that respects its users’ privacy and anonymity is Mullvad, they accept crypto payments, and even payments by cash in the post!
- Ensure Discord, gamer, social media handles are unique where you don’t want to make a direct connection to public personas, also ensure these have unique profile pics and emails associated to them.
- Use TOR if you are worried about protecting your anonymity, but don’t use this all the time as it’s not practical.
- Burner phones are a good option, but realistically only should be used in certain situations where you are convinced that you are at risk. Be wary of sites offering one-time use SMS as these messages, whilst useful, sometimes contain info about the accounts you use to sign up.
- Be careful about what apps you download, and also ensure if you are using an android phone you change your Advertising ID under Google Settings, to mess with the advertising algorithm.
- Turn off location tracking on phone, maps and all apps, and use a VPN when browsing on the phone and especially when using public Wi-Fi.
“OPSEC is important for everyone but if you are a high profile individual such as a CEO of a large multinational it becomes even more critical. You need to know what information is out there on you, your adversaries sure do.”- @LisaForteUK RedGoatCyber
Degrade
The next set of tools you have at your disposal is to degrade an adversary’s ability to discover information about you. One method is to poison your information or to leave a fake breadcrumb trail. Most importantly you want to create no trace between your online persona and information you want to protect.
- Ensure that you poison your data on sites you sign up, or sites you’ve already shared your information with, such as:
- Not using real Date of Birth (DoB), but also making sure DoB entered into sites is random each time
- Not using your real name or full name
- If you don’t have to use your real location, then don’t.
- Security questions if these are required, use the password manager form fill function to generate a random string this will be saved against that account usually under notes.
- For profile pictures, if a public one is required then be careful about which one you use, for all other accounts, thispersondoesnotexist.com is fine, or a random picture of a cat, a dog, or an inanimate object is fine. Also, ensure these are unique across sites so they cannot be linked via reverse image searching
- Use privacy settings to ensure that email addresses are made private/hidden from public, especially on Twitter where password reset shows part of your email!
- Use an email address for one time use when signing up to sites, ensure this cannot trace back to you, i.e. sign up with VPN and leave no identifying markers, such as names or other personal details.
- Plant landmines on your PC, email, and file sharing apps, use canary tokens to generate files such as fake password lists, bank statements, personal images etc. which will notify you if an attacker is targeting you when they open them.
- Even better create an enticing account and use the above as a honeypot. Just send yourself 100’s of emails, all of them with canary tokens as attachments, but it’s important that you ensure this email is not used for anything else.
There are many other techniques but these are some of the easiest to execute. I may post some more detailed and technical ones in the future.
“OPSEC isn't just a buzzword or something you know of, OPSEC is a state of mind, having good OPSEC is as close to being a Ghost, it is hard, but with the right understanding it is possible and highly effective in any industry” - @thecyberviking
Delete
This stage is vital and should be reviewed on a regular basis. I will add a caveat that some information can never really be fully deleted off the internet. If you are unlucky and have posts, or articles included in the internet archive then this has to remain in your personal threat model. However, you should delete what you can. Here are some tools and services you can use to help you.
- Firstly you want to find the online accounts you no longer need, there is a useful service that can help you find the delete links to your online accounts you know about https://backgroundchecks.org/justdeleteme/ it’s pretty useful, but these are the ones you know about.
- For accounts you don’t know about, there is a useful tool called deseat me. It does come with some privacy concerns, but if you are looking to delete your accounts quickly, including the email you are using for this tool, then it’s appropriate.
- If you are in the EU then you can use the right to be forgotten act under EU GDPR, where you can send subject access requests to remove data about yourself from sites that hold your data. Be wary that organisations may have a legitimate reason for processing this and can refuse.
- Remember it is better to delete a social media account rather than deactivate it, the latter means the account is still technically live and searchable.
“OPSEC is important to me, because as a parent, I feel like by keeping my data private, I’m also keeping the data of my children private. I don’t want them logging on in a few years to discover that their address, every photo from birth, and every embarrassing moment is already online. I’m building a foundation of privacy for them.” - @BadassBowden (Katelyn Bowden)
Do Nothing
If all else above has failed, there is always the option to do nothing and accept the risk, while you continue to find another method to resolve. Whilst this is not ideal, there are many circumstances where data cannot be deleted, degraded or disrupted, so this is where you have to work out the exposure, sensitivity of the data and how this may affect you. Information that falls into this category is, in most cases, usually public and non-sensitive.
Summary
We all have a lot of information that can be harvested on us, but by following the steps given in this article as well as the previous ones, we can all tidy up our digital footprint and make it a little harder for attackers to gain access to the information we are looking to protect. OPSEC is a mind-set, a way of thinking about how we prevent information falling into the hands of our digital world ‘enemies’, it's also about how we hide our movements, protect our digital assets and our identity. This is not a one-time exercise, if you are serious about protecting private information, it's a way of life!
About the Author

: From a background of threat intelligence, social engineering, and incident response, Stuart Peck is the Director of Cyber Security Strategy for ZeroDayLab. Stuart regularly delivers threat briefings to FTSE-level executives and directors throughout the UK and Europe. Passionate about educating organizations on the latest attacker trends facing business today and how to combat them, Stuart’s key areas of expertise include: the dark web, social engineering, malware and ransomware analysis & trends, threat hunting, OSINT, HUMINT and attacker recon techniques. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

