
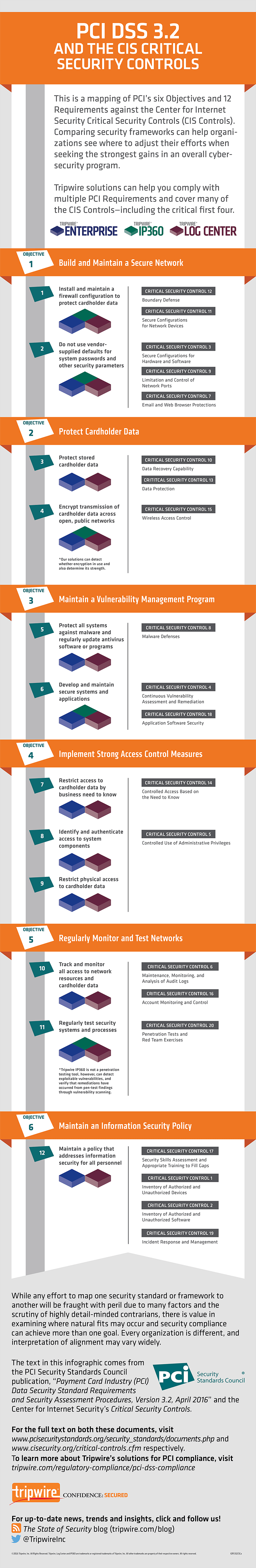
Compliance with version 3.2 of the Payment Card Industry Data Security Standard (PCI DSS) is a must for organizations that handle, process, transmit and store payment card data. But compliance isn’t always easy to establish or maintain. Indeed, there are certain challenges along the way that can make organizations’ compliance with PCI DSS 3.2 superficial and short-lived. To beat those challenges, organizations need to go beyond the checkbox and pursue PCI compliance as a continuous process. One of the ways they can do this is by mapping the six objectives and 12 requirements in version 3.2 of the Standard to the Center for Internet Security’s Critical Security Controls (“the CIS Controls”). In so doing, organizations can learn where they need to adjust their efforts to maximize the efficacy of their digital security programs. Below is a breakdown of how certain CIS Controls, in particular, can help with achieving and maintaining PCI compliance.
PCI Objective #1: Build and Maintain a Secure Network
Under the first objective of PCI DSS 3.2, organizations must build and maintain a secure network by fulfilling two requirements:
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other security parameters.
Five of CIS Controls can help organizations fulfill this objective and its two attending requirements. Companies can start with Control 5 to secure the configurations of their hardware and software. If they implemented Control 5 successfully, organizations will be equipped to fulfill Control 11 and achieve secure configurations for network devices. They can then use Control 7 to ensure email and web protections, including the use of only fully supported browsers and email clients. On top of those measures, organizations can perform regular automated port scans and manage all devices remotely logging into the internal network using Control 9 and Control 12, respectively.
PCI Objective #2: Protect Cardholder Data
The second objective of PCI DSS 3.2 requires organizations to protect cardholder data by meeting the following criteria:
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
Organizations can meet this objective with three of CIS Controls. Chief among them is Control 13, which helps organizations protect data by maintaining an inventory of sensitive data and removing sensitive data not regularly accessed. Companies also need to make sure they have regular automated data backups with Control 10. Finally, organizations can protect their data by limiting their usage of wirelesss technologies, as specified under Control 15.
PCI Objective #3: Maintain a Vulnerability Management Program
There are three requirements to the third objective of PCI DSS 3.2, Maintaining a Vulnerability Management Program. These are as follows:
- Protect all systems against malware and regularly update antivirus software or programs.
- Develop and maintain secure systems and applications.
To satisfy this objective, organizations can avail themselves of three controls. Control 3 gets to the heart of the matter with by emphasizing continuous vulnerability management. Companies can then use Control 18 to establish a process involving the acceptance and treatment of software vulnerabilities. Finally, organizations can set up additional malware defenses under Control 8.
PCI Objective #4: Implement Strong Access Control Measures
The fourth objective of PCI DSS 3.2 requires organizations to implement strong access control measures. There are three requirements to this objective:
- Restrict access to cardholder data by business need to know.
- Identify and authenticate access to system components.
- Restrict physical access to cardholder data.
There are two CIS Controls that can help organizations to match this objective. The first is Control 4, a security measure which can help organizations protect administrative access with unique passwords and multi-factor authentication. The second safeguard, Control 14, can help organizations control access on a need-to-know basis.
PCI Objective #5: Regularly Monitor and Test Networks
Organizations must regularly monitor and test networks under the fifth objective of PCI DSS 3.2. This target consists of two requirements:
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
Three CIS Controls are useful to organizations in fulfilling this objective. Control 6 is especially valuable in that organizations can use it to activate, manage and store logging on critical systems. Along that same vein, Control 16 helps companies monitor account login behavior. There’s also Control 20, which specifies that organizations control and monitor accounts associated with penetration testing.
PCI Objective #6: Maintain an Information Security Policy
The sixth and final objective of PCI DSS 3.2 necessitates that organizations maintain an information security policy. There’s just one requirement for this task:
- Maintain a policy that addresses information security for all personnel.
Four CIS Controls can help organizations achieve this objective. First and foremost, organizations can use Control 1 and Control 2 to establish inventories of their hardware and software assets. They can then look to Control 17 to implement a security awareness training program and Control 19 for developing an incident response program.
For more information on how to map the CIS Controls to PCI DSS 3.2, download this resource. Additional information on how to achieve automated, continuous PCI 3.2 compliance for secure cardholder data can be found here.
Insider Insights for the PCI DSS 4.0 Transition
Gain valuable insights from cybersecurity experts on transitioning to PCI DSS 4.0. Tripwire's comprehensive guide provides strategic advice, making the compliance process more streamlined and efficient. Understand the challenges and solutions for meeting PCI DSS requirements with expert guidance.

