
Sometimes the best way to inform ourselves about how cybersecurity is dealing with a new threat, technology, or situation is to just ask. COVID-19, and the resulting lockdowns, quarantines and economic changes certainly counts as a ‘situation’ for cybersecurity. While it would be nice if cybersecurity could temporarily take a backseat while people and organizations figure out how to adapt to truly new working conditions, the reality is that you can’t do things like rapidly shift to working from home, dramatically increase ecommerce over brick-and-mortar sales, and massively scale the logistics of delivery without considering how all those changes are secured along the way. Cybersecurity is part of the pandemic response, plain and simple. In order to learn more about how security professionals are dealing with this crisis, Tripwire conducted a survey. If you’re the kind of person who just wants to look at the data, you can see the results here. Many of the conclusions in these results are not surprising. For example, I don’t think anyone would be surprised to know that 94% of respondents are more concerned about security now than before COVID-19. To be fair, if you asked cybersecurity professionals if they were more concerned about cybersecurity now than this morning, you’d stand a good chance of getting a majority to say yes. After all, being concerned is part of the job description. It’s not the concern that’s interesting, but the next level down of why.
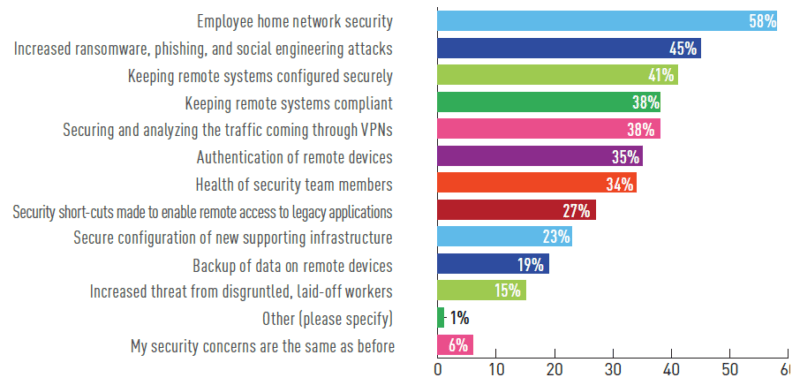
Figure 1 - What are cybersecurity professionals concerned about? It makes sense that practitioners would be concerned about employees’ home network security, but I predict this particular concern will wane over time. It’s unlikely that organizations are going to start securing those home networks. It’s much more likely that the other concerns will come to the forefront as organizations just deal with how to deploy, manage, and secure assets in an untrusted network environment. If you’re forward looking, worry less about the employees home network and more about how to gain the visibility and control you need into the corporate devices deployed anywhere outside the office. Security starts with visibility (“you can’t secure what you don’t know about”), and we wanted to know how the COVID-19 pandemic was affecting security visibility. 64% reported that security visibility is more difficult because of employees working remotely (50% somewhat more difficult, 14% much more difficult). Once again, the breakdown is important.

Figure 2 - Where do security teams have the least visibility? What’s surprising about these results is that they point out the shortcomings of solutions that were deployed for assets on the corporate network. There aren’t really any technical reasons that the same tool providing system update status or backup status shouldn’t be able to handle the same task in a more distributed network environment. Don’t get me wrong, there are lots of good, valid reasons out there, but what we’re seeing is a gap in the products deployed for these purposes. It’s especially interesting that vulnerability assessment shows up on this list at number two. If you’re using agents for vulnerability assessment, then the location of the assets matters much less. Over the past few years, agent-based VA has become a mainstream option. If, however, you’re running network-based scans, then assets moving out of the network makes them invisible. It might be time to consider an agent-based approach. Finally, we have policy compliance. There are very few people who get excited about policy compliance, and most of them are auditors. The reality is that compliance isn’t going anywhere, and while there may be some leeway in the short term for the shift to working remotely, ‘auditors gonna audit,’ as they say. A much higher percentage of respondents said that compliance is more difficult because of COVID-19.
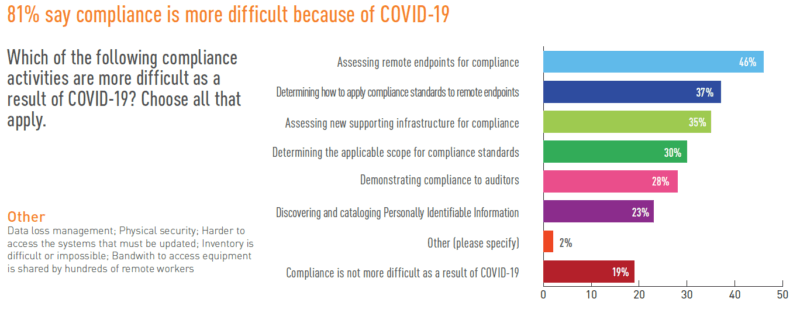
Figure 3 - Which compliance activities are more difficult? Once again, visibility into remote endpoints ranks at the top, in this case, for compliance. Interestingly, the second item is more about how to apply the policies in a new, more remote environment, rather than actual assessment. This is where expertise is more important than a tool. We also see concern for the supporting infrastructure start to show up here. The expansion to working remotely has focused a lot on the endpoints, but all the increased remote access has driven a corresponding increase in supporting infrastructure like VPNs, authentication, and other remote access technologies. They need to be secure, and compliant, as well. Finally, surveys like these often produce some contradictory results that ultimately give us insight. In this case, these two results generate some interesting lines of thought. First, we’ll return to the ‘areas of concern’ that we’ve already discussed. Note that “Increased ransomware, phishing, and social engineering attacks” ranks second at 45%. We also asked about whether employees were more susceptible to these types of attacks when working from home.
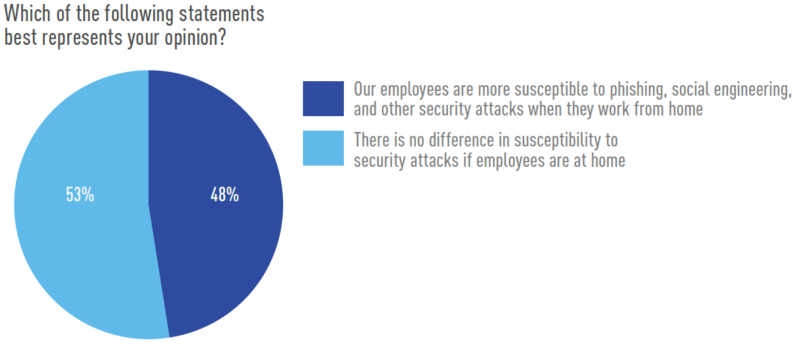
Figure 4 - Are employees now more susceptible to security attacks? Given the previous response, I would have expected a majority to say yes, employees are more susceptible working from home, but the majority (53%) actually came out on the other side. So why would security professionals be more concerned and at the same time think that employees aren’t more susceptible? The answer lies in the threat environment. The target surface, in this case employees, may not have significantly changed, but the threat environment has. COVID-19 provides a worldwide event with built-in fear and hunger for information. Those conditions are ripe for attackers to exploit through phishing and social engineering. In fact, 63% of our respondents reported having experienced some kind of COVID-19 related attack. At the end of the day, we all have to figure out how to adapt to these changing working conditions. For security professionals, the good news and the bad news is the same: security isn’t going anywhere. We don’t exactly have new problems to solve with remote working, but we do have new environments in which to continue solving the same problems: How do we deploy and maintain secure systems? How do we ensure systems are compliant? And how do we do so with fewer resources than we had yesterday?

