
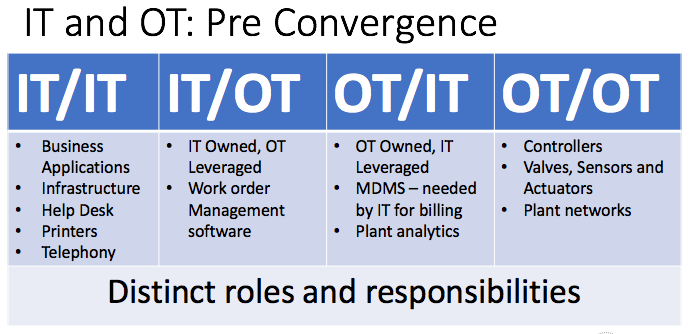
March 15, 2018, was a momentous day for U.S. homeland security officials. On that date, the Department of Homeland Security (DHS) and the Federal Bureau of Investigations (FBI) for the first time ever attributed digital attacks on American energy infrastructure to actors associated with the Russian government. Their joint technical alert (TA) explained that individuals associated with the Kremlin first went after “staging targets,” companies with network access to the attackers’ “intended targets.” The actors then pivoted off those preliminary victims in what were likely supply chain attacks to compromise the networks of U.S. energy organizations. The TA along with additional DHS reports of Russian attacks against energy organizations underscore the digital security challenges that confront organizations running industrial control systems (ICS). Of these, perhaps the greatest obstacle is how attackers are exploiting the connections between information technology (IT) and operations technology (OT) to infiltrate industrial organizations. It wasn’t always this way. Convergence is a relatively new phenomenon, here’s one perspective on the progression. Prior to this union, IT and OT did different things in four distinct silos. There were distinct groupings of responsibilities (in the form of “Owner/User”); first IT/IT, which did traditional IT stuff, and OT/OT, which did traditional OT stuff like managing controllers and segmenting the plant network. The other silos involved some but limited collaboration between the two. IT/OT, for instance, sometimes featured OT leveraging IT-owned and operated equipment like technology systems to submit work orders, whereas OT/IT in some cases could include IT leveraging OT-owned meter data management system (MDMS) for billing purposes.
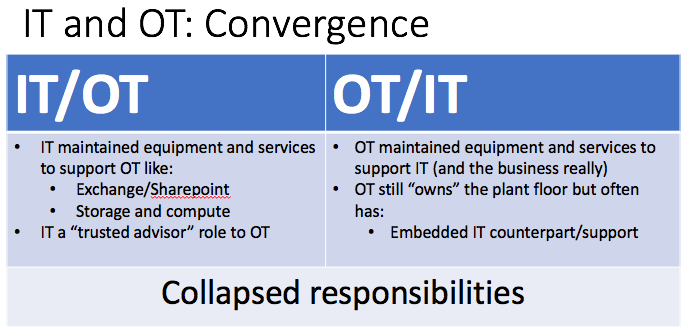
All that changed with the convergence of logical and physical resources. This merger reduced the four silos to two, resulting in shared responsibilities and devices. IT and OT no longer operate in vacuums, though they are still different entities. IT/OT today involves IT maintaining equipment and services in order to support but not advise OT. At the same time, there’s OT/IT, a silo where OT maintains equipment and services to support its embedded IT counterpart.
Given the IT-OT convergence and their shared responsibilities around managing ICS equipment, it’s no wonder that 44 percent of respondents to the SANS 2017 State of ICS Survey Report cited the addition of network devices as the top threat to industrial control security. It’s also not surprising that digital attacks have changed to accommodate these new assets. Prior to 2017, most of the attacks that struck industrial control systems like Stuxnet were designed by nation-state actors with specific targets in mind. Post-2017, there have still been sophisticated threats like Crash Override and TRISIS designed for certain ICS systems, but the bulk of threats now confronting these assets are generic IT malware like WannaCry, NotPetya and BadRabbit. With this shift in the ICS security threat landscape, campaigns targeting industrial environments are more numerous than they’ve ever been. Hence the attacks by Kremlin-affiliated actors against U.S. energy infrastructure, among other targets. Those offensives beg the question: how can organizations best approach the security of their industrial systems? Putting aside unrealistic considerations of switching industrial environments back to “analog and nondigital control systems,” organizations can start by taking an inventory of all their devices. They can do this by conducting a physical inventory or using a tool; in either case, they should update their network drawings after the fact. Next, organizations should use network segmentation, implement network access control (and even MAC address filtering as a stop gap for legacy endpoints that don’t support 802.11x) and institute monitoring and alerts to help detect and remove unauthorized connections to the industrial network. Finally, they should identify vulnerable and exploitable endpoints and enact robust patching mechanisms and log correlation to protect them against digital attackers. For information on how Tripwire’s solutions use these methods and other techniques to defend organization’s ICS systems, click here.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

