
Ransomware today is a billion-dollar industry. It’s crippled industries like healthcare. In 2017, for instance, WannaCry brought much of the United Kingdom’s National Health Service to its knees using the EternalBlue exploit. It was just a few weeks later when the NotPetya ransomware strain leveraged that same vulnerability to attack lots of industries.
These attacks and others like them were made possible by the ongoing presence of weak security controls and outdated operating systems. Looking ahead, it’s likely that malicious actors will continue to use ransomware to target a variety of industries. They’ll also probably go after individual organizations’ Point of Sale (POS) systems, as EMV chip cards have made data scraping nearly impossible.
PCI DSS to the Rescue
Fortunately, organizations can help to protect their cardholder environments against ransomware and other digital threats by achieving compliance with the Payment Card Industry Data Security Standard (PCI DSS). Created by the PCI Security Standards Council, PCI DSS is a set of requirements that organizations can use to protect their cardholder data. It also limits card issuers’ and banks’ liability in the event that a merchant suffers a data breach.
Introducing PCI DSS v4.0
As of this writing, it’s looking like the PCI Security Standards Council will complete version 4.0 sometime late-2021. Little is currently known about the new version of PCI DSS. But we do know some of the goals of the revised standard. These include the following:
- The revised standard will continue to meet the needs of the payment industry as technologies and solutions continue to change.
- PCI DSS v4.0 will seek to add flexibility and support additional methodologies for the purpose of achieving security. (Historically, the standard has been good at this. It’s introduced methodologies like file integrity monitoring (FIM) and vulnerability management (VM) in the past.)
- One of the primary goals of PCI DSS v4.0 will be to promote security as a continuous process so that in-scope organizations can remain compliant overtime.
- Lastly, PCI DSS v4.0 will continue to enhance validation methods and procedures that seek to help organizations with their compliance efforts.
Upon the completion of PCI DSS v4.0, there will be an extended transition period of time during which organizations can update to the newest version of the standard. The previous version, PCI DSS v.3.2.1, will remain active for 18 months upon the completion of v4.0. This will give organizations an opportunity to become familiar with the standard, supporting documents and other changes as well as plan their update process. To maintain compliance, organizations will need to complete their update plans by Q1 2024—the projected time when v4.0 will take effect.
Some Challenges to Consider
This transition period could exacerbate some challenges associated with obtaining and maintaining compliance with PCI DSS. First, there’s the threat of configuration drift. Organizations need to have a goal in mind for the environment and stick to it to make sure that systems in their cardholder environments stick to that desired state.
Second, organizations need to undergo the tedious task of demonstrating compliance to auditors. A lot of time and effort is needed to complete an audit depending on the number of assets, tests and controls. (Organizations need to have historical data to demonstrate compliance over time, after all.) Depending on their available resources and the size of their cardholder data environments, organizations might also not find it practical to audit all of their systems. Such a decision could leave certain digital threats to continue lurking on their systems.
Lastly, organizations might choose to invest in a PCI DSS compliance solution but not leverage it to strengthen their security in a meaningful way. PCI DSS requires that organizations have log management, FIM and VM capabilities in place, but all of this could prove to be costly if organizations are implementing a different solution from a different vendor for each security function. Even then, the capabilities might not advance organizations’ security beyond a “checkbox” function. Their FIM solution might alert to changes but offer no context, for instance, while their VM solution might conduct regular scans and identify weaknesses but not offer organizations guidance or hold them accountable to fix those holes.
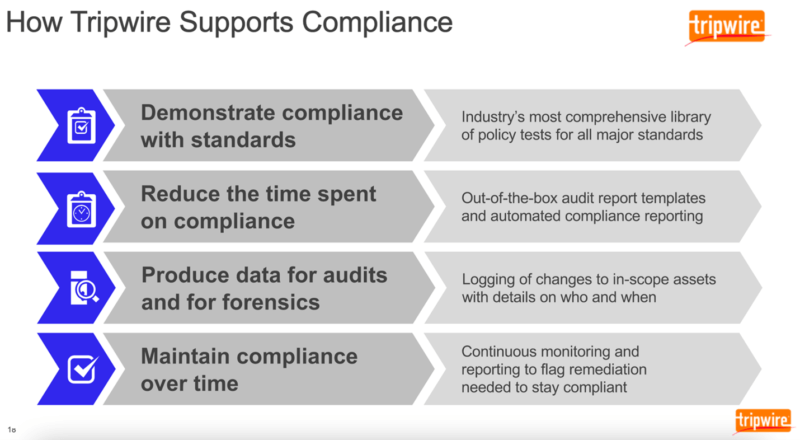
How Tripwire Can Help
Tripwire can help organizations get ready for PCI DSS v4.0.
It’s equipped to help organizations demonstrate compliance not only with PCI DSS but other major standards like CIS, ISO 27001 and many others. It does this by providing out-of-the-box audit report templates and automated compliance reporting. This enables Tripwire to connect to all assets in scope, test those assets and determine if they pass or fail a test for compliance, thereby saving organizations the time they would have otherwise spent on manually auditing everything. It’ll then produce reports that not only show compliance but also log changes to in-scope assets.
With that visibility, organizations can stay on top of their in-scope assets, address instances of configuration drift quickly and thereby maintain compliance over time.
For more information on how Tripwire can help your organization achieve and maintain compliance with PCI DSS, click here.
Insider Insights for the PCI DSS 4.0 Transition
Gain valuable insights from cybersecurity experts on transitioning to PCI DSS 4.0. Tripwire's comprehensive guide provides strategic advice, making the compliance process more streamlined and efficient. Understand the challenges and solutions for meeting PCI DSS requirements with expert guidance.

