
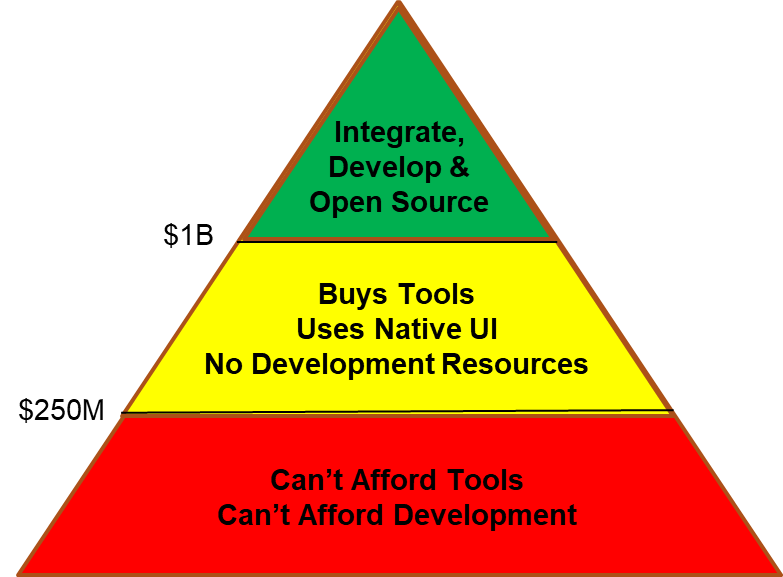
It may be possible to democratize security by making it more accessible to average companies through community resources. We have an idea or two but we would appreciate your thoughts. At the 2019 RSA conference, Matt Chiodi, Chief Security Officer of Palo Alto Networks stated: “… small organizations are using on average between 15 and 20 tools, medium-sized businesses are using 50 to 60 and large organizations or enterprises are using over 130 tools, on average.” It is a statement of the obvious when a SANS survey concludes that “too many tools that are not integrated" is one of the top three problems faced by security organizations. I’d like to refine these observations a bit. The pyramid below describes three levels of resource capability. The companies at the top are large and have extremely well-funded/mature security programs. They are able to afford the tools they believe are necessary, and they have internal development to either integrate tools or create tools as needed. The yellow band is the middle-class. They can afford a fair number of tools, but they can’t afford extensive integration or internal development needed for automation and customization. At the bottom is a large group of “have-nots.” They can only afford a limited number of tools, few staff, integration capabilities only when they are supplied by vendors and no customization.
We believe that this structure is problematic. As long as a significant percentage of the business community is unable to deploy adequate security, a nursery will exist for the training of an increasing volume of advanced bad actors. We also feel that small cities, non-profits and small businesses deserve to conduct their businesses safe from bad actors. We believe that an opportunity may exist to push the bar for affordable security down the food chain. Let’s be clear. This is not a purely altruistic venture. We believe strongly that community good is not inconsistent with profit. It is possible to strike a balance. So, we put this idea in front of you for your thoughts, opinions and improvements. Imagine an “open source” platform/community. In it, we construct a modular architecture. The individual modules could be open-sourced community elements, or they could be commercial products. The objective would be to have a system wherein the component parts are interoperable. A new company could pick up the pieces and have a credible security solution with a mix of open and commercial components put together with little to no coding. A more advanced company could select the areas in which they wish to focus their limited resources to do customization. In some cases, this would be no more than a UI. In others, it might be an automated process that augments standard components. The community would be there to provide components, recommendations, advice and assistance. Some of this would be for free; some for pay. The vendor community would benefit from greater interoperability and from functionality generated by customers. They would get product feedback and have an interested body of consumers to engage. Large players have the potential to contribute to the good of mankind, observe possible recruits, improve their public image and exploit open sourced work products. They could benefit from policy content, scripts and other content developed by other experts in the field. Small players benefit from free resources and advice from the community. More organizations could afford better security. Obviously, security is a large and diverse space. We could easily attempt to boil the ocean. Instead, we would propose to begin the work in our scope of expertise. We would bring together a collection of vendors with expertise in risk detection together with threat feed suppliers and analytics vendors. Customers would be invited and encouraged to participate. Policy content and analytics modules that they create for their internal use could be made available to other companies under open source/royalty free rules. Companies with fewer resources can contribute engineering time that they have toward shared work. Consultants wishing to make a name for themselves in the community could use the forum to create a portfolio of useful modules. Graduate students could also use the forum to provide novel work as part of their doctoral dissertation or master thesis. In the risk management system that we’ve envisioned, we could imagine collecting risk data from every possible source (i.e. vulnerabilities, configurations, behavioral analysis) and then combining it with data feeds like exploit activity and DNS analysis to enlarge and enrich the dataset. This blended and enriched data could then be used to drive a variety of ML and AI defense and reporting mechanisms. So, we look to those of you in the trenches to give us the benefit of your hard fought experience.
- If we could create a modular risk management system as a first step in a security community, would your company find it useful? Would it save you time and money?
- Would your company be likely to share work you’ve done? Would you want to use work from others?
- Does our pyramid model reflect your reality?
- If you think the concept is interesting but a little rough around the edges, how would you improve it?
- If you know of others who are working towards similar objectives, could you introduce us?
Please send us an email with your thoughts, opinions and even the occasional fever swamp ramble. Direct your contributions to [email protected]. And thank you in advance for your help.

