
It’s safe to say that cybersecurity is a common issue for all industries. But what is the cybersecurity state of affairs for Industrial Control Systems (ICS), and why should we care? ICS monitor and control industrial and physical infrastructure processes that are crucial for industries like manufacturing, transportation, energy, oil and gas, and chemical. If these ISC devices were to be compromised, regular service could be disrupted, proprietary data could be lost, and significant harm could occur. The bottom line is this: we all (consumers, businesses, governments, and organizations) should be concerned about the industrial control systems security posture.
What is the Security Posture for Industrial Control Systems-based Organizations?
It is hard to get an accurate read on the security posture for critical ICS infrastructure today for a variety of reasons. It is not a requirement to publicly disclose a breach if and when one occurs. Indeed, ICS-based organizations are not required to follow the US Data Breach Disclosure Act 2015, which requires organizations to notify consumers when their personal information is compromised. There are also minimal enforceable compliance regulations to drive better security. Exceptions do exist, however, such as in the North American Energy sector with NERC. The following are emerging standards for ICS environments that offer some security guidance:
- ANSI/ISA- 62443-3-2 is a security standard specific to ICS environments. It focuses on the network segmentation and isolation of these environments.
- NIST SP800-82r2, Guide to Industrial Control Systems (ICS) Security is directed at ICS/SCADA systems and was published in February 2015.
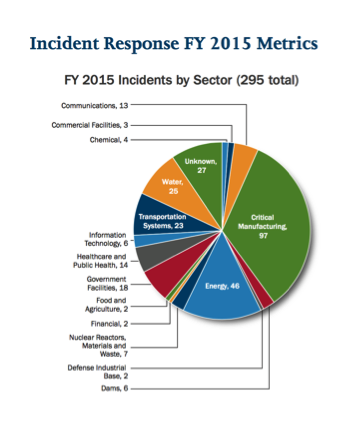
Source: ICS-CERT Several pieces of research indicate how bad the state of ICS security is. We begin with the Department of Homeland Security’s Industrial Control System Cyber Emergency Response Team (ICS-CERT), which offers periodic updates on incidents reported. ICS-CERT’s Final Incident Response Statistics from 2015 showed that 295 incidents involving critical infrastructure were reported in the U.S., compared to 245 ICS-CERT-investigated incidents in 2014. Most affected manufacturing and energy. Not surprisingly, spear-phishing tactics were cited as the single most common attack method. A vendor's research arrived at the same findings. Spear phishing is a people issue that suggests everyone needs to know about cyber security. While this research is helpful to gain insight into the security posture for ICS, the malware-driven power outages in Ukraine were a huge wake up call to ICS environments. Around Christmas Eve 2015, attackers overwrote firmware on critical devices at 16 substations, leaving them unresponsive to any remote commands from operators. As a result of those attacks, 80,000 customers went without electricity for six hours, and workers had to control the breakers manually.
OT? IT? To XT
Day-to-day functions in ICS-based environments are managed by Operations Technology (OT) in many organizations, but cyber security is currently assigned to Information Technology (IT.) To meet tomorrow's threats, we need these two different types of technologies to work together. The blending of IT and OT is critical since more ICS devices are using network connectivity in order to improve automation and become more efficient To address the threats associated with connectivity, some organizations are working to “air gap” or isolate vulnerable ICS systems, but even then, most ICS devices are never fully disconnected or segmented from the network. For example, there might be a link for testing or a Wi-Fi link to the Internet. Another consideration is that many ICS devices are running legacy operating systems that have not been upgraded and are therefore more likely to have vulnerabilities. In general, OT typically does not upgrade because it would disrupt service and jeopardize uptime, whereas a good part of an IT professional’s job is to upgrade systems to improve functionality, performance and minimize vulnerabilities. This fundamental difference will need to be reconciled. Lots of people are talking about securing our critical infrastructure. Take Robert Westervelt, and information security research manager for IDC:
"A combination of factors is dramatically reshaping OT security. More Internet connected industrial automation devices and the convergence of OT and IT infrastructures, in addition to a shortage of security skills, means that accurate evaluation and mitigation of security risks is increasingly challenging.”
Analysts are predicting that by 2020, IT security will be responsible for 25% of physical incidents in ICS environments. Some may ask why. It’s simple: many ICS devices are connecting to the Internet and the IT network, but most organizations do not have “security” professionals who can protect ICS devices. This makes IT security front and center to this issue.
What to Do about your Industrial Control Systems?
Okay enough of the doom and gloom discussion. So what can you do? Basic security hygiene would include monitoring critical ICS-based assets by:
- Deploying anti-malware and breach detection where possible.
- Preventing unauthorized applications from running by deploying application whitelisting.
- Preventing unauthorized changes by deploying secure configuration.
- Minimizing known vulnerabilities by deploying vulnerability management where possible.
- Avoiding physical attacks by enabling USB lockdown on all ICS devices.
- Segmenting your network with firewalls/IPS between business and ICS networks.
There are also industry resources available. For example, the United States Department of Homeland Security (DHS), the National Cybersecurity and Communications Integration Center (NCCIC) and the National Security Agency (NSA) have jointly published a paper titled Seven Steps to Effectively Defend Industrial Control Systems, a resource which is aimed at providing practical steps organizations can take to protect their critical infrastructure. The ICS-CERT organization has a range of support from training, onsite assessments, periodic published guidance, and assessment tools. In particular, its Cyber Security Evaluation Tool (CSET) is a stand-alone software tool that guides asset owners and operators through a step-by-step process to analyze their ICS andIT network security practices using many recognized government and industry standards and recommendations. CSET provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture. Tripwire also offers support for securing ICS environments. Most recently Tripwire announced Tripwire Configuration Compliance Manager (Tripwire CCM) for Industrial Automation, which provides customers a simple path to add effective security monitoring and assessments. Tripwire CCM operates without touching ICS or SCADA equipment, risking operational availability, or requiring a complicated deployment. I am hoping analyst predictions can be challenged, but it will require prompt action and resources. War always implies human safety is at risk, and this is a cyber war we cannot lose. If you are interested in learning more about Industrial Cyber Security you can download our new e-book, “Industrial Cyber Security For Dummies” here.

Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

