What Is File Integrity Monitoring (FIM)?
File integrity monitoring is an integral cybersecurity control required by global compliance requirements like PCI DSS. Invented by the founder of Fortra's Tripwire, FIM enforces the integrity of digital systems by continuously monitoring for changes to files, operating systems, servers, endpoints, and more in real time — showing you what changed, when, and by whom, so you can stop security incidents in their tracks.
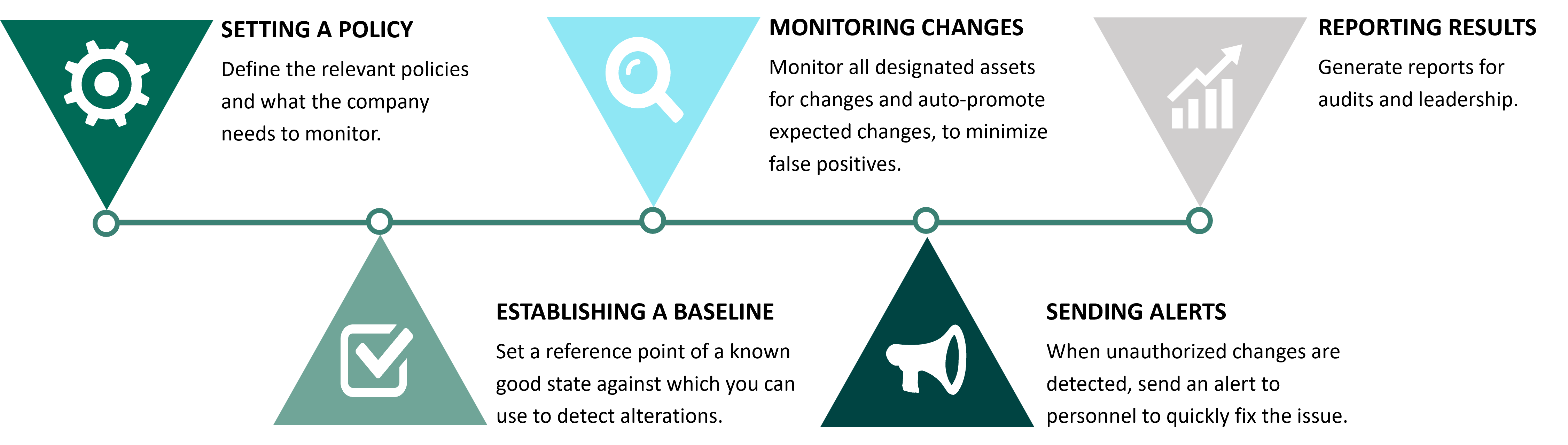
Why Is File Integrity Monitoring Important?
FIM enables you to remediate unauthorized changes, reduce overall risk, and maximize uptime.
Benefits of File Integrity Monitoring (FIM)
Detect changes in real-time
Identify exactly what changed and by whom
Determine which changes increase risk
Determine which changes result in non-compliance
Distinguish between authorized and unauthorized changes
See FIM in Action
File Integrity Monitoring Best Practices
Establish a Secure Baseline
Monitor More Than Just Files
Keep Security in Mind
Notify the Appropriate Personnel
Combine with Policy Management
Multi-Policy Coverage
File Integrity Monitoring for Operating Systems (Windows vs. Linux)
In today's world, organizations are running on a variety of different operating systems. It's imperative to find a FIM solution with the flexibility to continuously monitor the operating systems you use today with room to grow. From AIX and Amazon to VMware and Windows, enforce FIM using your choice of operating systems.
File Integrity Monitoring Compliance
File integrity monitoring is an explicit requirement of several regulatory compliance standards because of its effectiveness as a cybersecurity control for protecting sensitive data against breaches. FIM is directly required by PCI DSS, HIPAA, FISMA SI-7, and SOX, but advanced FIM solutions can automate the enforcement of all major compliance standards. Continuous, automated compliance helps organizations pass their audits and shrink their attack surface with minimal manual effort.
Scalable Protection for Complex Environments
Whether you manage your data on-premises, fully in the cloud, or in a hybrid environment wherein both are used, Tripwire solutions bridge FIM across your entire environment. As the inventors of FIM, Tripwire can provide complete visibility into every change on your network.
File Integrity Monitoring Tools
Tripwire Enterprise
Tripwire® Enterprise pairs the industry’s most respected FIM with security configuration management (SCM) to provide real-time change intelligence and threat detection. For the compliance officer, it delivers proactive system hardening and automated compliance enforcement—resulting in a reduction of audit cycles and cost.
Real-time change detection
Automated compliance
Extensive integrations
Tripwire File Integrity Manager
Tripwire® File Integrity Manager is available for those who want the power of Tripwire FIM without the other features included in Tripwire Enterprise. It uses automation to detect system changes and to remediate those that take a configuration out of policy.
Real-time change detection
“Who, what, and when” change information
Change ticketing system integration
See Tripwire FIM in Action
Organizations with visibility into system changes are more effective at catching intruders and keeping systems online. See what’s going on across your entire IT infrastructure in a single pane of glass.
Watch the on-demand demo here or schedule a personalized demo.
Featured Case Studies
Telecom Company
Learn how one global telecommunications company maintained SOX compliance and elevated its change management process with Tripwire Enterprise. Before introducing Tripwire into its environment, it was already taking advantage of ServiceNow to keep DevOps processes running at top speed. But they didn’t have an automated, reliable way to monitor change approvals and reconciliations. In addition to quickly seeing process improvements, the company can now identify application owners that aren’t following the change control process.
Electric Utility Organization
Western Farmers Electric Cooperative (WFEC) is a U.S. electric generation and transmission cooperative. Along with the need for NERC CIP compliance and FIM, WFEC needed a solution that would identify indicators of compromise and monitor for suspicious activity without causing service interruption. According to WFEC, “Tripwire is not resource-intensive the way anti-virus is. From my perspective, Tripwire does more than traditional antivirus does. It gives you more insight.”