
The cyber threat landscape today continues to pose a myriad of unique challenges. This is especially the case for industrial organizations due to factors such as aging equipment, poor design or implementation, skills gaps and a lack of visibility. These shortcomings are exacerbated by the mean time to breach detection, which continues to hover above 150 days on average. The SANS Institute via the Center for Internet Security recommends the Critical Security Controls as a means for organizations to strengthen their digital security. These measures make it clear that once an organization has completed a hardware and software inventory, one of the most important security controls they can implement is secure configurations. One of the four actions to implement, automate and measure effectiveness is as follows: Improved information security configuration and hygiene to reduce the number and magnitude of security vulnerabilities and improve the operations of networked computer systems, with a focus on protecting against poor security practices by system administrators and end-users that could give an attacker an advantage.
A Needle in the Haystack Conundrum
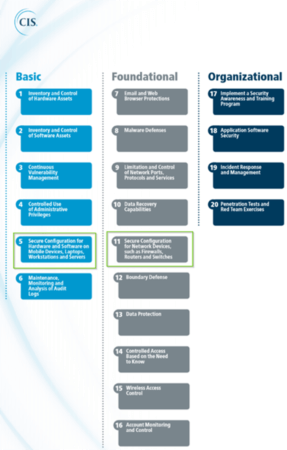
Unfortunately, implementing the CIS Critical Security Controls is no small undertaking. At first glance, Basic Control 5 “Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers” and Foundational Control 11 “Secure Configuration for Network Devices, such as Firewalls, Routers and Switches” appear to be trivial. In reality, implementing these two measures constitutes a significant task. I liken security configuration management to finding a needle in a haystack; an organization only has to make a single mistake to allow an adversary to wreak havoc. I’m reminded of the Capital One attack in 2019 that was accomplished through leveraging what was described as a “configuration vulnerability.” An organization of any size, not just a major financial institution like Capital One, can have thousands if not hundreds of thousands of security configuration settings that are worthy of scrutiny. As such, finding a misconfiguration can be like trying to find several needles in many haystacks.
The OEM Approach
To further complicate the security configuration management challenge, especially in the ICS/SCADA world, OEM vendor solutions like complex control systems can add unique operating systems, software and hardware to the mix that have equally unique and often less-than-ideally-documented security configurations. A vendor specializing in their field will have unique advantages to selecting an appropriate cybersecurity framework for their platform, taking steps to integrate it, understanding the unique requirements (regulatory or otherwise) of their customer base and properly implementing a security configuration management solution. Regarding the latter point, such a tool should come equipped with the ability to reduce the average mean time detection of a breach to a number that’s more reasonable than 150 days.
SANS Webinar
Join us on Friday, July 10th at the SANS Oil & Gas Solutions Forum: Objective-based Security Drives Effective Solutions. There, Tripwire will be presenting a deeper dive into the design and implementation of a custom-fit cyber security framework in critical infrastructure environments with our partner Nexus Controls, a Baker Hughes business. Register here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

