
Ask any geek and they'll tell you how fun it is to install Linux on a new machine. Whether you're trying out a new distro or installing an upgraded version, there is something cathartic about jumping on the Linux bandwagon and hacking away on a new system.
Although Linux by nature is more secure than Windows, there are still steps that need to be taken after installation to assure that you have hardened your system and prepped it for hours of fun use. Follow these steps to help harden your Linux OS. While this is not a comprehensive list, it will start you on your path to a more secure OS. This article assumes the user is familiar with running commands as root. For further assistance on any of these tips, the fastest option is to perform a web search for your particular OS; there are hundreds of community forums where the answer to your question has already likely been answered.
1) Update the OS
After you have logged into your system for the first time, updating the OS should be the first action you take. Open a terminal and, depending on the flavor of Linux you are running, run the command:
For Debian-based systems: sudo apt-get update && time sudo apt-get dist-upgrade For Red Hat-based systems: su -c 'yum update'
2) Enable the firewall
If you are running Ubuntu, the firewall is disabled by default. I highly recommend you use the graphical firewall interface ‘GUFW,’ which is an acronym for ‘Graphical Uncomplicated FireWall.’ Install GUFW by passing the terminal command: sudo apt-get install gufw After GUFW is installed, you can open it by passing the command gufw Open GUFW and turn the firewall ON by sliding the Status button to the right. For most users, the default options of Incoming: Deny and Outgoing: Allow will be sufficient, but custom rules can be easily added.
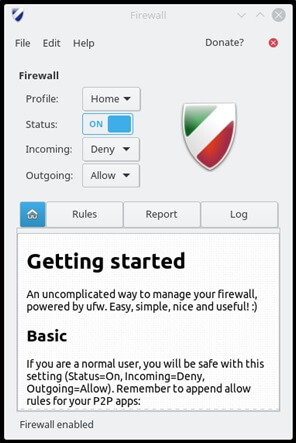
On Red Hat version 7, the firewall is enabled by default. In case you are running an older version, you can manually start the firewall on a RH system by entering the command: systemctl enable firewalld To configure the firewall and verify blocks, you can open the firewall by navigating to: System → Administration → Firewall from the panel or type: system-config-firewall at a shell prompt.
3) Install Antivirus Software
This is a hot-button issue that elicits strong opinions from both sides. Despite the fact that malware and viruses are written primarily for Windows, my opinion is that AV software only helps harden a system. Users should seize any opportunity to make a system more secure. The best free AV solution is ClamAV but there are other Linux AV products available, such as Sophos, ESET, Comodo and Bitdefender.
4) Third-Party Software
Third-party software should always be installed under the directory /opt. Help minimize your attack surface by removing unneeded programs/processes that start up automatically. The command ‘netstat -npl’ lists all the currently running services; if you can identify services you do not need, then take the steps necessary to uninstall the application(s) tied to those services. The ‘top’ command is handy for looking at what processes are eating up the most system resources, but I recommend installing and using ‘htop’ by passing the command: sudo apt-get install htop The command ‘pstree’ is another cool way of looking at processes, but instead it lays them out in a tree format.
5) Disable SSH Root Login
Disable SSH Root user access by opening the file /etc/ssh/sshd_config in your favorite text editor. Search for the line: #PermitRootLogin no Remove the pound # sign from the beginning of the line. Close the file and restart the SSH service by passing this command: /etc/init.d/sshd restart
6) Disable X Windows
If you are building a Linux file/mail/print server, there is no need to run X Window desktops like Gnome or KDE. You can increase the security and performance of a server by disabling X Windows. The following will disable X Windows by changing the run level command. Open the file: /etc/inittab Find the line that reads: id:5:initdefault: Change the line to: id:3:initdefault:
7) Disable USB ‘Thumb Drive’ Storage
If you want to make sure no one can use a thumb drive on your Linux machine, here’s an easy way to disable USB storage. Open your favorite text editor and create a new text file. Add the following line into this new text file: install usb-storage /bin/true Save the file as usb-storage.conf under the directory /etc/modprobe.d/ Reboot your machine and test the new configuration by connecting a USB thumb drive – it should fail to mount.
8) Disable CTRL-ALT-DELETE
If you are building a production server, it is a good idea to disable the Ctrl-Alt-Delete option that initiates the reboot process. In your text editor, open the file /etc/inittab Locate the line that reads: ca::ctrlaltdel:/sbin/shutdown -t3 -r now Comment the line out by prefixing it with a pound # sign at the start of the line
9) BIOS Security
Enter your BIOS configuration and disable booting from CD/DVD, USB, external & floppy drives. Enable the BIOS password and choose a strong password.
10) Audit your system
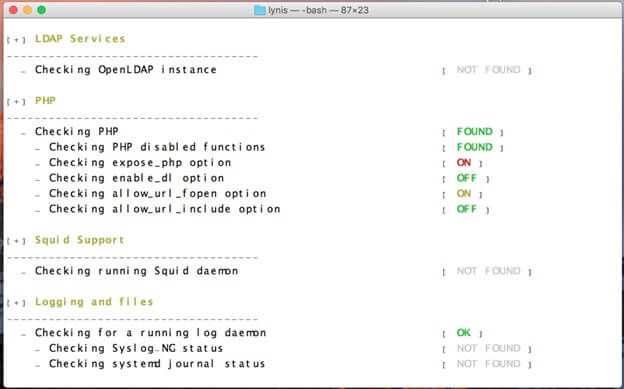
There are several free tools available to audit your system. One of them I recommend is Lynis: an open source tool that performs a local security assessment and audits local services for vulnerabilities. It is light-weight and easy to use; just unzip it and run the command ./lynis audit system
About the Author: Brian M. Thomas (@InfoSec_Brian) is a passionate professional with 17 years’ experience providing Tier-4 data solutions in all disciplines of IT including Network/Server administration and Information Security. Proven experience in HIPAA, ISO 27001 and PCI compliance. You can connect with him on LinkedIn here: https://www.linkedin.com/in/bmthomas. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

