
An updated variant of Jaff ransomware boasts a more professional design and now encrypts victims' data with the WLU extension. On 23 May, Internet Storm Center (ISC) handler Brad Duncan collected 20 malspam emails that all used a fake invoice theme and a spoofed email address. The emails also came with a PDF attachment containing an embedded Word document. This document leveraged malicious macros to infect a Windows computer.
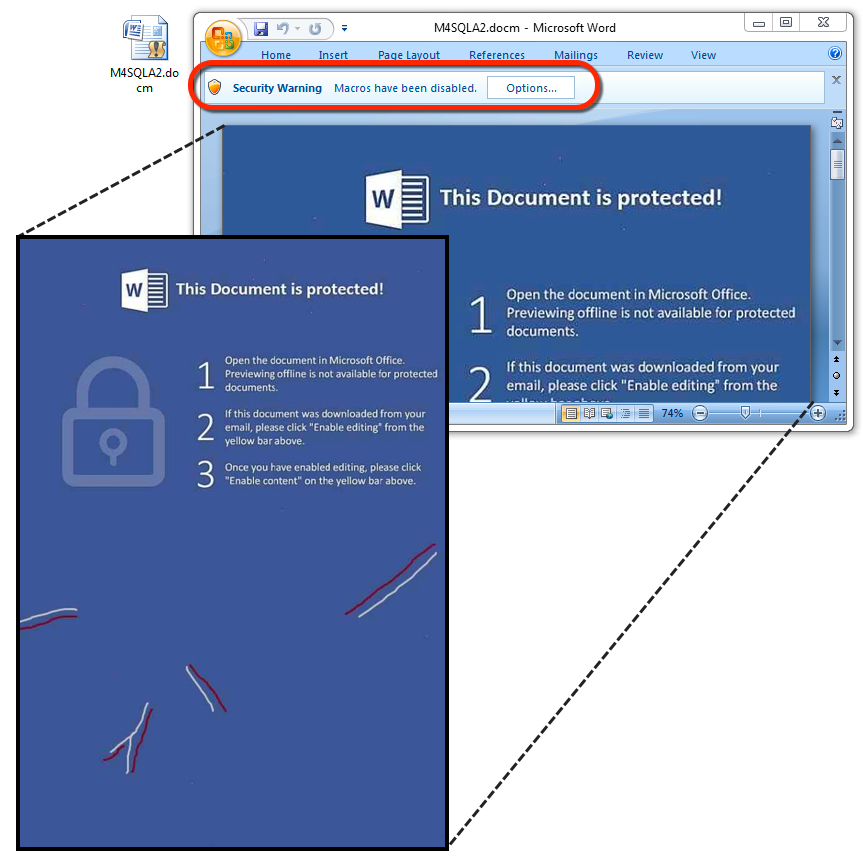
The embedded Word document with malicious macros. (Source: ISC) Enabling the document's macros initiated an infection at the hands of Jaff, a form of ransomware which researchers first discovered in early May. Duncan explains how this new campaign loaded the threat:
"The Word macros generate an initial URL to download an encoded Jaff binary, then we see one other URL for post-infection callback from an infected host. The initial HTTP request for Jaff returns an encoded binary that's been XORed with the ASCII string I6cqcYo7wQ. Post-infection traffic merely returns the string 'Created' from the server after an infected host checks in."
The campaign stored the encoded Jaff binary with an ever-changing filename like "lodockap8" to the user's AppData\Local\Temp directory. It then decoded the binary and saved its new form, an executable that also sported an ever-evolving name like "levinsky8.exe," to that same directory. That executable in turn activated the ransomware payload, which appeared like this on the infected host:
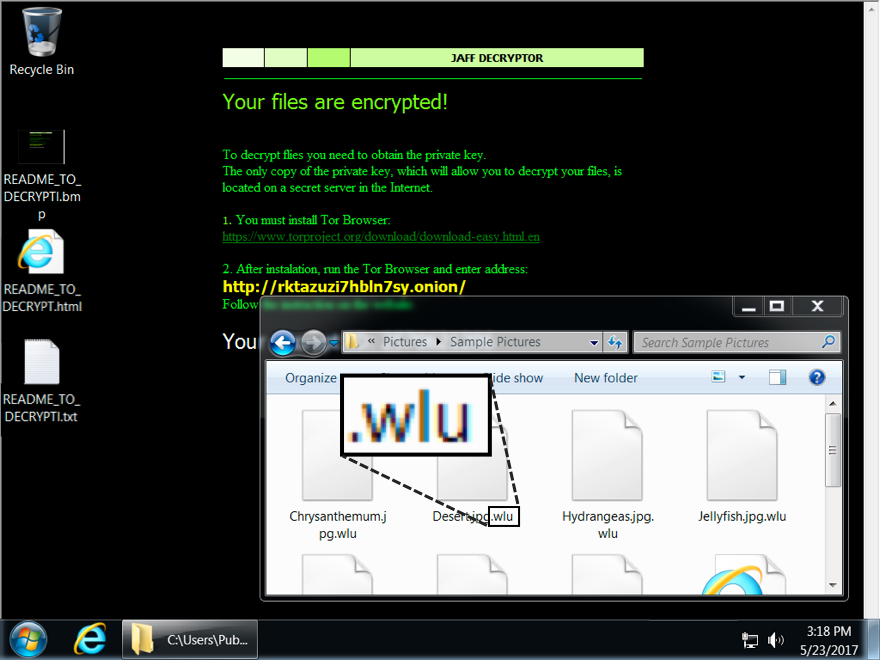
Desktop of a Windows host infected with a Jaff ransomware sample from 2017-05-23. (Source: ISC) Compare the above sample with how it looked earlier in May:
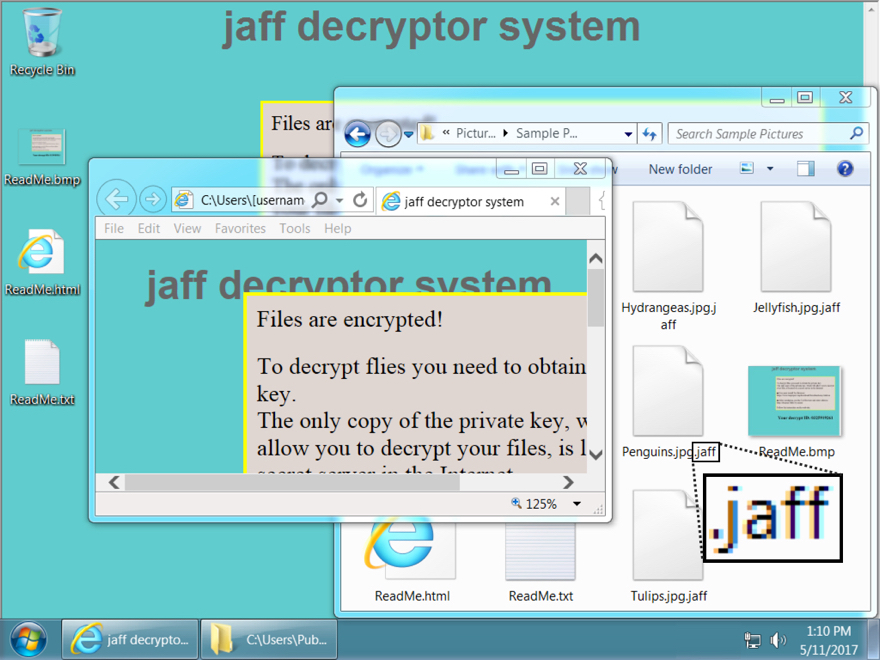
Desktop of a Windows host infected with a Jaff ransomware sample before 2017-05-23. (Source: ISC) Not only that, but whereas Jaff previously encrypted victims' files using the JAFF extension and demanded 2.036 Bitcoins (or roughly $3,726 in ransom), it's now shifted to the WLU extension and asked Duncan's machine for only 0.35630347 Bitcoins (around $833.50). To defend against Jaff, organizations should consider using software restriction policies that deny binary execution in certain Windows directories. They might want to also consider investing in other ransomware prevention strategies like disabling Office macros by default. A guide for this preventive step is available here. In the event Jaff has already infected your computer, here's what you can do to try to recover your files.

