
A new phishing attack is using fake non-delivery notifications in an attempt to steal users' Microsoft Office 365 credentials. SANS ISC Handler Xavier Mertens discovered the attack while reviewing data captured by his honeypots. The attack begins when a user receives a fake non-delivery notification from Microsoft such as the one shown below:
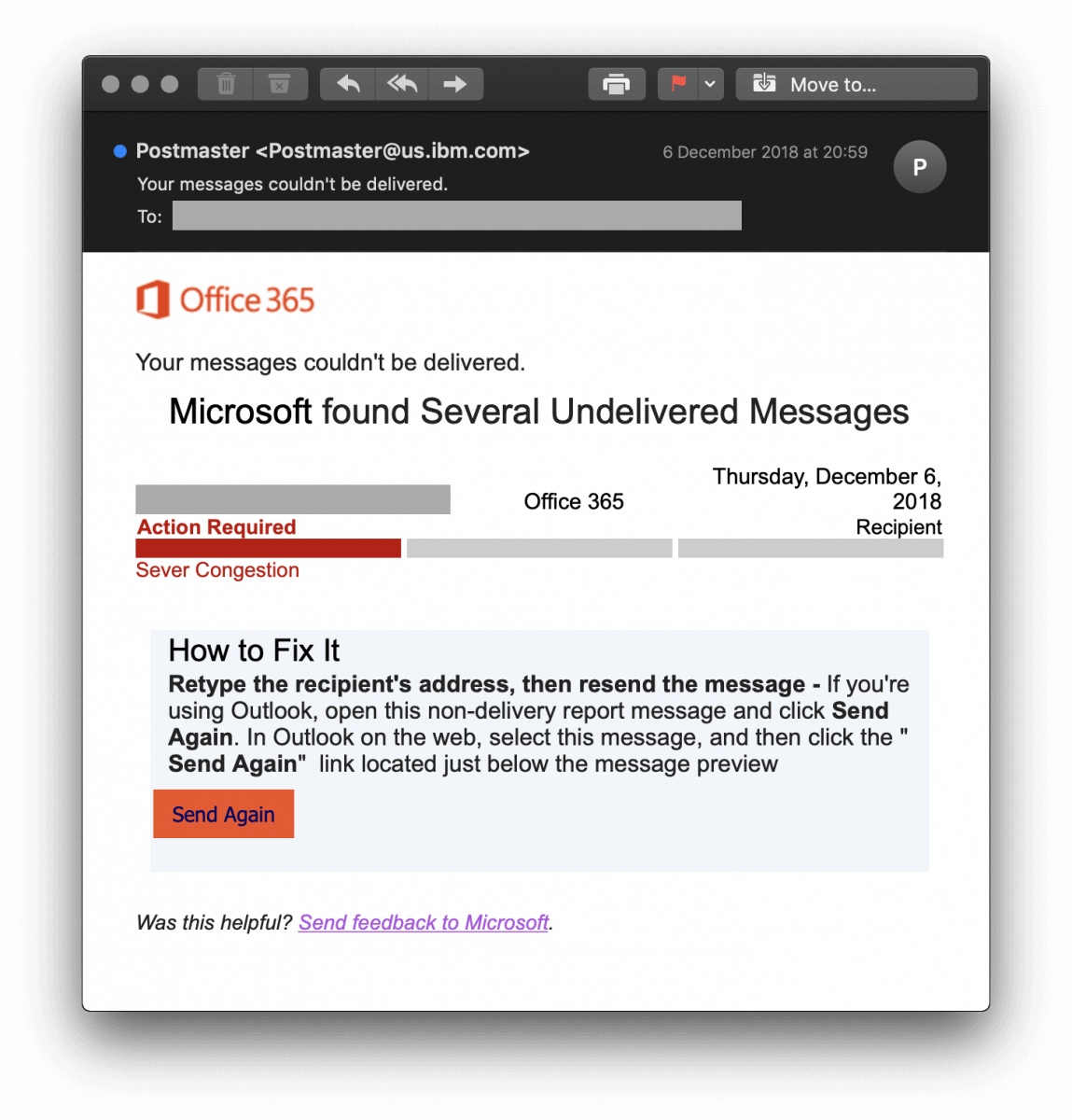
A screenshot of the fake Office 365 non-delivery notification. (Source: SANS ISC) For the sake of comparison, here's what a legitimate non-delivery notification for Office 365 looks like:
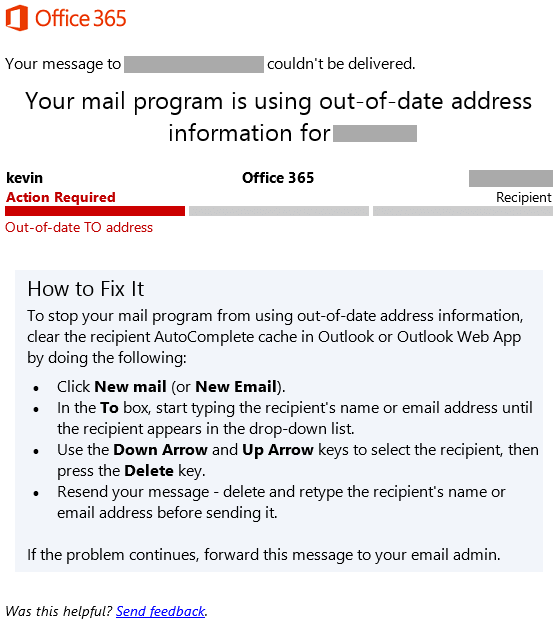
A real Office 365 non-delivery notification. As you can see, the real notification provides instructions through which the user can delete out-of-date address information for their contacts before attempting to resend the message. By contrast, the fake notification instructs users to simply click the "Send Again" button included in the email. Doing so redirects the user to a phishing site that impersonates the real Office 365 login. The URL for the phishing page ends with *[email address] and incorporates this information into a dialog box designed to steal the user's password for their Office 365 credentials.
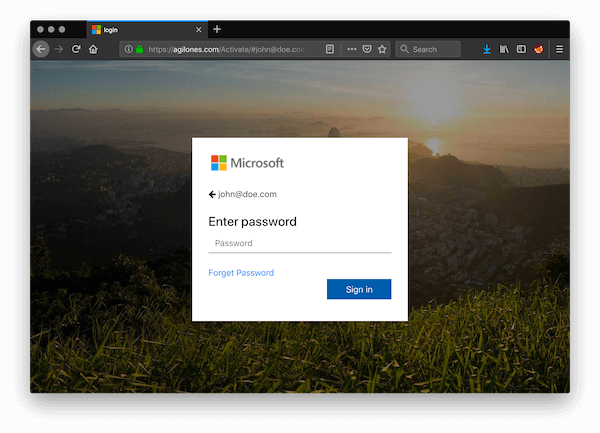
Screenshot of the Office 365 phishing site. (Source: SANS ISC) Once a user enters in their password, a JavaScript function called sendmails() sends off their information to the attackers and then redirects them to the official Office 365 login page. This isn't the first time that phishers have preyed on Office 365 users. In 2017, bad actors used a botnet attack called "KnockKnock" to primarily target Office 365 system accounts. Just a year previously, researchers documented an attack campaign where digital attackers incorporated Punycode into fake shipping alerts to trick users into sending over their Office 365 login credentials. Users can protect themselves against these types of email-based attacks by familiarizing themselves with the most common types of phishing operations. They should also consider protecting their Microsoft accounts with two-factor authentication (2FA). For instructions on how to enable this feature for Microsoft and other web services, click here.

