
Authorities in the United States have charged two people in connection with a series of notorious ransomware attacks. According to the Department of Justice, 34-year-old Faramarz Shahi Savandi and 27-year-old Mohammad Mehdi Shah Mansouri were the masterminds behind attacks against more than 200 networks since 2015. Unlike normal ransomware attacks (which are often delivered by a widely spammed-out malicious email attachment), the SamSam attacks saw organizations manually hacked one-by-one via a variety of techniques including brute-forcing their way into exposed RDP connections on a vulnerable server and making use of stolen login credentials. Once in, the hackers would harvest admin passwords and escalate their privileges with a view to gathering further intelligence on the network they had compromised, expanding their foothold and unleashing the SamSam ransomware to compromise and encrypt PCs. Victims were directed to webpages under the control of the hackers that contained their ransomware demands along with a threatening countdown after which - it was said - decryption keys would be deleted and recovery of the victim's data would be impossible. The SamSam extortionists would demand as much as US $8000 worth of Bitcoin to recover the data from one infected computer or a US $55,000 lump sum to decrypt all affected PCs on a network.
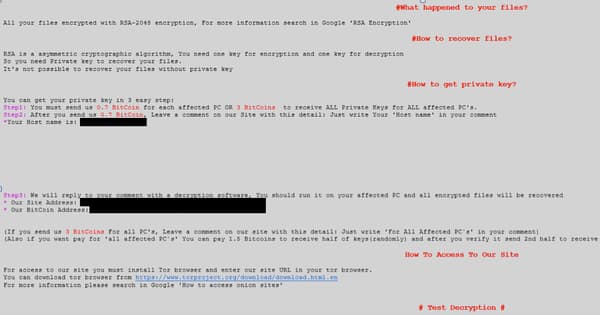
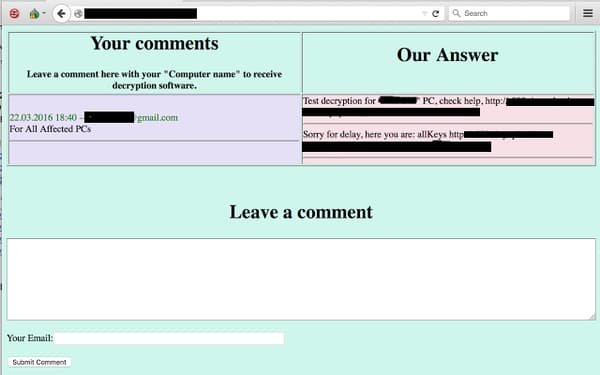
And like any other successful business venture, the brains behind SamSam recognized the importance of properly supporting their "customers." Towards that end, they provided a portal through which victims could leave questions if they were experiencing difficulties making a payment.
In all, the two men are alleged to have successfully extorted more than US $6,000,000 from their victims, who included hospitals, educational institutions, the city government of Atlanta, Colorado’s Department of Transportation and the Port of San Diego. Over 200 victims are said to have suffered damages totaling over US £30 million after being hit by SamSam. Since 2013, Savandi and Mansouri are said to have used two Bitcoin addresses to process over 7,000 transactions, sending approximately 6,000 Bitcoin worth millions of dollars. According to a statement from the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) some of these were Bitcoin received as a result of the SamSam ransomware. Now Savandi and Mansouri have both been charged with conspiracy to commit wire fraud, conspiracy to commit fraud and related activity in connection with computers, intentional damage to a protected computer and transmitting a demand in relation to damaging a protected computer. But as the FBI's wanted poster makes clear, both men are thought to reside in Tehran, the capital of Iran.

As such, if Savandi and Mansouri don't do anything silly like go on vacation to a country which has an extradition agreement with the United States, the chances of the two men having their day in an American court room seems remote. In the absence of a physical person to place before a judge, the US authorities have instead published the Bitcoin addresses used by the pair for allegedly collecting their ransomware payments: 149w62rY42aZBox8fGcmqNsXUzSStKeq8C and 1AjZPMsnmpdK2Rv9KQNfMurTXinscVro9V Cryptocurrency exchanges around the world are being encouraged not to process transactions related to either address. "Treasury is targeting digital currency exchangers who have enabled Iranian cyber actors to profit from extorting digital ransom payments from their victims. As Iran becomes increasingly isolated and desperate for access to U.S. dollars, it is vital that virtual currency exchanges, peer-to-peer exchangers, and other providers of digital currency services harden their networks against these illicit schemes," said Treasury Under Secretary for Terrorism and Financial Intelligence Sigal Mandelker. "We are publishing digital currency addresses to identify illicit actors operating in the digital currency space. Treasury will aggressively pursue Iran and other rogue regimes attempting to exploit digital currencies and weaknesses in cyber and AML/CFT safeguards to further their nefarious objectives."
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

