
You don’t have to search very far in the news to see stories of websites being hacked and customer details being stolen. Stories about incidents involving industrial control systems (ICSes) and operational technology (OT) environments aren’t so common. But they are prevalent. Just the other week, for example, an airline company sent out an email letting me know that their database had been hacked and that my travel details might have been taken. These types of incidents are happening more often, and they are also becoming more frequent in the industrial control environments of organizations in the water, chemical, oil & gas and power industries. These cyber attacks are even making news headlines. When it affects critical national infrastructure, people take notice. A one-size-fits-all plan won’t make cybersecurity work for the evermore-converging worlds of IT and OT. What works in an IT office might not necessarily work in industrial apps, after all. So, how can organizations in Europe, the Middle East and Africa (EMEA) make ICS security work in the age of IT-OT convergence? In this article, we’ll look at some simple but practical steps in the journey to securing your network. Then we’ll look at some best practices on how to secure the network. Along the way, we’ll examine what goals/standards are applicable to a particular industry sector as well as any regulatory government frameworks with which we must comply.
Where Are These ICS Security Threats Coming from?
Threats can come from many places. They may be adversarial, accidental, environmental, etc. When you really dig into the reasons for downtime due to cyber incidents in industrial control systems, however, the vast majority of these are unintentional. Intentional attacks make up only 20% of the total incidents. From that, only about half are from external attacks.
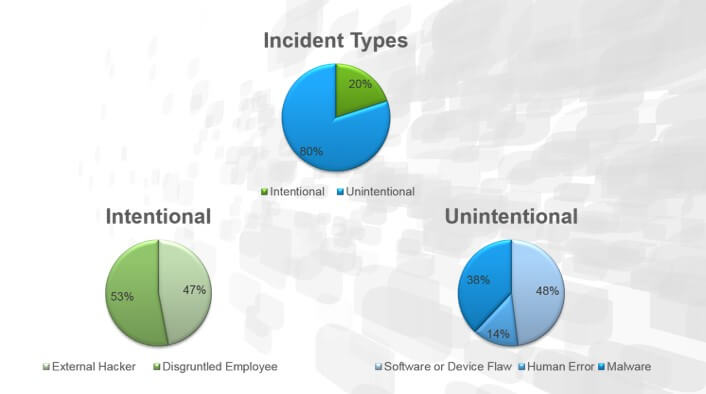
A breakdown of security incidents at industrial organizations. (Source: Belden) The problem is that the convergence of IT and OT is making reliability and security in EMEA organizations’ industrial environments more difficult to achieve. That’s because IT and OT traditionally maintain different foci than one another. For its part, IT environments “normally” have more connections to the outside world. They have more possibilities for devices to connect to their network. (Just take the example of Bring Your Own Device.) Many of the functions of these networks depend on connectivity to the web or cloud. That is not to say that ICS or OT environments do not require connectivity. However, it is less likely that they require this. Normally, their connections to cloud applications are simply designed to relay “data” about monitored industrial assets. The connections operate in service of the environment’s operational technology, in other words. In this understanding, IT-OT convergence is bringing more and more connections to OT environments. With those connections come more and more risks, particularly with regards to cybersecurity. Perhaps the most significant challenge is finding talented personnel to protect the rising number of connected endpoints in these environments. More than half (58%) of the companies surveyed classify IT as a major challenge to hire ICS cybersecurity employees with the right skills. This aspect is even more critical given that companies need to integrate their OT/ICS with their IT systems and Internet of Things (IoT) ecosystems.
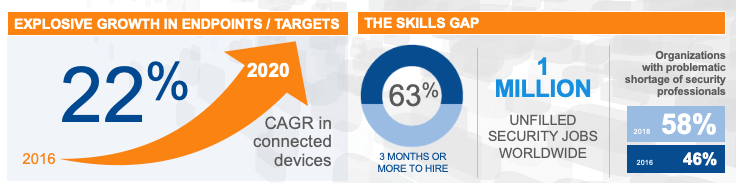
A look at endpoint growth and the growing skills gap. (Source: Belden) Simultaneously, 50% of the companies surveyed said it’s challenging to find suitable partners and service providers to implement ICS solutions. Given that the market for talent is exhausted, this is especially critical. EMEA organizations need external services to compensate for a lack of skilled cybersecurity talent.
How to Ensure Cybersecurity in Your Industrial Environments
All of this can be a daunting task if you have little or no experience with cybersecurity. So, let’s break it down. When we talk about “cybersecurity,” the first thing that might come to mind is a firewall. While they are extremely important in controlling traffic flows, you can’t put a firewall in front of every device on your network. There are some foundational steps you can put in place to control your networks. First, we want to be sure we know what is connected and where it is connected to create a baseline. We can do this by using passive discovery to build an inventory of all hardware and software. Once that’s begun, we can use secure configuration management (SCM) to set an ideal baseline for all tracked assets and then monitor for deviations. Second, we want to limit access to the network. We can do this by putting in VLANs and ACLs (Access control lists) as well as firewalls. Those solutions might be stateful, or they could use Deep Packet Inspection for that extra layer of security. After you’ve taken these initial steps, you then need to be able to react if something changes. This is where having some sort of compliance rules or regulations can help determine your actions as result of these changes. Towards that end, you can look to any number of standards as a means of determining how good your cybersecurity posture is on your network. Here are just a few in particular that you can review:
- ANSI/ISA 99 – This is probably one of the first standards I personally used in networks and gave some good specification on how traffic should flow between networks (zones and conduits). The evolution of this standard is the IEC 62443, with the intention of completing and expanding its capacity for action.
- NIST SP 800-82 (Guide to Industrial Control Systems) – This defines the typical topology of SCADA systems, identifying threats and vulnerabilities and providing recommendations and countermeasures to mitigate these risks.
- ISO 27000 (Information security management systems): This is a general-purpose standard that provides good practices and recommendations for information security management and is normally used for the implementation or management of Information Security Management Systems (ISMS).
Network components need to comply with these standards together as an overall network. It’s not a case of “I’ll get compliant products, simply put them on my network and get the job done.” You need to have a comprehensive strategy consisting of solutions that build on these types of standards from the ground up. Learn how Tripwire can help secure your EMEA organization’s industrial environment.

About the Author: Ciaran Burns is a Solutions account Manager covering the UK & Ireland for Belden’s industrial platform of products. He has been with Belden a little over 8 years and has had both commercial and technical positions within the company. He brings together his mix of, 15 years’ experience, in the industrial automation field to serve his customers with cutting edge Networking solutions ranging from on board rail, energy substations to water and waste water treatment plants. Ciaran graduated in 2005 from the University of Sussex in Brighton, England with a 1st class Masters in Electronic and Communications Engineering. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

