
Are you doing enough to prevent scammers from hijacking your social media accounts?
Even if you have chosen a strong, unique password for your online presence and enabled two-factor authentication it's possible that you've overlooked another way in which online criminals could commandeer your social media accounts and spam out a message to your followers.
That's a lesson that internet entrepreneur Carl Pei, the co-founder of smartphone firm OnePlus, has hopefully learned after cryptocurrency scammers used his Twitter account to send a fraudulent message to his 330,000 followers this week.
The fraudulent message announced Pei's new company (which is literally called "Nothing") was entering the world of cryptocurrency, and invited followers to send their Ethereum cryptocurrency to a wallet if they wanted to invest in the project.
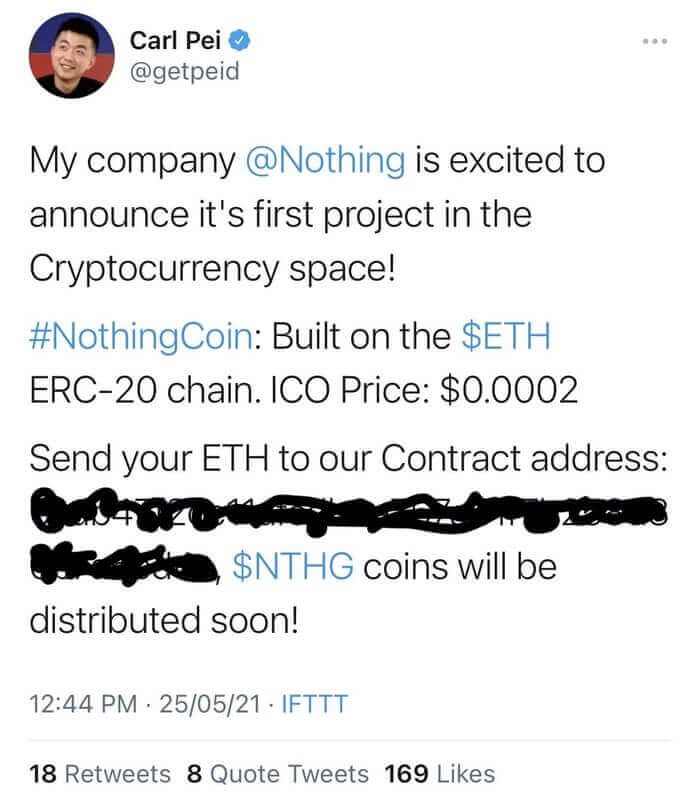
As Pei describes, hackers were able to post the message having compromised his IFTTT account:
Through permissions granted to my @IFTTT which was hacked, this Tweet was injected asking for your ETH. Please do not send any ETH or your personal info to cryptocurrency accounts claiming to be @Nothing. I’ve deleted all 3rd party apps connecting to my Twitter.
IFTTT (If This Then That) is a handy online platform that allows internet users to automate processes between a wide variety of apps, devices, and services. For instance, you could program an internet-connected bulb on your porch to light up when a pizza is about to be delivered, or automatically tweet out photographs that you post on your Instagram account if they have a certain hashtag.
Pei had connected IFTTT to his Twitter account, presumably to automate the posting of some tweets. That isn't unusual - in fact, it's something I did myself some years ago.
But it does mean that you need to connect IFTTT to your Twitter account, granting it posting permissions. And that means if your IFTTT account is compromised, or another third-party service you have linked either directly or through IFTTT to tweet out messages is hijacked, that you no longer have full control over what gets shared with your Twitter followers.
And that's why it's so important that you are careful about which third-party apps, if any, you connect to your social media accounts. Once an app is connected it doesn't matter if you change, say, your Twitter password - the third-party app still has access to your account and can take advantage of any permissions you have granted it.
Here's how you revoke a third-party app's permission to access your Twitter account:
- Go to the Apps and sessions section of your account settings. All of the apps connected to your account will be displayed. Here you can view what specific permissions each app has to use your account - some may only have read access, others may have read and write, while others may even have access to your private direct messages.
- Click the Revoke access button next to the app you wish to disconnect from your account.
But there are also steps you can take to harden your security, without revoking a particular app. For instance, it appears that it was Carl Pei's IFTTT account that was compromised. If Pei still wanted to make use of his IFTTT account in this fashion, he may wish to not only change the password associated with that account but also enable two-step verification (2SV).
Having two-factor authentication or two-step verification enabled on your online accounts adds an additional layer of security beyond relying upon passwords alone.
Personally I would recommend that everyone check the list of apps which they have connected to social media accounts like Twitter. All too often you will find that you may have left a third-party app linked to your account which you may no longer use, or no longer trust. If you don't have a good reason to keep it, or you don't recognise it, or simply don't trust it any longer, remove its rights to post on your behalf.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

