
Cybersecurity threats to manufacturing and process plants come from a wide range of attack vectors, including supply chain, logistics, enterprise computing, remote connections, operator stations, programmable logic controllers, distributed control systems (DCSs), smart sensors, and new smart devices. Internet of Things (IoT) technologies offer greater connectivity and endless applications, but they make the cybersecurity landscape more complex.
Several affected industries have greatly improved their defence posture, primarily thanks to governmental regulatory compliance requirements. Most organizations with industrial control systems (ICS) fall into one of two categories: regulated and non-regulated. It is, therefore, essential to figure out which framework applies to your industry. The ISA/IEC 62443 series of standards belongs to the non-regulated compliance requirements.
The ISA99 Committee
The International Society of Automation (ISA) 99 standards development committee brings together industrial cyber security experts from across the globe to develop ISA standards for the security of industrial automation and control systems that apply to all industry sectors and critical infrastructure. The ISA99 committee addresses industrial automation and control systems whose compromise could result in any or all of the following situations:
- endangerment of public or employee safety
- loss of public confidence
- violation of regulatory requirements
- loss of proprietary or confidential information
- economic loss
- impact on national security.
Manufacturing and control systems include, but are not limited to:
- hardware and software systems such as DCS, PLC, SCADA, networked electronic sensing, and monitoring and diagnostic systems
- associated internal, human, network, or machine interfaces used to provide control, safety, and manufacturing operations functionality to continuous, batch, discrete, and other processes.
The committee's purpose is to develop standards, recommended practices, technical reports, and related information that define procedures for implementing digitally secure manufacturing and control systems and security practices and assessing cybersecurity performance.
Although the guidance applies to those responsible for designing, implementing, or managing manufacturing and control systems, users, systems integrators, security practitioners, and control systems manufacturers and vendors can also make use of it. The focus of these standards and best practices is to improve the confidentiality, integrity, and availability of components or systems used for manufacturing or control and provide criteria for procuring and implementing secure control systems.
The ISA/IEC 62443 series
The ISA/IEC 62443 series of standards, developed by the ISA99 committee and adopted by the International Electrotechnical Commission (IEC), provides a flexible framework to address and mitigate current and future security vulnerabilities in industrial automation and control systems (IACSs). The following diagram, courtesy of ISA, depicts the status of the various work products in the ISA/IEC 62443 series of IACS standards and technical reports.

ISO-27001, NIST Cybersecurity Framework, and ISA/IEC 62443 are some of the widely adopted international standards that provide a comprehensive guideline and absolute effectiveness in securing IT and OT systems.
IEC 62443 Key Publications
According to IEC 62443-1-1, an Industrial Automation and Control System (IACS) is a "collection of processes, personnel, hardware, and software that can affect or influence the safe, secure, and reliable operation of an industrial process." The key standards in the IEC 62443 series are the following:
- IEC 62443-2-4 – defines policies and practices for system integration
- IEC 62443-4-1 - secure development lifecycle requirements
- IEC 62443-4-2 - IACS components security specifications
- IEC 62443-3-3 - security requirements and security levels
- IEC 62443-3-2 – cybersecurity risk assessment
The standard sees cybersecurity as an ongoing process and not as a goal that must be reached and caters to the development of IACS components that are secure by design. Defence-in-depth policies and practices must govern the integration of these components into an industrial environment.
ISA/IEC 62443-4-2, Security for Industrial Automation and Control Systems: Technical Security Requirements for IACS Components, provides the cybersecurity technical requirements for components that make up an IACS, specifically the embedded devices, network components, host components, and software applications. The standard sets forth security capabilities that enable a component to mitigate threats for a given security level without the assistance of compensating countermeasures. The standard specification of security capabilities for system components offers product vendors and all other control system stakeholders a consistent language. This simplifies the purchase and integration processes for the control system's computers, software, network equipment, and control devices.
ISA/IEC 62443-4-1, Product Security Development Life-Cycle Requirements, specifies process requirements for the secure development of products used in an IACS and defines a secure development lifecycle for developing and maintaining secure products. The lifecycle includes security requirements definition, secure design, secure implementation (including coding guidelines), verification and validation, defect management, patch management and product end-of-life.
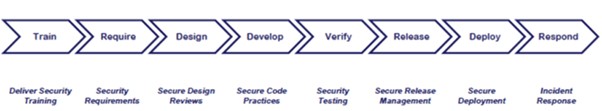
These requirements can be applied to new or existing processes for developing, maintaining, and retiring hardware, software, or firmware. The requirements apply to the developer and maintainer of a product but not to the integrator or user of the product. It is crucial to design security into products from the outset of the development life cycle since it can help eliminate product vulnerabilities before they reach the field.
We are all aware of how challenging and costly it can be to patch software in the field regularly. The standard allows us to build secure-by-design products and stop the cycle of regular security patches. ISA/IEC 62443-3-3, System Security Requirements and Security Levels, defines the security assurance levels of the IACS components. Security levels define the cybersecurity functions embedded in our products to increase their robustness and resistance to cyber threats.
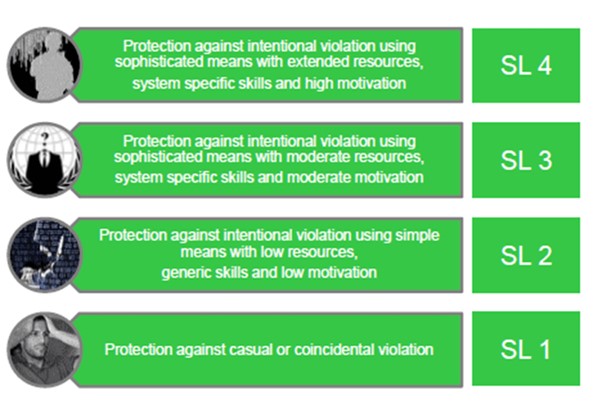
Security Levels 1 and 2 correspond to threats from insiders, such as careless or disgruntled employees or contractors or intruders with low skills and motivation. On the other hand, Security Levels 3 and 4 are related to threats from "professional" cybercriminals, industrial espionage, or state-sponsored malicious actors that demonstrate high skills and moderate to high motivation. In addition, IEC 62443-3-3 defines the security Foundational Requirements, which include processes for user authentication, enforcement of roles and responsibilities, change management, use of encryption, network segmentation, audit logs, and system backup and recovery.
ISA/IEC 62443-3-2: Security Risk Assessment for System Design, published in 2020, defines a comprehensive set of engineering measures to guide organizations through the essential process of assessing the risk of a particular IACS and identifying and applying security countermeasures to reduce that risk to tolerable levels. The standard is based on the premise that each organization that owns and operates an IACS has its own risk tolerance. Each IACS represents a unique risk depending on the threats it is exposed to, the likelihood of those threats occurring, the inherent vulnerabilities in the system, and the consequences if the system were compromised. ISA/IEC 62443-3-2 defines the core requirements for an IACS risk assessment without being excessively prescriptive. The resulting standard promotes industry-wide uniformity while allowing IACS owners and operators to employ any approach that is compliant with the standard.
How does ISA/IEC 62443 differ from ISO 27001?
Although similar in that they are both cybersecurity-centered industry standards/regulations that help organizations meet compliance requirements, pass audits, and achieve certification, IEC 62443 and ISO 27001 have several key differences.
ISO 27001 is a standard and framework for cybersecurity management. It helps businesses handle information security risks. ISA/IEC 62443, however, is focused more on business continuity in industrial environments.
How Does ISA/IEC 62443 Help Organizations Comply with Regulations Like NIS2?
The ISA/IEC 62443 standard helps critical infrastructure businesses comply with regulatory requirements like NIS2 because it aligns with NIS2's focus on risk management and the protection of essential services and addresses specific cybersecurity needs in operational technology environments.
How Tripwire Helps
Currently, IEC 62443 covers aspects of domains such as chemical processing, petroleum refining, food and beverage, energy, pharmaceuticals, water, and manufacturing, but it can also be used in automotive and medical devices. Applying the controls suggested by the ISA/IEC 62443 framework can be overwhelming.
Tripwire's Cybersecurity for ICS can help you meet the foundational requirements defined in the standard. Our cyber resiliency suite integrates with the plant network equipment and factory automation systems you already own to help you find, fix, and monitor security to prevent and detect cyber incidents. "Navigating Industrial Cybersecurity: A Field Guide" covers how to get a robust cybersecurity program in place, with clear instructions on implementing industrial frameworks and foundational security controls, aligning IT/OT, gaining executive buy-in, and selecting the right tools for the job. You can download it here.
Request a Live Demo
Experience the power of Tripwire's cybersecurity solutions firsthand! Take a guided tour or participate in live demos to see how our products can enhance your organization's security. Start exploring now

