
A new attack framework known as "Triton" is targeting industrial control systems (ICS) in an attempt to cause operational disruption and/or physical consequences. FireEye recently detected an incident at a critical infrastructure organization in which an attacker gained access to a Distributed Control System (DCS) that allows human operators to remotely manage industrial processes. From there, the bad actor could have caused the plant to shut down. Instead they moved to also compromise the Triconex Safety Instrumented System (SIS) controllers in a move that FireEye believes was designed to cause the maximum amount of damage at the company. It's at this stage that the malicious individual revealed Triton. The enterprise digital security company's Blake Johnson, Dan Caban, Marina Krotofil, Dan Scali, Nathan Brubaker, and Christopher Glyer elaborate on this critical moment:
Once on the SIS network, the attacker used their pre-built TRITON attack framework to interact with the SIS controllers using the TriStation protocol. The attacker could have caused a process shutdown by issuing a halt command or intentionally uploading flawed code to the SIS controller to cause it to fail. Instead, the attacker made several attempts over a period of time to develop and deliver functioning control logic for the SIS controllers in this target environment. While these attempts appear to have failed due one of the attack scripts’ conditional checks, the attacker persisted with their efforts. This suggests the attacker was intent on causing a specific outcome beyond a process shutdown.
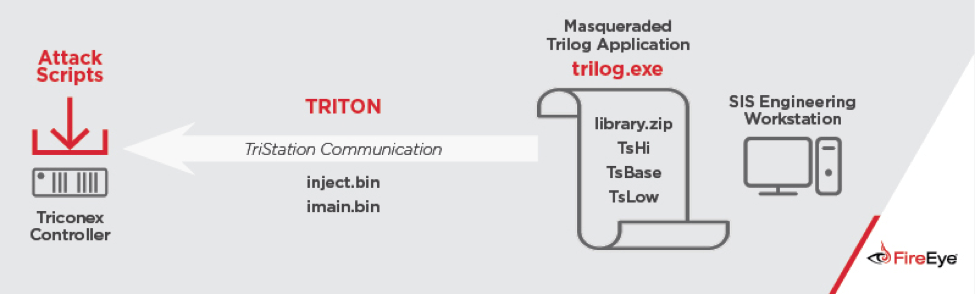
TRITON Architecture and Attack Scenario. (Source: FireEye) While attempting to cause additional damage, the wrongdoer inadvertently shut down operations. At this time, FireEye has not attributed Triton or the attack to a specific threat actor. They have found that the malware is consistent in its aim with other ICS-related threats including Stuxnet and Industroyer. Coupled with the fact that whoever was responsible for the attack had no apparent monetary motivations, was willing to disrupt critical infrastructure, and had created a significant piece of malware, FireEye reasons that a nation-state actor is the most likely handler of Triton. To protect against attacks at the hands of Triton and similar malware, critical infrastructure organizations should segregate their networks, implement access control on critical workplace endpoints, and create change management procedures. They should also invest in a tool that, among other things, monitors the industrial network for potential problems. To learn about one such ICS solution that does just that, click here.

