
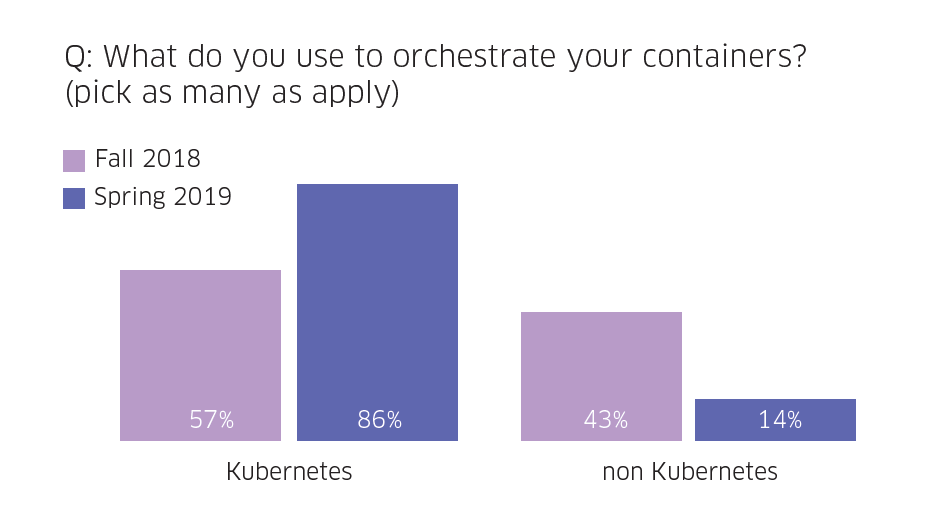
Containers have become a popular technology for enterprises that need to create agile, scalable and reliable applications. As they’re moving containerized workloads into production, many are adopting Kubernetes for container orchestration. While containerization enables DevOps to deploy software fast and efficiently, it also creates new security challenges, especially for those who’ve accelerated their implementation of this complex technology. The Kubernetes system has surged in popularity in the last few years, and the pace hasn’t stopped. Just recently, adoption grew almost 50 percent within a span of only six months, according to our recently published survey of nearly 400 IT professionals. The survey, titled “The State of Container and Kubernetes Security,” found that 86 percent of the respondents are using Kubernetes, compared to 57 percent at the end of 2018.
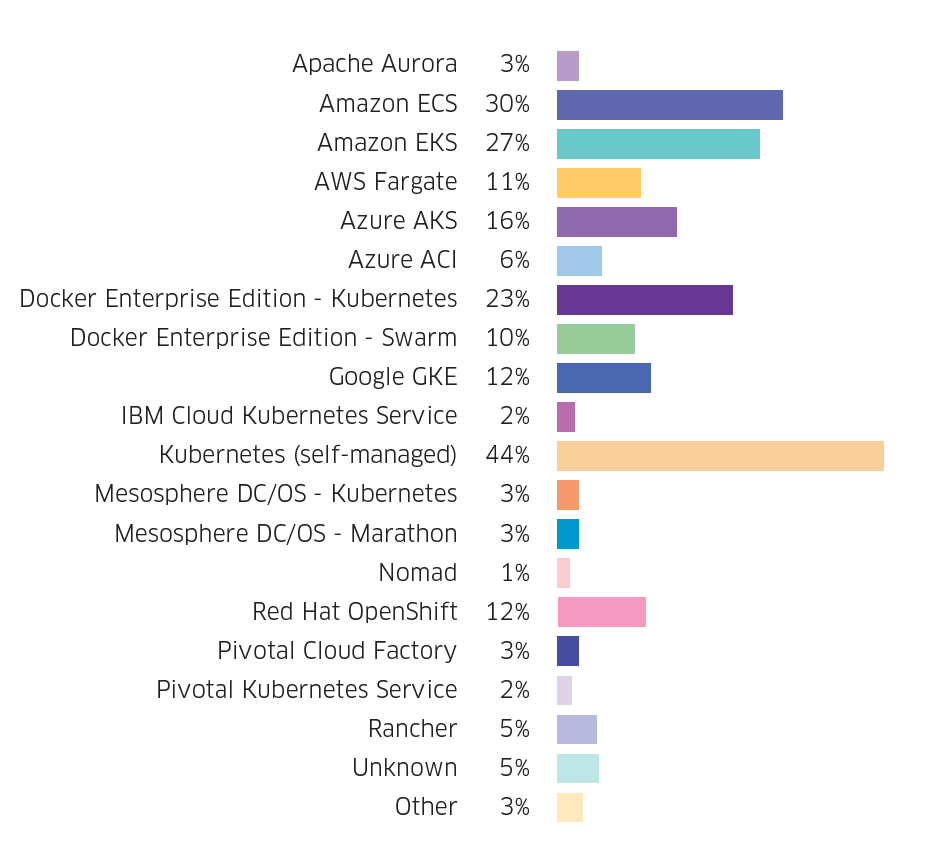
Despite the fact that every major cloud provider offers a managed Kubernetes service, a large portion of respondents self-manage their Kubernetes clusters. This is likely because it gives organizations additional flexibility to easily port their environment to a different platform.
The robust growth in Kubernetes reflects the rapid adoption of containerized applications in general. The technology has gone mainstream, and developers and engineers are finding new ways to use it. Gartner estimates that by 2022, more than 75 percent of organizations will run containerized apps in production, compared to only 30 percent today. Despite a growing maturity in many aspects of containerized workloads, however, organizations are not making equal advances in their security approaches. And now that many app developers are running containers at scale, security issues will only escalate.
Growing Security Concerns
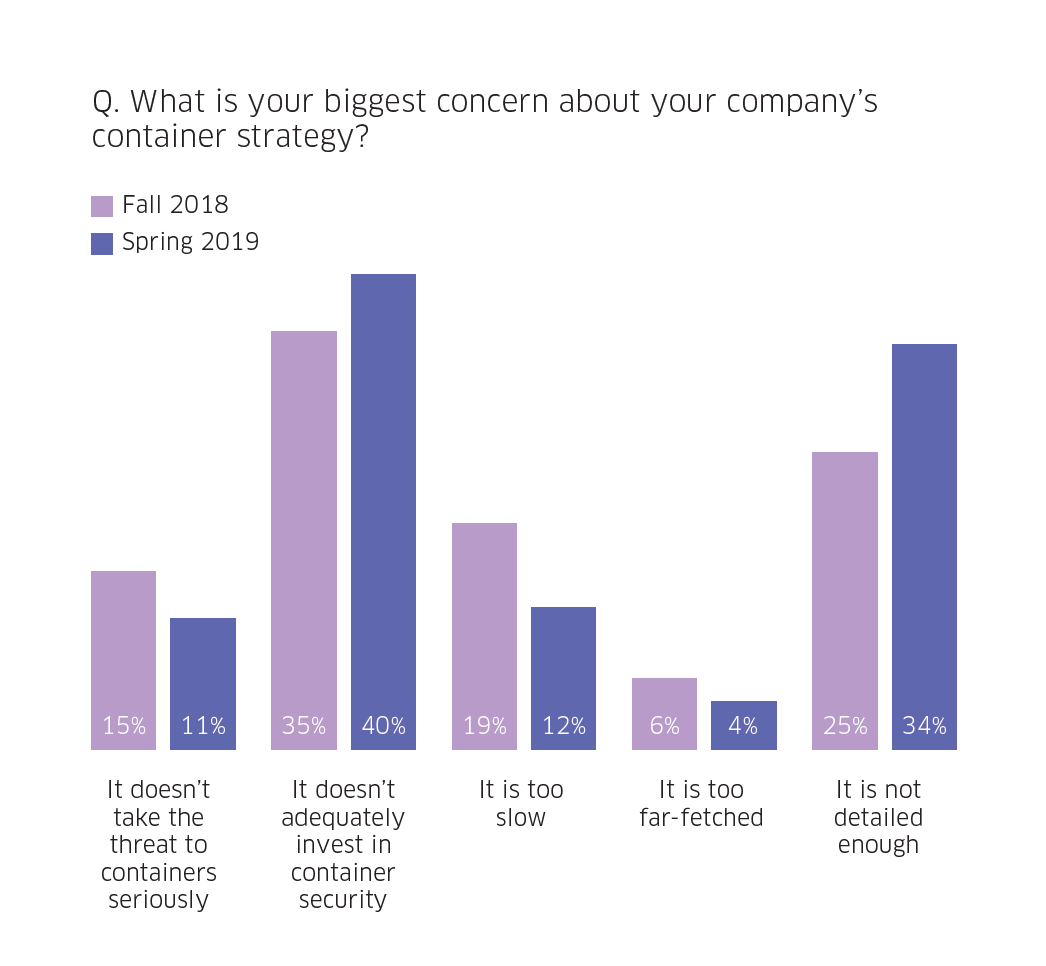
Our survey found that security has remained the top concern for IT professionals whose organizations have a container strategy. Additionally, the concern is growing—40 percent of those surveyed said their company didn’t adequately invest in container security, compared to 35 percent in a similar survey six months prior. Even more concerning is that some organizations don’t even take the security threats seriously.
Runtime, not surprisingly, maintains its lead as the life cycle stage that’s the most worrisome, while misconfigurations are seen as the biggest—and growing—risk. Runtime security is critical since threats are happening in real-time, and this has implications for the entire IT environment. For example, a container compromised by a malicious process can execute another process, like port scanning, that puts the enterprise network at risk.
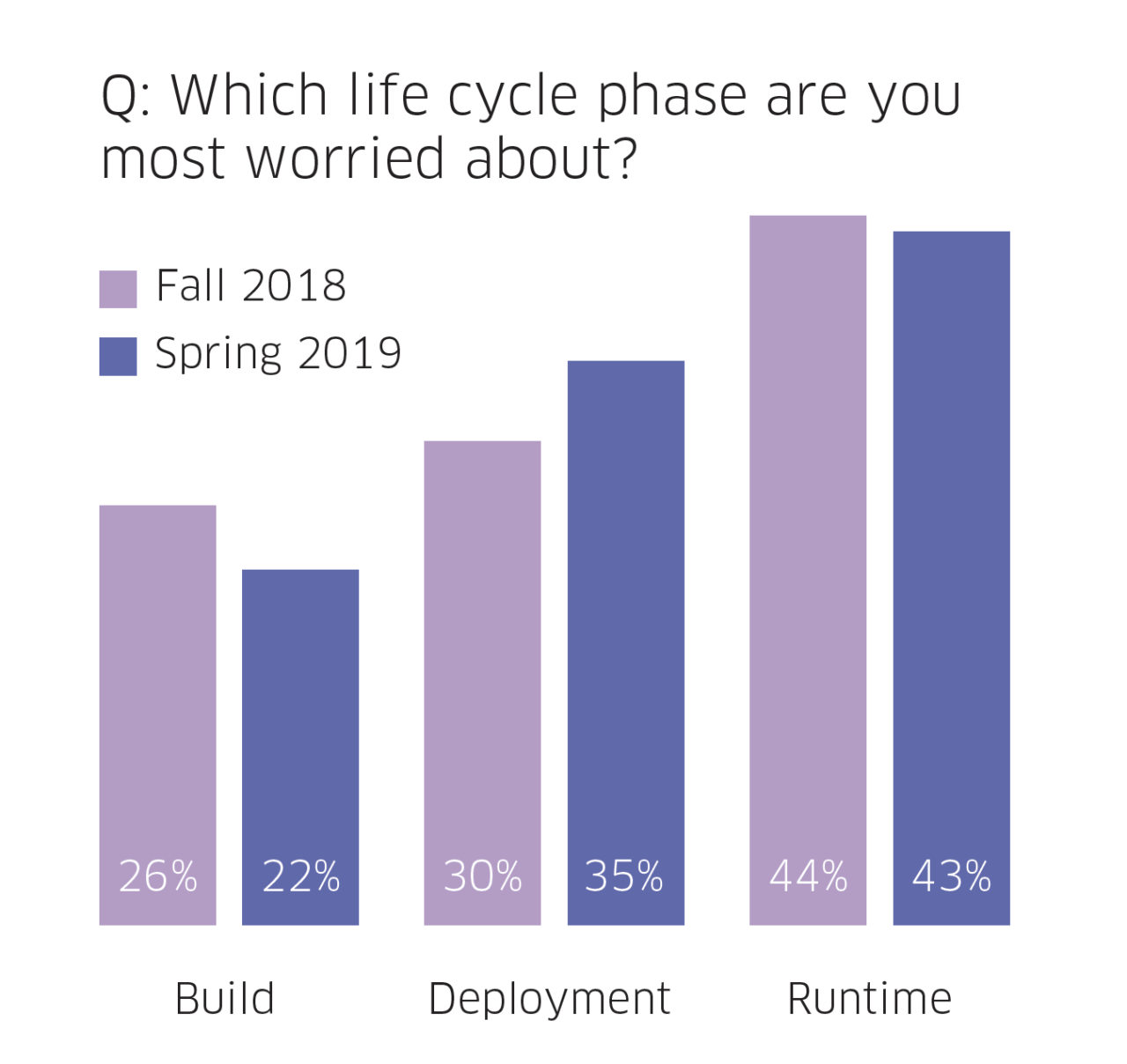
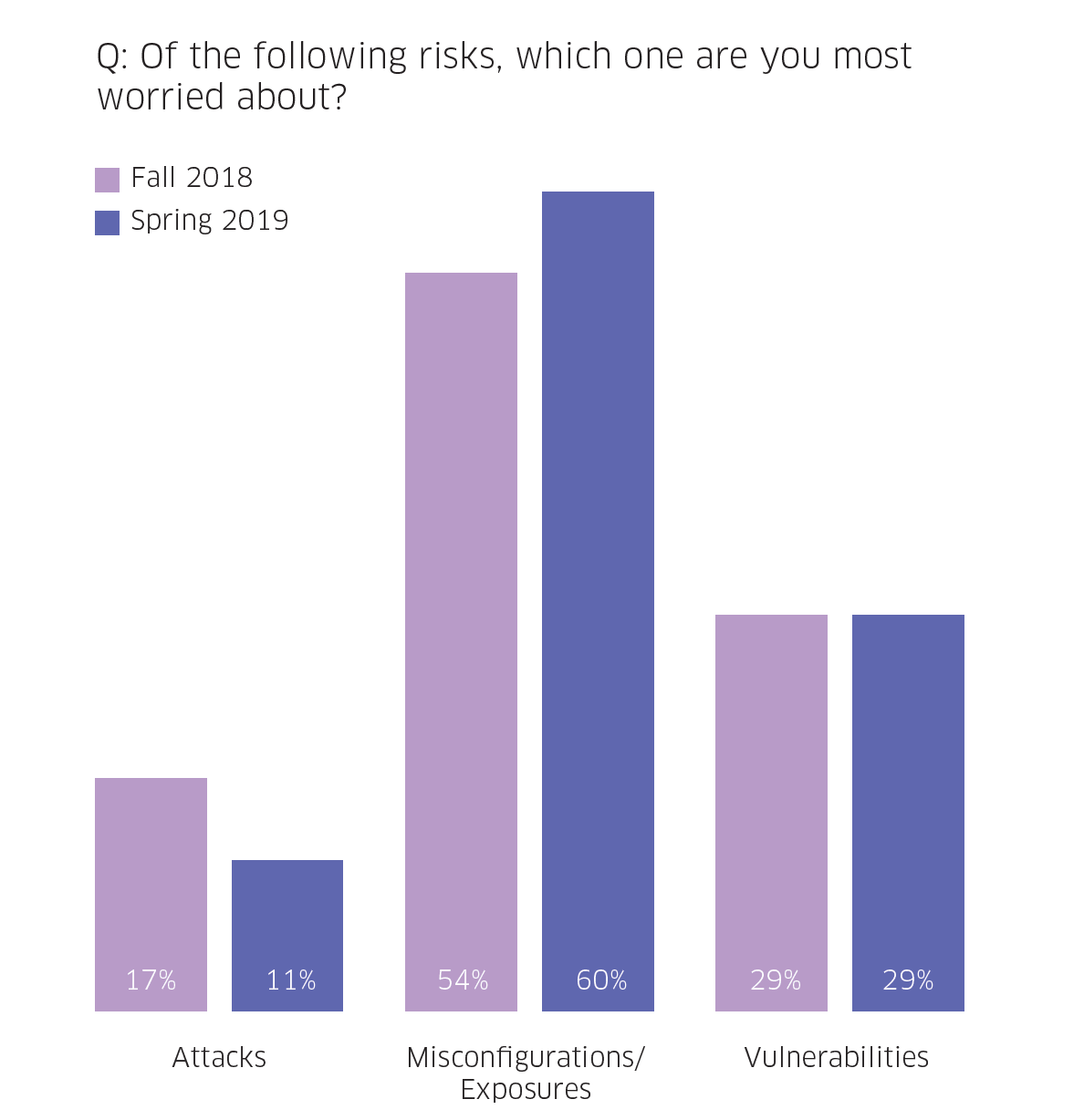
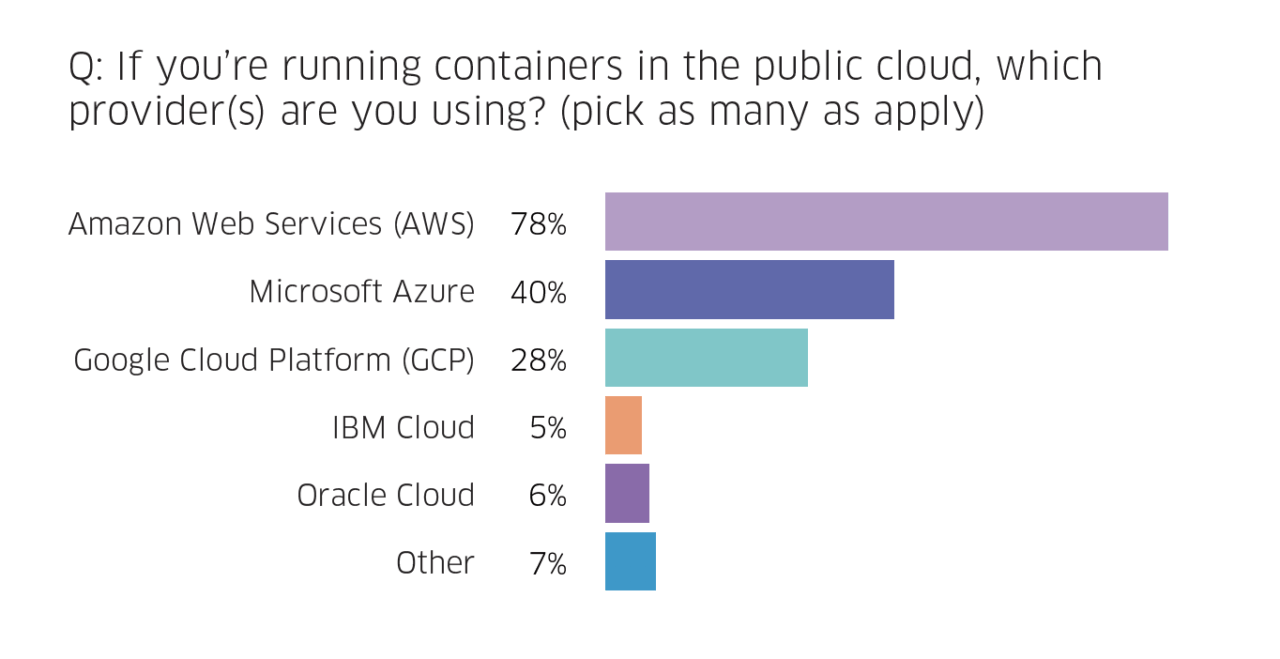
One of the many container and Kubernetes security challenges stems from the fact that containers are running everywhere—the vast majority run containers on-premises and in one or sometimes multiple clouds—which means there’s more attack surface to consider. While the hybrid model is the most prevalent, some organizations are still only running them on-prem, and others are increasingly using the cloud. To no one’s surprise, our survey found that Amazon’s AWS dominates the market, with Microsoft’s Azure a distant second. Regardless of the platform, Kubernetes is the most-commonly used orchestrator and becoming increasingly more popular.
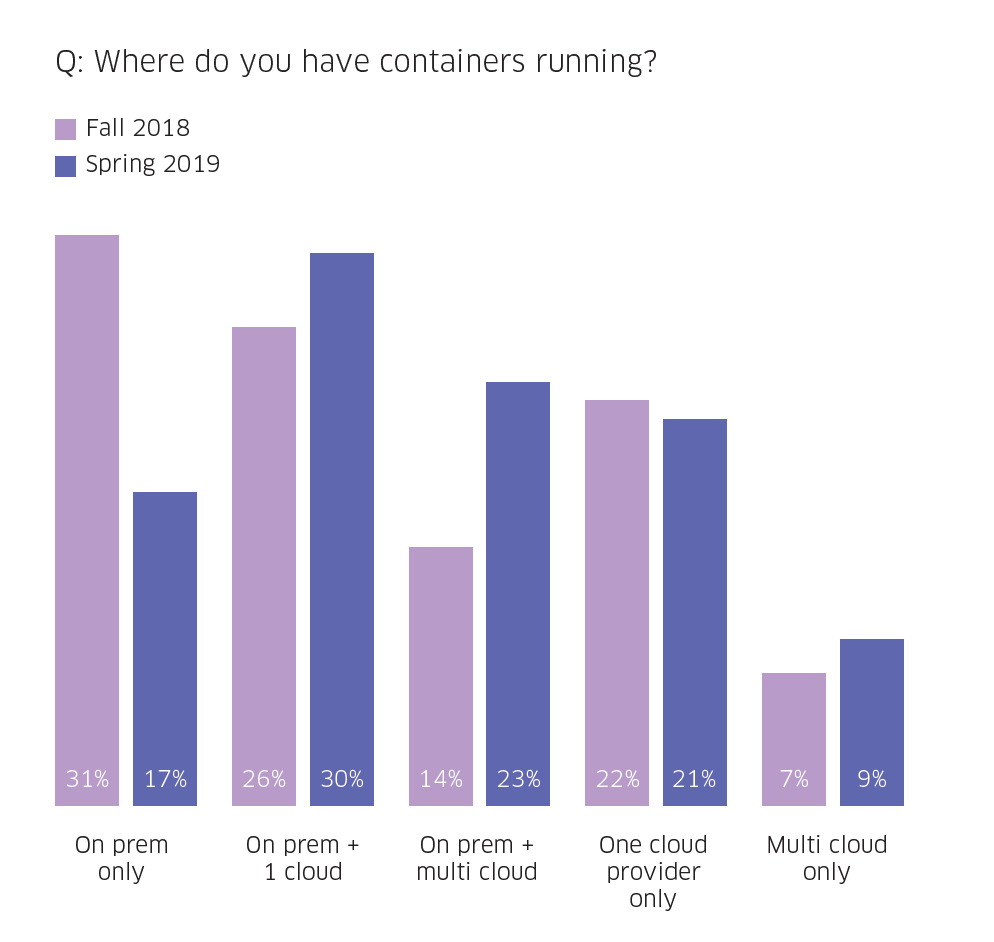
The Rise of DevSecOps
As organizations mature in their container strategy, they come to understand that security should be a priority across the entire life cycle. To move from security as an afterthought to security that’s built-in, many are implementing a DevSecOps mindset. Instead of the security team coming in at the end of the development cycle, the collaboration between DevOps and security creates a more agile environment while making security a native feature. The predominant “waterfall” style of developing and testing software before handing it off to the security team runs contrary to the DevOps approach of continuous integrations and continuous delivery. Containers can help DevOps and security to align organically by adding continuous security to the mix. The IT professionals surveyed for “The State of Container and Kubernetes Security” agree—more than 60 percent said containers increased cooperation between the DevOps and security teams.
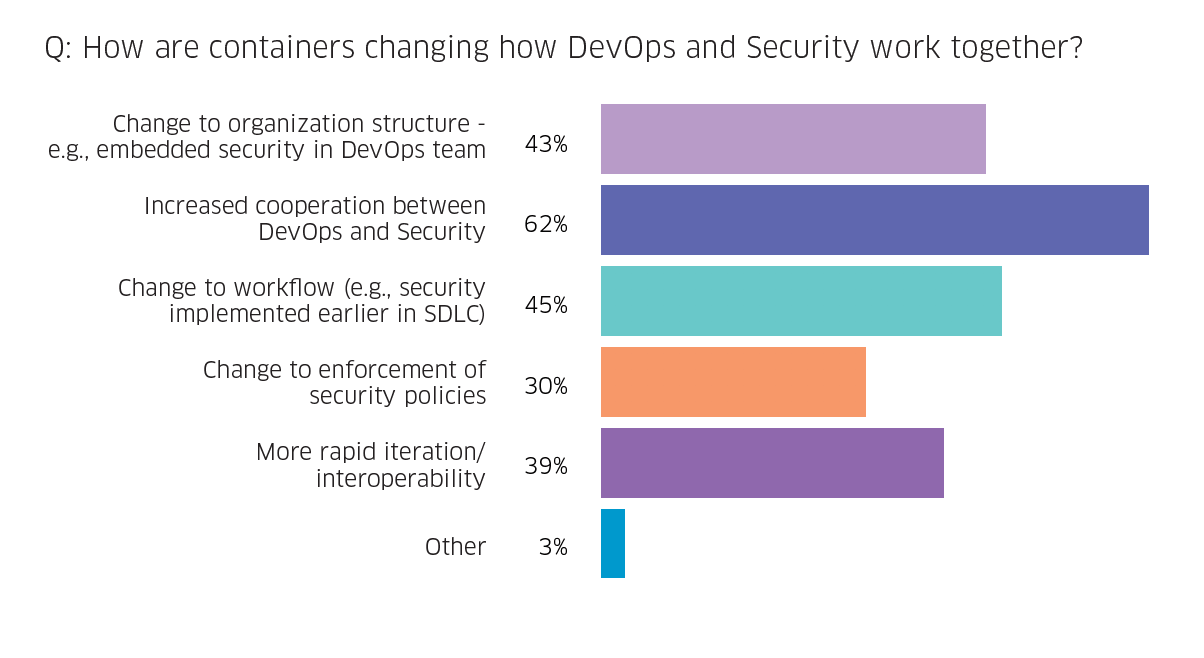
The survey also found an increase from 24 percent to 31 percent in the number of those who felt DevSecOps should be responsible for operating a container security platform. This indicates that IT professionals are recognizing the value of closer collaboration between the two sides.
Looking Ahead: A Shift in Culture
Organizations using containerized apps could greatly benefit from a DevSecOps culture because it enables them to adapt to the new, dynamic landscape. Bolted-on security simply doesn’t keep up with this environment. Just as DevOps “shifts left” to focus on quality and prevent problems rather than solving them after the fact, DevSecOps is about shifting left to add security into the code rather than adding it on top of it. Containerization is here to stay. As more enterprises move to production, their robust adoption of Kubernetes will continue. But they can’t afford to leave security as an afterthought. Like any other technology, Kubernetes is vulnerable, which means threat actors will find ways to exploit it—and we’re already seen that happen. Containers have become a solution for various app development problems, including the ability to run apps reliably when they’re moved across environments. Why, then, invite new problems by not integrating reliable security? Without including container security in the entire life cycle—build, deploy, and runtime—organizations are reducing the benefits of agility and flexibility by creating new security risks. For SecDevOps to work, organizations need security tooling, workflows and processes that bridge the two functions. This requires a conscientious investment, along with a revised strategy.
About the Author:

With a passion for building disruptive products, Ali Golshan is Co-founder and CTO for StackRox, where he oversees the company's technology strategy and roadmap. Prior to StackRox, Ali was the Founder & CTO of Cyphort (acquired by Juniper Networks) and led the company's product strategy and research initiatives Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

